An open letter to Godaddy: Whois Service
Quick links:
Update 2017-09-27
Update 2017-11-04
Update 2017-11-23
Update 2017-11-24
Dear Godaddy
Artists Against 419 has been champions for the consumer since 2003.
In our efforts at fighting advance fee fraud, we use various data sources to enable threat identification and mitigation. Let us be extremely clear on this issue, Artists Against 419 has no commercial ambitions. All our efforts are done with trusted volunteer assistance and self funded.
Here is the problem we are addressing: The consumer has no real champion in terms of consumer protection, when it comes to fraud on the internet internationally. Much posturing exists, sure. But ultimately it brews down to “If you have been defrauded, report it to the authorities“, or the disingenuous reply “Get a court order in a competent jurisdiction“. Or even worse: “Contact the website owner“. This is a buck passing exercise after the fact of a consumer being defrauded, not a consumer protection approach. As such Artists Against 419 was born.
In our efforts we analyze all available data pertaining to malicious events we specialize in. This may be a dying widow asking a victim to log into a certain bank. Or it may be somebody trying to sell marijuana or experimental drugs to a cancer sufferer. Or a car via a fake escrow, stealing somebody’s hard earned savings. Where we assist victims, we request they report such incidents to the authorities. Numerous reports also flows from us to the authorities in various jurisdictions upon encountering serious or linked serial abuse or like, things they may be interested in. We are a first line of defense in consumer threat mitigation. The commercial sector has numerous champions, vying for this sector of the internet where business can afford protection. Likewise governments hire experts and can address threats. However consumers at best have an antivirus solution that ill protects them from any advance fee fraud threats. One extremely common threat, much denied and disavowed, is domain based threats where a malicious actor will buy a domain, obtain hosting, then set up a fraudulent website abusing this domain name. This is why we exist. Make no mistake, despite expert claims to the contrary, domain based abuse plays a big part in human rights violations. Yet most anti-virus vendors don’t include these domains in their offerings, unless some expert mistakes a fake 419 bank for phishing. Yet strangely our virtually non-existent fake positive rating makes our data prime source for certain consumer facing portals to protect consumer class users.
We are not vigilantes. We record why we say a website and/or domain is malicious, record all attributes of such a presence, preserving this data. We do not record hacked websites. Our data was and is being used to analyze issues, cases at law enforcement. At least one officer used our data to such great effect, that he got promoted to the commercial cyber sector, thanking us for our great work.
One of these attributes collected for malicious domains is domain registration data, also called WHOIS data, for such a domain. As per ICANN agreements between Godaddy and ICANN, you are obliged to make such data available under your obligations, subject to certain conditions. These are covered in the ICANN RAA 2013, Section 3, Public Access to Data on Registered Names. While this agreement is between yourselves and ICANN, the terms evolved with much community, NGO and government input and consensus. As such you are expected to abide by these policies. The topical portions in Section 3 of the ICANN RAA says (emphasis my own):
3.3.1 At its expense, Registrar shall provide an interactive web page and a port 43 Whois service providing free public query-based access to up-to-date (i.e., updated at least daily) data concerning all active Registered Names sponsored by Registrar for each TLD in which it is accredited. The data accessible shall consist of elements that are designated from time to time according to an ICANN adopted specification or policy. Until ICANN otherwise specifies by means of an ICANN adopted specification or policy, this data shall consist of the following elements as contained in Registrar’s database: ….
3.3.5 In providing query-based public access to registration data as required by Subsections 3.3.1 and 3.3.4, Registrar shall not impose terms and conditions on use of the data provided, except as permitted by policy established by ICANN. Unless and until ICANN establishes a different policy according to Section 4, Registrar shall permit use of data it provides in response to queries for any lawful purposes except to: (a) allow, enable, or otherwise support the transmission by e-mail, telephone, or facsimile of mass, unsolicited, commercial advertising or solicitations to entities other than the data recipient’s own existing customers; or (b) enable high volume, automated, electronic processes that send queries or data to the systems of any Registry Operator or ICANN-Accredited registrar, except as reasonably necessary to register domain names or modify existing registrations.
In our case the exclusions do not apply as we are not involved in any of the abusive activities mentioned. We are fighting abuse, not propagating it. We have had much consumer acknowledgement where we stop a scammers from abusing consumers. And where it was too late, our data on fraudulent web entities allowed the consumers to realize what was happening and prevented further secondary fraud.
However, of late the Godaddy port 43 team decided they do not like certain IP addresses, blocking certain IP addresses and, instead of producing the policy mandated standard output on port 43 as also described in Section 3, the Godaddy services outputs a result such as:
Domain Name: allchemz.com
Registrar URL: http://www.godaddy.com
Registrant Name: Drake Monrue
Registrant Organization: Agro Industrial GmbH
Name Server: JESSICA.NS.CLOUDFLARE.COM
Name Server: ZOD.NS.CLOUDFLARE.COM
DNSSEC: unsignedFor complete domain details go to:
http://who.godaddy.com/whoischeck.aspx?domain=allchemz.com(Snip disclaimer and terms)
The lookup that produced this output was the first query done in many hours against Godaddy WHOIS server. While policies allow you to rate limit queries to avoid abuse etc, there is a reasonableness aspect to this. It does not allow you to block output forever more to certain IP addresses. Yet this is what you are doing. Refer https://www.icann.org/en/system/files/newsletters/update-whois-access-audit-report-port43-06apr11-en.pdf
Not only has Artists Against 419 experienced this issue, but various other parties fighting abuse. Some of the anti-abuse folks are discussing how this abusive blocking is making fighting abuse much more difficult and has been going for weeks.
Certain processes and standard have to be defined as to produce reliable predictable results. Not only does this ensure accuracy, it also enforces accountability. Using a port 43 lookup is one of these currently and must remain so until the standard changes as per ICANN policies. You do not get to decide. Using port 43, we expect a certain result, much like connecting to a website on port 80 or port 443 via a browser, and the other side answering with a response. If it was expected to answer and it does not, or incorrectly, it is broken. If you unilaterally decide to violate standards by using port 8000 as opposed to port 80 for http, or port 4445 and not port 443 for https, you would not be in business for long. It is the adherence to standards that has allowed Godaddy to grow to become the biggest registrar. Such is the nature of standards, they allow predictability, they allow planning and a better experience for all. But now you appear to be picky about which standards and protocols you adhere to, while blatantly violating others?
Also, please do not try and force any complainant to use the URL given in a port 43 lookup; http://who.godaddy.com/whoischeck.aspx?domain=…domain-name… for the following reasons:
- This URL is protected via Google Captcha. Google is particularly pedantic in terms of it’s captchas … and wrong, despite the user solving captchas correctly. There are even terms for it, Google captcha loops. Simply search for the term Google captcha issues on a search engine and uncover a history of problems, wild accusations, bugs and issues. Personally I was stuck for 9 minutes on one Google captcha session with Godaddy’s web WHOIS service. Yet it is Godaddy’s responsibility to deliver a viable service and you also do not get a free pass to pass the responsibility elsewhere. This is time that could have been better spent elsewhere.
- http://who.godaddy.com/whoischeck.aspx?domain=…domain-name… is the wrong URL. This URL delivers a result indicating if the domain is available or not, plus a lot of marketing blurb, but not domain registration details.
- The correct URL is https://www.godaddy.com/whois/results.aspx?domain=…domain-name…
- All data obtained via this interface has to be copied and pasted into the desired areas. This process is slow and tedious, also error prone.
Godaddy, you have been reasonably good at fighting abuse when made aware of it. But if your abuse team requires a good understandable report, please at least give abuse reporters the opportunity to be able to compile such reports efficiently.
On the 12th, a certain press release will be done in the USA. It will illustrate how a certain sector of the small business has been destroyed on the net due to gross abuse. Yet this is the very sector Godaddy claims to promote?
While I will not steal the thunder of this extremely credible party that spent many selfless hours researching this issue internationally, let’s look at the issues that led to the demise of this sector of the legitimate internet economy. It will also show how much due process vs abuse there is. These are the sad realities of the net, enforcement vs jurisdictional issues.
Earlier we showed trying to do a lookup on domain name allchemz.com. This domain is Godaddy sponsored. It’s registrant details, once bypassing the port 43 issues, is:
Domain Name: allchemz.com
Registry Domain ID: 2064244553_DOMAIN_COM-VRSN
Registrar WHOIS Server: whois.godaddy.com
Registrar URL: http://www.godaddy.com
Updated Date: 2016-10-07T08:13:02Z
Creation Date: 2016-10-07T08:12:59Z
Registrar Registration Expiration Date: 2017-10-07T08:12:59Z
Registrar: GoDaddy.com, LLC
Registrar IANA ID: 146
Registrar Abuse Contact Email: abuse@godaddy.com
Registrar Abuse Contact Phone: +1.4806242505
Domain Status: …
Registry Registrant ID: Not Available From Registry
Registrant Name: Drake Monrue
Registrant Organization: Agro Industrial GmbH
Registrant Street: Vogelweiderstrae 31-33
Registrant City: Wels
Registrant State/Province: Wels
Registrant Postal Code: 4600
Registrant Country: AT
Registrant Phone: +43.6886455648
Registrant Phone Ext:
Registrant Fax:
Registrant Fax Ext:
Registrant Email: drakexxxwizard@gmail.com
…
This domain is claiming to sell illegal drugs online, stating; “Our dedication to quality and scientific integrity has made us one of the most respected online shop in the US”. We find many contradictions on this website, exposing this website for what it is.
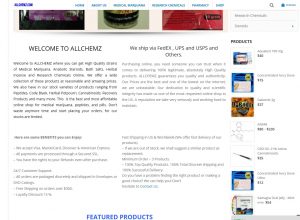
The bath salts being sold is not exactly the type you share with your loved one to relax in a bath with, rather an illegal drug well described and referenced by LegitScript and that would or should not be sold in the USA: https://www.legitscript.com/products/Bath+Salts/
So this should be a LegitScript issue, not an Artists Against 419 issue, right? Wrong!
The experimental drugs are typically marketed to people suffering from terminal cancer. Then to boot they have there credit card details stolen, never receiving the promised drugs they bought. From there they get scammed on secondary courier website scams. They typically have their privacy stolen There is no drugs, only fraud!
Your clue is in this US DEA Alert: https://www.deadiversion.usdoj.gov/pubs/pressreleases/extortion_scam.htm
The criminals call the victims (who in most cases previously purchased drugs over the internet or by telephone) and identify themselves as DEA agents or law enforcement officials from other agencies. The impersonators inform their victims that purchasing drugs over the internet or by telephone is illegal, and that enforcement action will be taken against them unless they pay a fine. In most cases, the impersonators instruct their victims to pay the “fine” via wire transfer to a designated location, usually overseas. If victims refuse to send money, the impersonators often threaten to arrest them or search their property. Some victims who purchased their drugs using a credit card also reported fraudulent use of their credit cards.
All the needed elements needed to commit this fraud and extortion, are present on the website hosted on domain allchemz.com. To understand this issue, we need to analyze this issue a bit closer. This includes WHOIS access Godaddy (hint, hint, wink, wink)! It’s telling that Godaddy has already suspend one domain for this party , docsolutioncenter.com (thank you to Godaddy Abuse team). This domain was abused to target consumers, claiming to sell real passports and fake passports, IELTS ceritifcates etc.
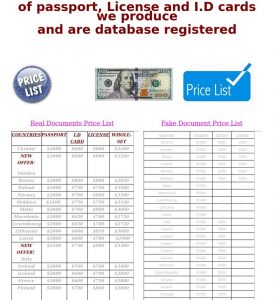
We know this because we recorded this fraud. It’s available there for you as much as for any legitimate abuse fighting member of the community, law enforcement included. It showed the same WHOIS details as allchemz.com. Meanwhile, this party suddenly changes identities and location between registrars. Domain dogbreedsales.com was terminated at another registrar for it’s involvement in pet scams. Here is the same domain owner, but who claimed to be US based:
Registrant Name: drake Monrue
Registrant Organization: gohigh ltd
Registrant Street: 12 street broadway
Registrant City: california
Registrant State/Province: Califofrnia
Registrant Postal Code: 90001
Registrant Country: US
Registrant Phone: +1.7592536619
Registrant Email: drakexxxwizard@gmail.com
Digging a bit deeper, we get a bit closer to the truth. In 2015 this party registered another domain for a drug scam as well, but now with a different name and in the Cameroon:
Domain Name: M4MED-MEGASTORE.COM
Registry Domain ID: 1971095592_DOMAIN_COM-VRSN
Registrar WHOIS Server: whois.ilovewww.com
Registrar URL: http://www.ilovewww.com
Updated Date: 2016-10-24T05:39:48Z
Creation Date: 2015-10-23T02:28:43Z
…
Registrant Name: Ngunkeng Ntem Fomenky
Registrant Organization: M4Meds-MegaStore
Registrant Street: Boulevard
Registrant City: Ebolowa
Registrant State/Province: South
Registrant Postal Code: 00237
Registrant Country: CM
Registrant Phone: +237.23777715673
…
Registrant Email: drakexxxwizard@gmail.com
Now I’m not sure how much the Godaddy abuse team knows about Cameroonian scams, but this is exactly what we’re seeing here. These very fraudsters have virtually a destroyed a certain part of legitimate commerce on the internet. There abuses ranges from consumer facing fraud to business targeting fraud, things like commodity scams claiming to sell agricultural products. Godaddy, you may wish to look at which other domains this party had before transferring one away (hint, hint again). These are all a severe threat to the legitimate internet commerce.
Sure, we can report these to the authorities after the fact, when somebody has already been defrauded. But that’s not always to say they will do something, nor is it consumer protection as explained earlier. It depends on their workload and the loss, also if the victim chooses to report it. We further need to appreciate the folks at law enforcement capable of dealing with cyber abuse are grossly overworked. As such, if we can prevent abuse rather than sit back idly watching the abuse happen and compounding law enforcement’s problems, it’s a preferred outcome.
The Godaddy port 43 WHOIS issues mentioned above are not only being experienced by the Artists Against 419 team, but also by Patrick Klos, Admin of Phishcop.net who mentioned this same issue on the Phishtank mailing list as far back as 8 Jul 2017 (snips my own since this abuse was due to hacking):
Has anyone else run across this?
It appears GoDaddy is severely limiting the data they provide in the standard (a.k.a. “command line”) WHOIS response. For example, when I use WHOIS on a hacked domain, I get this:
C:\>whois (snipped domain name)
[whois.internic.net][whois.godaddy.com]
Domain Name: (snipped domain name)
Registrar URL: http://www.godaddy.com
Registrant Name: (snip)
Registrant Organization: (snip)
Name Server: H1.CREATORY.ORG
Name Server: H2.CREATORY.ORG
DNSSEC: unsignedFor complete domain details go to:
http://who.godaddy.com/whoischeck.aspx?domain=balanceinlove.comWhen the output SHOULD LOOK LIKE THIS:
Domain Name: (snipped domain name)
Registry Domain ID: 1959459494_DOMAIN_COM-VRSN
Registrar WHOIS Server: whois.godaddy.com
Registrar URL: http://www.godaddy.com
Update Date: 2016-09-12T14:54:49Z
Creation Date: 2015-09-11T19:28:30Z
Registrar Registration Expiration Date: 2017-09-11T19:28:30Z
Registrar: GoDaddy.com, LLC
Registrar IANA ID: 146
Registrar Abuse Contact Email: abuse@godaddy.com
Registrar Abuse Contact Phone: +1.4806242505
Domain Status: clientTransferProhibited http://www.icann.org/epp#clientTransferProhibited
Domain Status: clientUpdateProhibited http://www.icann.org/epp#clientUpdateProhibited
Domain Status: clientRenewProhibited http://www.icann.org/epp#clientRenewProhibited
Domain Status: clientDeleteProhibited http://www.icann.org/epp#clientDeleteProhibited
Registry Registrant ID:
Registrant Name: (snip)
Registrant Organization: (snip)
Registrant Street: (snip)
Registrant City: (snip)
Registrant State/Province:
Registrant Postal Code: (snip)
Registrant Country: (snip)
Registrant Phone: (snip)(snip)
Name Server: H1.CREATORY.ORG
Name Server: H2.CREATORY.ORG
DNSSEC: unsigned
URL of the ICANN WHOIS Data Problem Reporting System: http://wdprs.internic.net/
>>> Last update of WHOIS database: 2017-07-07T23:00:00Z <<<Is this a new thing?? Are any other registrars doing this?? This kind of restriction is going to make processing phishing URLs take MUCH LONGER, especially if every registrar decides to do something different!
Note, Godaddy, Patrick was protecting your client! Yet you were and still denying him the ability to protect one of your legitimate clients. Yet you claim to support small business? Upon asking Patrick permission to share his post, he consented adding this:
I support the effort to making GoDaddy do the right thing! They’ll tell us we can submit a waiver request form, but that’s just kicking the can down the road. They should support proper PORT 43 WHOIS without stupid waivers! They’re helping the bad guys and making life harder for the good guys – I don’t get it.
What is this form Patrick is referring to? When this same issue originally started for Artists Against 419, we reached out to the Godaddy port 43 team. Their response was to send through a form which had to be completed, with the note:
Hello,
Please fill out the form I have attached and send it back so we can review your request.
thank you,


Let us look closer at the limitations Godaddy is placing in these usage terms:
Any use of this data for any other purpose is expressly forbidden without the prior written permission of GoDaddy.com. By submitting an inquiry, you agree to these terms of usage and limitations of warranty. In particular, you agree not to use this data to allow, enable, or otherwise make possible, dissemination or collection of this data, in part or in its entirety, for any purpose, such as the transmission of unsolicited advertising and solicitations of any kind, including spam. You further agree not to use this data to enable high volume, automated or robotic electronic processes designed to collect or compile this data for any purpose, including mining this data for your own personal or commercial purposes.
Please initial to confirm: _______Please confirm that you understand that we have the ability to shut down your access to our Port 43 if you use the service in violation of the terms or exceed your limit.
Please initial to confirm: _______
But the ICANN RAA explicitly says:
3.3.5 In providing query-based public access to registration data as required by Subsections 3.3.1 and 3.3.4, Registrar shall not impose terms and conditions on use of the data provided, except as permitted by policy established by ICANN. Unless and until ICANN establishes a different policy according to Section 4, Registrar shall permit use of data it provides in response to queries for any lawful purposes except to: (a) allow, enable, or otherwise support the transmission by e-mail, telephone, or facsimile of mass, unsolicited, commercial advertising or solicitations to entities other than the data recipient’s own existing customers; or (b) enable high volume, automated, electronic processes that send queries or data to the systems of any Registry Operator or ICANN-Accredited registrar, except as reasonably necessary to register domain names or modify existing registrations.
While the changes and differences are subtle, the limitations and implications are vast. And to boot, Godaddy is now imposing restrictions different to those as in the ICANN RAA 2013, with no policy changes implemented by ICANN that would permit them to make such changes as per the RAA.
Then as ScamPup’s admin Jason emailed the Godaddy port 43 team when the same issue was encountered on your side:
As such, for the sake of accountability, please supply me with the
number of whois lookups done from (IP address removed) in the past 24 hr
period. If such information is not forthcoming I’ll unfortunately have
to lodge an ICANN complaint, dragging in other folks in a petition
style complaint to ICANN compliance, cc’ed to SSAC and the APWG.I put it to you that you are enabling maliciousness by hampering the
ability to to allow a reasonable number of whois lookups. If you do
not want people to do so many lookups against you while investigating
malicious domain abuse, rather look at ways to make many such lookups
avoidable by stopping abuse, but don’t punish the very parties trying
to undo the mess. You are now doing more harm than good.
Ironically this was the same sentiments expressed by Patrick of Phishcop.net. When you replied to him, sending him the same form you sent us, yet not divulging the number of requests made, he replied (IP addresses and AS numbers removed):
This is not what was requested.
I wanted to know how many whois lookups were done from (IP address removed) in the past 24 hrs that made you decide to limit access for the reasons stated in the email to you, that you yourself include?
I’m putting it to you your rate limiting is either over zealous or broken.
As for filling in the form, what guarantee do I have that this information will not be disclosed. What purpose will it serve? You are asking me to sign a blank check. As for IP addresses I use, working on a dynamic IP, the range would be anything on ASXXXXX which is anything my provider decides to allocate in their current 19.9 million IP addresses range. And if my copper fixed wire connection is down or while traveling, I use wireless via ASXXXX which has over 20 million IP addresses. So obviously this does not fit into the token template reply and solution.
The email from Jason to the Port 43 team shows clearly he was asking the number of requests done. Then we have other groups as well that see the same issues, groups like ScamSurvivors whose sole goal is to assist victims to fraud by linking the dots for those victims, assisting them with facts to complain to the authorities. There are more such groups …
Godaddy, on the 12th or 13th I will be posting here again. It is due to unilateral deliberate policy violations that a certain segment of the legitimate commerce on the internet was destroyed. I will then show why and how primarily three registrars contributed to this issue. While you were not part of this abusive and corrosive process that spanned slightly more than a year in the USA, you could easily become one of the factors in the next step of undermining trust on the net. That would undermine all the marketing your CEO has done, also destroy the hard work to stem the tide of abuse everybody seems so quick to disavow any responsibility for. Do not be THAT one!
I ask you now, do you know who your sincere friends are, those who are looking out for consumers on the net, not asking for reward or acknowledgement, even protecting your legitimate clients while assisting your abuse team pointing out those deliberately abusing you and your terms? Partnering with them can assist you in making the net a bit safer for ordinary consumers, prevent yourselves to become conduits for fraud. Consider these groups are your early alert friends. The are not asking for reward, rather you not simply disrespect them. They are experts in their respective fields that are even teaching and assisting the authorities. That is how much of the net operates and stays safe.
At this stage we are looking at how to best resolve this issue you are causing for certain sectors of the security community. As the largest registrar, you’ve had some issues from time to time. Yet you’ve always fixed them, either directly or after complaints. We have tried alerting your abuse team when needed and they have been great in general. Where we compiled stats to point out the most abused registrars, even commented on the great work your abuse team were doing, they deserved it!
We ask you now do the right thing and not allow this issue to undermine all the hard work done by your other teams.
Sincerely,
Derek
On behalf of the anti-abuse community.
Update: This issue also affect domain registered via Wild West Domains, LLC for obvious reasons.
Domain Name: kibestinsurance.com
Registrar URL: http://www.wildwestdomains.com
Registrant Name: Registration Private
Registrant Organization: Domains By Proxy, LLC
Name Server: DNS1.FREEHOSTIA.COM
Name Server: DNS2.FREEHOSTIA.COM
DNSSEC: unsignedFor complete domain details go to:
http://who.securepaynet.net/whoischeck.aspx?domain=kibestinsurance.com&prog_id=418222The data contained in this Registrar’s Whois database,
In this case we have a domain being used for financial scams, targeting small business:
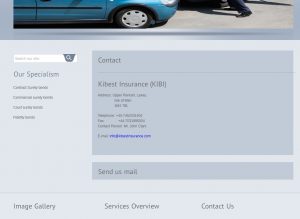
Despite claiming to be UK based, this company is not registered in the United Kingdom.
The URL so kindly supplied by Wild West Domains for an online request of the registration details, does not work:
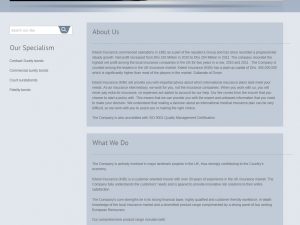
This bogus company describes itself as such:
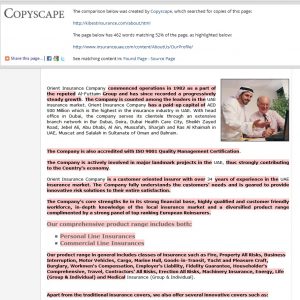
Much content stolen from a legitimate longstanding Godaddy client in the UAE! We can most easily see this by comparing the content in CopyScape:
And just for fun: The real registration details are hidden via DomainsByProxy, LLC.
Registrant Name: Registration Private
Registrant Organization: Domains By Proxy, LLC
Registrant Street: DomainsByProxy.com
Registrant Street: 14455 N. Hayden Road
Registrant City: Scottsdale
Registrant State/Province: Arizona
Registrant Postal Code: 85260
Registrant Country: US
Registrant Phone: +1.4806242599
Registrant Phone Ext:
Registrant Fax: +1.4806242598
Registrant Fax Ext:
Registrant Email: kibestinsurance.com@domainsbyproxy.com
Once again this just reflects why it is important to be able to research maliciousness on the net, be it a scam email, or something more like this fictitious company hosted on free hosting that actually was targeting somebody and why we took a closer look.
Update 2017-09-27
The release of the mentioned report above was delayed, but was released yesterday and can be found at https://www.bbb.org/puppyscamstudy/.
This excellent piece of research by BBB director Steve Baker looks at pet scams, how these have become a massive threat to anybody purchasing a pet on the web. In essence, this pet sales segment of the web has been trashed. The consumer has a much better change of getting defrauded than being able to find a real pet on the web. This has a knock on effect. Credit card details are trivially stolen in these. Though not much known, is how Asian Arowana are used in pet scams to set up American consumers for extortion by fake government officials; Asian Arowana are CITES protected species and prohibitions against import and selling of Asian Arowana exists. This is all part and parcel of this consumer facing threat.
While this is a consumer facing article, the reality is that in the background this only touches the merest tip of a massive iceberg, a specific iceberg threatening consumers and businesses alike and ill understood by most authorities. This was also the specific reason that that docsolutioncenter.com and allchemz.com was mentioned. Welcome to Cameroonian Scams. Although also from West Africa, these are not 419 scams, they are totally different in nature and execution affecting and treating each and every part of legitimate commerce.
Each of these threats starts of with the malicious party registering a domain. Much of the escalation and mitigation done thus far have relied on the ability to do proper research. The results of such research makes it’s way into the hands of the authorities and other parties that can take these matters further to ensure due process. But by this stage we are typically past the point of consumer protection, rather seeking justice for victims to cyber crimes from the authorities. Anybody that has been following consumer facing cyber crime will know that justice is hard to find for consumers and, for the bulk, the perpetrators go unpunished.
It’s easy for the world biggest registrar Godaddy to distance themselves from the reality that it’s not always law enforcement that raises the red flags on such issues, while rather trying to absolve themselves from any responsibility, yet frustrating law and policy abiding security researchers by not abiding to the policies as above. Meanwhile they themselves sell domains to these malicious parties mentioned in this report, allowing the targeting of consumers (and businesses as deliberately pointed out in this blog above originally – that iceberg) worldwide, even their own fellow countrymen, perhaps even the family members of their own staff! Even the very business they themselves claim to be the champion for.
It’s through a failure to abide by and gaming of agreed upon and accepted policies such as the ICANN RAA, that we finally arrived at a point that we can say a part of the legitimate internet has already been trashed. Godaddy, although not a major contributor, has most certainly also contributed to this issue. We further need to note that this is just one such threat facing consumers and business, while there are many more. Likewise there are many more groups trying to avert these different disasters, legitimate efforts not in violation of any policies that Godaddy is frustrating by violating policy, while undermining the credibility of the legitimate internet, perhaps even slowly destroying it.
Update 2017-11-04
Since the previous update on 2016-09-27 a lot has happened, but also not much. Let us explain …
ICANN Ticket RTN-088-27208.
A complaint was lodged with ICANN on 6 Oct 2017. The message has to be brief since ICANN Compliance insists on web forms. In this case the form only allows for 2000 characters so obviously the complaint cannot be detailed (Certain bits of information passed on to ICANN have been redacted for publication to prevent abuse).
Godaddy is violating the ICANN RAA.
Full details at https://blog.aa419.org/2017/09/08/an-open-letter-to-godaddy-whois-service/
There are imposing terms beyond that as in the ICANN RAA which they are not allowed to do.
This issue is long-standing and undermines not only the credibility of the ICANN RAA, the are hampering legal IT Security efforts to mitigate abuse.
Godaddy’s Port 43 team, ceo@godaddy.com and legal@godaddy.com has been made aware of this issue.
AA419’s view is made clear in the blog post.
While it’s trivially easy bypassing this issue, this should not be needed. As (redacted) says, discussing this issue on Phishtank:
——– Forwarded Message ——–
Subject: Re: [users] GoDaddy limiting their WHOIS records?!?
Date: Mon, 18 Sep 2017 12:43:56 +0100
From: (redacted)
Reply-To: users
To: users….
GoDaddy have been doing this for simply ages …
… it was an issue that I had to overcome back in early 2013 when I was
collecting data for an ICANN Whois study.—
(redacted)——– Forwarded Message ——–
Subject: Re: [users] GoDaddy limiting their WHOIS records?!?
Date: Fri, 15 Sep 2017 08:53:15 -0400
From: (redacted)
To: users> That’s part of the problem. People try it and see it works for them
> without understanding that GoDaddy (and possibly others) are
> creating _per-IP-address restrictions_ in their WHOIS servers.Has anyone (else) filed a complaint with ICANN about this? How did
you make out?I gotten responses indicating ICANN would like to ignore or sidestep
the issue if at all possible. …etc
This complaint was lodged in the correct form at ICANN Compliance as ““. Since ICANN Compliance insists on an example domain, but then tries twisting these policy issues into issues about the example domain (lessons learnt), domain godaddy.com was used as an example to bypass any such attempt.
Eventually, 11 days later on 17 Oct 2017, a reply was received from ICANN Compliance:
Thank you for submitting a Whois Format complaint concerning the
registrar name GoDaddy.com, LLC.Although your complaint is invalid for the complaint type selected, it
may be able to be processed as a Whois Unavailable complaint. To make
that determination, ICANN is requesting additional information.Please note that the corresponding registrar’s current Whois Port 43
and web-based Whois service are operational.However, if you are encountering a Whois service problem for a
specific domain name Whois query, please provide ICANN the following
information by 24 October 2017:– Provide an appropriate evidence such as screenshots and/or
time-stamped system logs at the time you have queried the Whois data
for the reported domain name, and failed to receive a Whois result.Please send the information and records requested above via reply
email (no more than 4 MB total) and do not change the email subject
heading. Please provide records as attachments in .TXT, .PDF, or
.DOC(X) format.If you do not provide this information before 24 October 2017, ICANN
will close your complaint.Sincerely,
ICANN Contractual Compliance
############################################
The problem summary
(snip … message shown above)
The whois at the time of processing is:
REGISTRAR WHOIS:
Domain Name: GODADDY.COM
Registry Domain ID: 4013247_DOMAIN_COM-VRSN
Registrar WHOIS Server: whois.godaddy.com
Registrar URL: http://www.godaddy.com
Updated Date: 2013-06-02T12:16:24Z
Creation Date: 1999-03-02T05:00:00Z
Registrar Registration Expiration Date: 2021-11-01T11:59:59Z
Registrar: GoDaddy.com, LLC
Registrar IANA ID: 146
Registrar Abuse Contact Email: abuse <at> godaddy.com
<mailto:abuse <at> godaddy.com>
Registrar Abuse Contact Phone: +1.4806242505
Domain Status: clientTransferProhibited
http://www.icann.org/epp#clientTransferProhibited
Domain Status: clientUpdateProhibited
http://www.icann.org/epp#clientUpdateProhibited
Domain Status: clientRenewProhibited
http://www.icann.org/epp#clientRenewProhibited
Domain Status: clientDeleteProhibited
http://www.icann.org/epp#clientDeleteProhibited
Registry Registrant ID: Not Available From Registry
Registrant Name: Domain Administrator
Registrant Organization: Go Daddy Operating Company, LLC
Registrant Street: 14455 N Hayden Rd Suite 219
Registrant City: Scottsdale
Registrant State/Province: Arizona
Registrant Postal Code: 85260
Registrant Country: US
Registrant Phone: +1.4805058800
Registrant Phone Ext:
Registrant Fax: +1.4805058844
Registrant Fax Ext:
Registrant Email: companynames <at> godaddy.com
<mailto:companynames@godaddy.com>
Registry Admin ID: Not Available From Registry
Admin Name: Domain Administrator
Admin Organization: Go Daddy Operating Company, LLC
Admin Street: 14455 N Hayden Rd Suite 219
Admin City: Scottsdale
Admin State/Province: Arizona
Admin Postal Code: 85260
Admin Country: US
Admin Phone: +1.4805058800
Admin Phone Ext:
Admin Fax: +1.4805058844
Admin Fax Ext:
Admin Email: companynames <at> godaddy.com <mailto:companynames <at> godaddy.com>
Registry Tech ID: Not Available From Registry
Tech Name: Domain Administrator
Tech Organization: Go Daddy Operating Company, LLC
Tech Street: 14455 N Hayden Rd Suite 219
Tech City: Scottsdale
Tech State/Province: Arizona
Tech Postal Code: 85260
Tech Country: US
Tech Phone: +1.4805058800
Tech Phone Ext:
Tech Fax: +1.4805058844
Tech Fax Ext:
Tech Email: companynames <at> godaddy.com <mailto:companynames <at> godaddy.com>
Name Server: CNS1.GODADDY.COM
Name Server: CNS2.GODADDY.COM
Name Server: CNS3.GODADDY.COM
Name Server: A11-64.AKAM.NET
Name Server: A1-245.AKAM.NET
Name Server: A20-65.AKAM.NET
Name Server: A6-66.AKAM.NET
Name Server: A8-67.AKAM.NET
Name Server: A9-67.AKAM.NET
DNSSEC: unsigned
URL of the ICANN WHOIS Data Problem Reporting System:
http://wdprs.internic.net/
>>> Last update of WHOIS database: 2017-10-06T20:00:00Z <<<For more information on Whois status codes, please visit
https://www.icann.org/resources/pages/epp-status-codes-2014-06-16-enThe data contained in GoDaddy.com, LLC’s WhoIs database,
while believed by the company to be reliable, is provided “as is”
with no guarantee or warranties regarding its accuracy. This
information is provided for the sole purpose of assisting you
in obtaining information about domain name registration records.
Any use of this data for any other purpose is expressly forbidden without
the prior written
permission of GoDaddy.com, LLC. By submitting an inquiry,
you agree to these terms of usage and limitations of warranty. In
particular,
you agree not to use this data to allow, enable, or otherwise make
possible,
dissemination or collection of this data, in part or in its entirety, for
any
purpose, such as the transmission of unsolicited advertising and
and solicitations of any kind, including spam. You further agree
not to use this data to enable high volume, automated or robotic
electronic
processes designed to collect or compile this data for any purpose,
including mining this data for your own personal or commercial purposes.Please note: the registrant of the domain name is specified
in the “registrant” section. In most cases, GoDaddy.com, LLC
is not the registrant of domain names listed in this database.REGISTRY WHOIS:
Domain Name: GODADDY.COM
Registry Domain ID: 4013247_DOMAIN_COM-VRSN
Registrar WHOIS Server: whois.godaddy.com
Registrar URL: http://www.godaddy.com
Updated Date: 2014-04-09T04:15:36Z
Creation Date: 1999-03-02T05:00:00Z
Registry Expiry Date: 2021-11-01T11:59:59Z
Registrar: GoDaddy.com, LLC
Registrar IANA ID: 146
Registrar Abuse Contact Email: abuse <at> godaddy.com
<mailto:abuse <at> godaddy.com>
Registrar Abuse Contact Phone: 480-624-2505
Domain Status: clientDeleteProhibited
https://icann.org/epp#clientDeleteProhibited
Domain Status: clientRenewProhibited
https://icann.org/epp#clientRenewProhibited
Domain Status: clientTransferProhibited
https://icann.org/epp#clientTransferProhibited
Domain Status: clientUpdateProhibited
https://icann.org/epp#clientUpdateProhibited
Domain Status: serverDeleteProhibited
https://icann.org/epp#serverDeleteProhibited
Domain Status: serverTransferProhibited
https://icann.org/epp#serverTransferProhibited
Domain Status: serverUpdateProhibited
https://icann.org/epp#serverUpdateProhibited
Name Server: A1-245.AKAM.NET
Name Server: A11-64.AKAM.NET
Name Server: A20-65.AKAM.NET
Name Server: A6-66.AKAM.NET
Name Server: A8-67.AKAM.NET
Name Server: A9-67.AKAM.NET
Name Server: CNS1.GODADDY.COM
Name Server: CNS2.GODADDY.COM
Name Server: CNS3.GODADDY.COM
DNSSEC: unsigned
URL of the ICANN Whois Inaccuracy Complaint Form:
https://www.icann.org/wicf/For more information on Whois status codes, please visit
https://icann.org/eppRegistrar: GoDaddy.com, LLC
Whois Server: whois.godaddy.com############################################
The attempt at making out this complaint to be potentially invalid is rather ingenious and it is not the first time ICANN Compliance has done so. As shared on PhishTank by another anti-abuse group administrator:
I gotten responses indicating ICANN would like to ignore or sidestep the issue if at all possible. First they try to tell me GoDaddy’s WHOIS is working fine. Then they imply that I used the wrong tickbox to file the complaint (I clicked on “Registrar does not meet Whois Service Level Agreement (SLA) requirements” because that’s what’s happening). They continue by telling me “Please note that the corresponding registrar’s current Whois Port 43 and web-based Whois service are operational.”, all the while ignoring my repeated claims that the results are dependent upon the source IP address of the request!
Please tell me others are trying to get ICANN’s attention about this as well?
As such our reply 18 Oct 2017:
Hello ICANN Compliance
Thank you for reverting.
cc: (redacted), ICANN SSAC: Issue of Security Community interest
Note: Everything said here in terms of Godaddy applies equally to Wild West Domains as their Port 43 Whois service does exactly the same.
This is in fact a “Whois Format complaint“, not a “Whois Unavailable” complaint, and the correct form was used.
Godaddy selectively intercepts certain IP addresses, substituting the Whois details under certain circumstances with a lesser format such as:
> $ whois godaddy.com -h whois.godaddy.com
> Domain Name: GODADDY.COM
> Registrar URL: http://www.godaddy.com
> Registrant Name: Domain Administrator
> Registrant Organization: Go Daddy Operating Company, LLC
> Name Server: CNS1.GODADDY.COM
> Name Server: CNS2.GODADDY.COM
> Name Server: CNS3.GODADDY.COM
> Name Server: A11-64.AKAM.NET
> Name Server: A1-245.AKAM.NET
> Name Server: A20-65.AKAM.NET
> Name Server: A6-66.AKAM.NET
> Name Server: A8-67.AKAM.NET
> Name Server: A9-67.AKAM.NET
> DNSSEC: unsigned
>
> For complete domain details go to:
> http://who.godaddy.com/whoischeck.aspx?domain=GODADDY.COM
>
> The data contained in GoDaddy.com, LLC’s WhoIs database,
> while believed by the company to be reliable, is provided “as is”
> with no guarantee or warranties regarding its accuracy. This
> information is provided for the sole purpose of assisting you
> in obtaining information about domain name registration records.
> Any use of this data for any other purpose is expressly forbidden without the prior written
> permission of GoDaddy.com, LLC. By submitting an inquiry,
> you agree to these terms of usage and limitations of warranty. In particular,
> you agree not to use this data to allow, enable, or otherwise make possible,
> dissemination or collection of this data, in part or in its entirety, for any
> purpose, such as the transmission of unsolicited advertising and
> and solicitations of any kind, including spam. You further agree
> not to use this data to enable high volume, automated or robotic electronic
> processes designed to collect or compile this data for any purpose,
> including mining this data for your own personal or commercial purposes.
>
> Please note: the registrant of the domain name is specified
> in the “registrant” section. In most cases, GoDaddy.com, LLC
> is not the registrant of domain names listed in this database.As such, the Whois service on port 43 is available, but not outputting the expected format. This equally applies all Godaddy registered domains and is not domain specific to a specific Godaddy sponsored domain.
Godaddy is doing this with any party doing more than about 10 Whois lookups, even if not in rapid succession, then blocking such IP for many hours with the alternate output format (about a day), unless specifically whitelisted. The above example result was obtained by checking malicious domains in our database until the format substitution occurred, then querying domain godaddy.com against their own service.
As such you are correct that Port 43 is operational, and is also why this is not a “Whois Unavailable” complaint:
> Please note that the corresponding registrar’s current Whois Port 43 and web-based Whois service are operational.
But that does not mean it keeps on being functional, nor gives the correct format – unless you are whitelisted.
The web-based Whois service is not topical and was never the subject of the complaint. Such usage is Google Captcha protected (which even frustrated a researcher), rendering it not fit for purpose. The RAA does not say a registrar shall have either one or the other, it specifically says both.
The result is based upon IP address as decided by Godaddy’s programmatic whitelisting/blacklisting system.
Artists Against 419 made Godaddy’s Port 43 team (port43 <at > godaddy.com). The response was to set terms beyond and above what ICANN sets, a violation of the ICANN RAA by sending a form that had to be completed for access.
Email reply with details sent included in attachment: Incident_32960564.pdf (The IP addresses mentioned is privileged information as it includes (redacted) network specific information)
Attachment Fakesite_126613.pdf was included in the original email to Godaddy and is attached here to – showing exactly what and how such information is topical and why it’s needed as a data-set showing actionable harm. As such there was and is total transparency.
Form to be completed included with additional terms beyond that of the RAA 2013: Port43AccessRequestForm.pdf
This resulted in the blog post at https://blog.aa419.org/2017/09/08/an-open-letter-to-godaddy-whois-service/ (included as An_open_letter_to_Godaddy.pdf )
Godaddy’s CEO, Legal team and the port 43 team was made aware of this blog in a single email, illustrating the harmful affect their actions are having, while not being in line with the RAA as pointed out.
> ——– Forwarded Message ——–
> Subject: Re: Update [Incident ID: 32960564] – whois look-up failing partially
> Date: Sat, 9 Sep 2017 01:56:39 +0200
> From: (redacted)
> Reply-To: (redacted)
> Organization: aa419.org
> To: (redacted)
> CC: (redacted)
>
> Dear Godaddy
>
> Please review
> http://blog.aa419.org/2017/09/08/an-open-letter-to-godaddy-whois-service/
>
> This is an open letter to Godaddy on behalf of the the anti-abuse
> community.
>
> Regards,
>
> Derek Smythe
> Artists Against 419
> http://www.aa419.org
>
An auto-reply was received from Godaddy Legal, but no other reply. But that indicates the email response made it to the Godaddy email servers and Godaddy had the opportunity to investigate this issue, but chose not to. As such their blocking and substitution is wilful and willfully in violation of the ICANN RAA.The usage of Whois data by Artists Against 419 is in line with the provisions of the RAA and does not violate it in any way. All our process are manually initiated and uses stock standard protocols and methods, no automation is used for mining the Godaddy Whois service. The consumers of the data and results are law enforcement, consumer protecting groups and investigators (such as Steve Baker of the US BBB for his recent pet scam study showing how these malicious actors, websites and domains have undermined the legitimate pet trade).
Apparently ICANN Compliance has been made aware of this issue before:
> ——– Forwarded Message ——–
> Subject: Re: [users] GoDaddy limiting their WHOIS records?!?
> Date: Fri, 15 Sep 2017 08:53:15 -0400
> From: (redacted)
> Reply-To: users
> To: users
>
>
>
> On 9/8/2017 2:29 PM, Patrick Klos wrote:
> > On 9/8/2017 1:56 PM, Cedric Knight wrote:
> >> $ whois -h whois.godaddy.com balanceinlove.com
> >> seems to work
> >
> > Sure, it works for you because your IP address hasn’t been
> > “restricted” (yet).
> >
> > That’s part of the problem. People try it and see it works for them
> > without understanding that GoDaddy (and possibly others) are
> > creating _per-IP-address restrictions_ in their WHOIS servers.
>
> Has anyone (else) filed a complaint with ICANN about this? How did
> you make out?
>
> I gotten responses indicating ICANN would like to ignore or sidestep
> the issue if at all possible. First they try to tell me GoDaddy’s
> WHOIS is working fine. Then they imply that I used the wrong tickbox
> to file the complaint (I clicked on “Registrar does not meet Whois
> Service Level Agreement (SLA) requirements” because that’s what’s
> happening). They continue by telling me “Please note that the
> corresponding registrar’s current Whois Port 43 and web-based Whois
> service are operational.”, all the while ignoring my repeated claims
> that the results are dependent upon the source IP address of the request!
>
> Please tell me others are trying to get ICANN’s attention about this
> as well?
>
> Patrick Klos
> Phishcop AdminAlso see the comments at https://onlinedomain.com/2017/10/05/domain-name-news/neustar-destroyed-biz-us-domain-name-whois-service/
> Jose
> October 6, 2017 at 7:48 pm
>
> Godaddy has been doing this for .com and .net since 4 months ago. Haven’t anyone seen this yet??
>
> They are blocking even 5 queries made within 20 minutes!
>
> First complaint to ICANN they say the whois was working. Off course it works for one query specially if it comes from ICANN IPs since they have the obligation to monitor QoS…
>
> After insisting and giving concrete examples they are still to replyRegards,
Then, on 26 Oct 2017 (8 days later):
Dear Derek Smythe,
Thank you for your response. In order to address your complaint to the registrar of record properly, ICANN requires the following:
By 2 November 2017, please confirm your permission for ICANN to forward your complaint below and any attachment or communication you have provided in your response(s) to the registrar of record and any other party with whom ICANN may consult in order to address your complaint.
If you do not provide this information on or before 2 November 2017, ICANN will close your complaint.
Thank you for your cooperation.
Sincerely,
ICANN Contractual Compliance
Reply 26 Oct 2017:
Hello ICANN Compliance
Hereby I explicitly give you permission to forward any and/or all
information I sent to you to any party as is relevant to the
resolution of this issue.Thank you.
The eventually, on 31 Oct 2017:
Dear Derek Smythe,
Thank you for submitting a complaint concerning the registrar GoDaddy.com, LLC. Your report has been entered into ICANN’s database. For reference your ticket ID is: RTN-088-27208.
ICANN will follow up with the registrar per process and provide you an update with its findings.
For more information about ICANN’s process and approach, please visit http://www.icann.org/en/resources/compliance/approach-processes .
Sincerely,
ICANN Contractual Compliance
The reader should note the games being played here, with time going by while frustrating legitimate usage of WHOIS details, enabling fraud on the internet. Every time the complainant is given 7 days to respond …. tick tock … yet:
06 Oct 2017 : aa419 Ticket lodged
17 Oct 2017 : 11 days later, ICANN Compliance reply making complaint off as inaccurate using wrong submission
18 Oct 2017: 1 day later: aa419 detailed response, showing why the complaint is in fact valid, correct and the harmful effect of this blocking
26 Oct 2017: 8 days later: ICANN Compliance request to forward details.
27 Oct 2017: Immediately: aa419 permission to ICANN Compliance.
31 Oct 2017: 4 days later: ICANN Compliance finally accepts complaint.
It should be noted nothing new and/or of value was communicated after the orginal complaint on the 6th of Oct. This complaint was stalled from the 6th of Oct to 31st of Oct on a clear policy issue that Godaddy is violating. This was clearly communicated right from the word go in an open and public post, readable above. There was no reason for this delay.
The ICANN RAA 2013 is the result of a bottom-up, consensus-driven, multi-stakeholder model comprised of three parts: the ICANN Community, the ICANN Board, and the ICANN Organization. Allowing a registrar to violate these terms, then delaying on action has one predicatable result; harm and frustration, undermining the legitimate internet.
But this is also not the first time this has been seen in tickets lodged with ICANN Compliance.
Godaddy now doing blanket blocks?
Apparently Godaddy has now decided to block numerous unknown IP address, substituting the standard WHOIS output with a lesser junk output. To verify this conclusion, an IP address under my control, never used once for a WHOIS lookup in the past four years, was used to do a lookup on malicious domain royalecargolines.com. The result?
$ whois royalecargolines.com -h whois.godaddy.com
Domain Name: royalecargolines.com
Registrar URL: http://www.godaddy.com
Registrant Name: Rapheal wallah
Registrant Organization:
Name Server: NS231.GLOBEHOST.COM
Name Server: NS232.GLOBEHOST.COM
DNSSEC: unsignedFor complete domain details go to:
http://who.godaddy.com/whoischeck.aspx?domain=royalecargolines.com$ date
Sat Nov 4 21:32:55 UTC 2017
So much for ICANN RAA 2013, Sect 3.3.1 and 3.3.5 where Godaddy’s Port 43 has gone rogue while an ICANN Compliance complaint is stuck in the compliance doldrums.
Update 2017-11-23
At this stage even ICANN’s own WHOIS service is failing with Godaddy domains. Has ICANN done too many WHOIS lookups that Godaddy considers this abusive (since it appears the tail is now wagging the dog)?
Sent to ICANN Compliance:
Hi ICANN Compliance
Just an update.
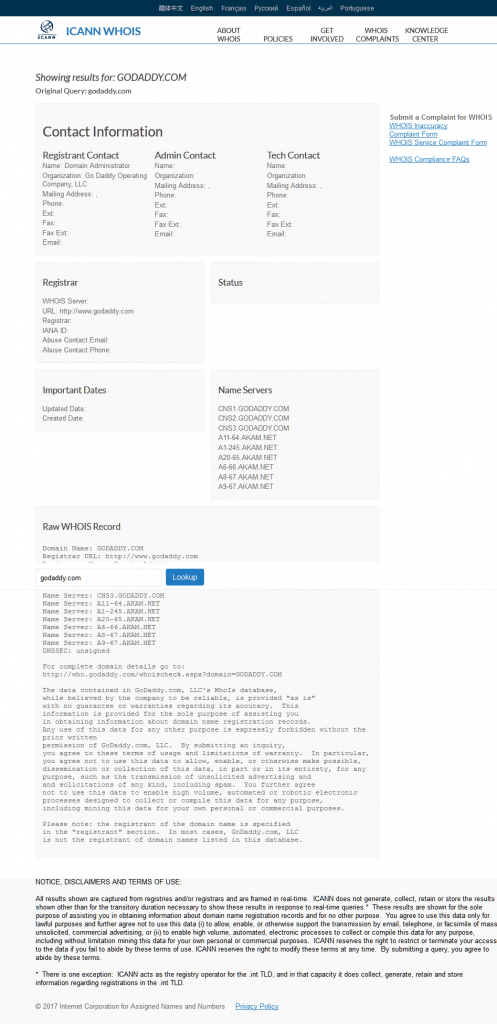
Currently I can’t even use ICANN’s own website to look up a Godaddy sponsored domain.
https://whois.icann.org/en/lookup?name=godaddy.com
Domain godaddy.com was used as to not confuse issues.
Snapshot attached.
Regards,
Update 2017-11-24
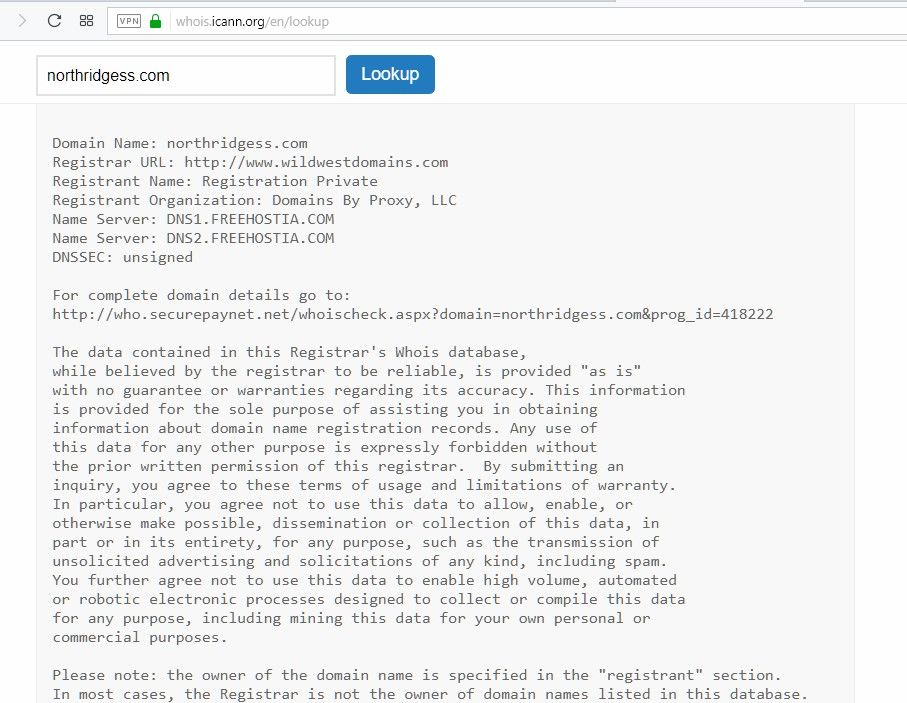
Even ICANN’s WHOIS query failing to be able to access prt 43 on Godaddy when we look at affiliated Wild West Domains. ScamPup has lodged a complaint with ICANN Compliance on this issue.
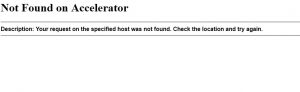
Trying to do a a query on malicious domain northridgess.com yields the same substituted fromat as we see on Godaddy, although the link shown to use is to another URL http://who.securepaynet.net/whoischeck.aspx?domain=northridgess.com&prog_id=418222 to be used:
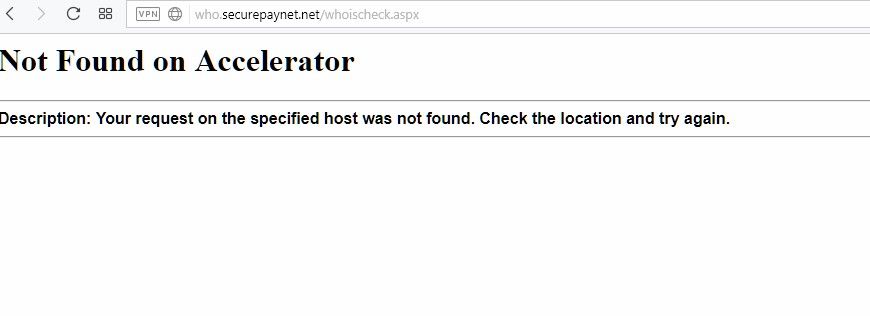
But it gets worse: Going to the shown URL http://who.securepaynet.net/whoischeck.aspx?domain=northridgess.com&prog_id=418222 as per the query yields an error:
Not Found on Accelerator
Description: Your request on the specified host was not found. Check the location and try again.
For the folks encountering this, currently you’ll have to go play reCaptcha games on https://www.godaddy.com/whois/ and pray you don’t get caught in the dreaded ReCaptcha loop.