DNS Abuse Dominoes
While ICANN, the regulators and the various interest groups are debating the definitions of DNS abuse, what constitutes a security threat and is within their responsibility (or rather not), what’s wrong in this area, fraudsters don’t care about these shenanigans. They’re exploiting DNS to their own advantage in well defined illegal activities.
The rules made when the Internet was young, seems unable to keep the steps with current realities. The divide between the ideal Internet in the regulators’ model and the one we’re dealing with daily, is widening as ever increasing numbers of fraud actors learn how to abuse and hijack anything they can in their efforts to steal unwary consumers’ money.
While there are no definitions of Advance Fee Fraud everyone can agree on, there are also no standard ways of dealing with the abuse of the online space the bad actors base their frauds on. There might be rules, but those rules are inconsistently applied at each Registrar / hoster, with each having their own interpretation of rules. This has educated the fraudsters well.
One of the main elements used in blaming the victims of online fraud is a basic question: Why didn’t they check before being defrauded? This is easy to say, yet increasing harder to do lately.
The Internet is crowded with crawlers and spiders reposting content in what looks almost like a general click-bait contest. No one seems to care how legitimate the original source is. Fake businesses using fraudulent websites (and sometimes smart SEO campaigns) shows up in various places online. In all that noise, it becomes almost impossible for an untrained person to guess what is real and what is fake.
We don’t have courses in schools to teach us, for example, the difference between a simple search key in Google and the same search key in quotes. In the real world, you need a license to prove you’re qualified to drive a car. The Internet has no license. One can chose to have a car or not, but no such liberty exists when it’s about the Internet with everything forcing us to use online resources. We end up having our entire life online – finance, work, education, social interactions.
The average Internet user assumes that someone is checking before allowing a website online, yet the reality is that the processes are mostly automated. The checks we see happens usually only after someone gets defrauded and complains about it, if at all.
One might imagine that a Registrar or a hoster will never register / host a domain name impersonating a registered company name. They might refuse to register the obvious ones, but many are well aware that the bad actor will turn to another Registrar / hoster more “flexible” in that regard. At the end of the day it’s all about business and we even find the term “bullet proof hoster”. Yet these “bullet proof hosters” also sell domains.
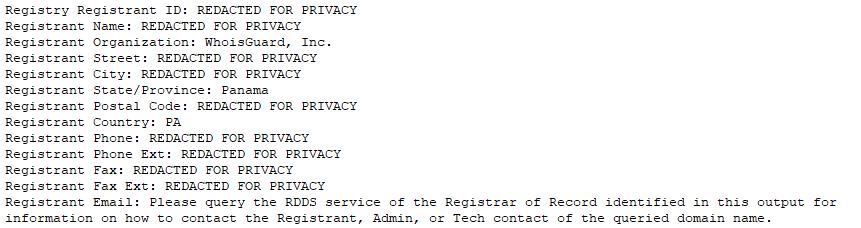
Before the GDPR, identifying a bad actor creating a fake website used in Advance Fee Fraud was easy, based on a WHOIS check. That option is now gone for the average user, with even the privacy protection provided by the Registrar now sometimes hidden behind the GDPR privacy blanket:
While regulators, law enforcement or financial institutions have jurisdictional problems they try to solve mitigating abuse and fraud, fraudsters have no such problems. When they don’t steal from one another, these bad actors can happily share the same infrastructure and develop their other part of the business independently. The case illustrated here is a perfect example of how the DNS abuse happens and nobody seems to notice or wishes to acknowledge it.
Domino effect – the case study
In this study we have a total of 295 domains impersonating banks and associated websites used to impersonate oil companies, pharma and other romance scam related websites. Then we uncover another 153 domains impersonating couriers. We managed to identify and analyze 336 of these fraudulent domain names. The entire list can be seen here:
https://db.aa419.org/fakebankslist.php?cmd=ADV&x_Project=dominoeffect.
Different fraud syndicates share the same resources abusing these domain names. In some cases they use the services of the same faker maker. In other cases they only share hosting accounts or SSL certificates.
The idea for a case study started with a dying widow scam as shown at https://www.scamsurvivors.com/forum/viewtopic.php?f=6&t=76369:
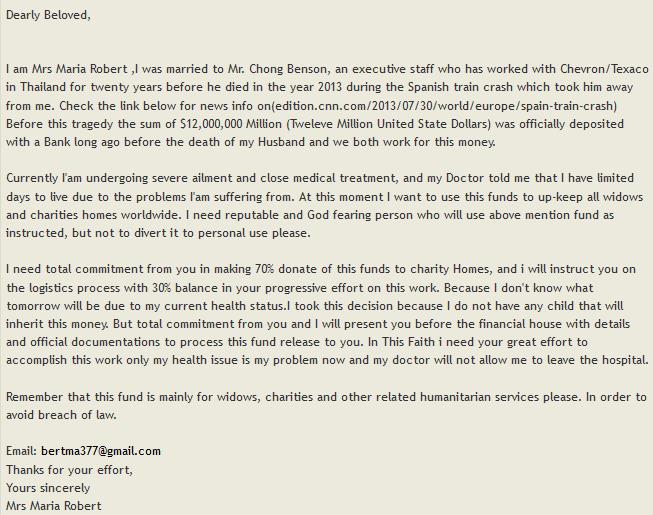
We’ve found that over 80% of such scam spams leads to malicious domains and websites. This was no different. A fake lawyer followed and after that a bank:
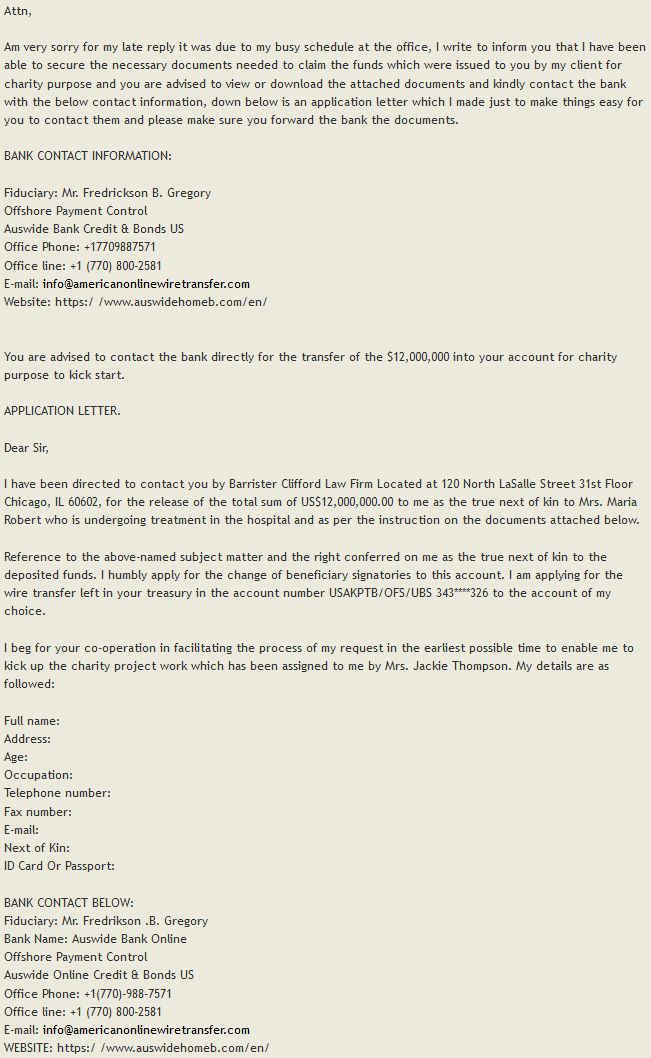
The bank was impersonating a real bank (as it can be seen in last line of the message shown above). There was no content on the fraudulent domain name – the fraudsters were using it only for the email address. During the interaction with the fraudster, another domain name was sent to the potential victim on the forth bank email, with the same sender email address being used.
But there was no bank, no problem. Another email followed, and another and another using the same domains. The fourth time we find a slight variation in the domain name. Domain auswidehomeb.com becomes auswidehomebk.com:
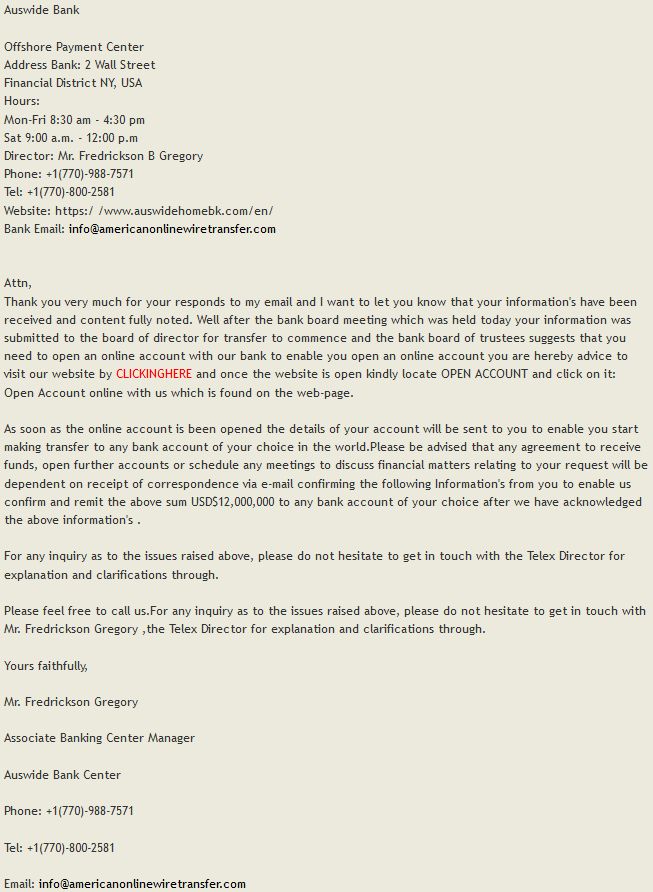
To the casual internet user, it might have appeared that there was no content on auswidehomebk.com, only a parking page.

Yet the fraudster was sending the direct link for were the “bank” was really hidden:
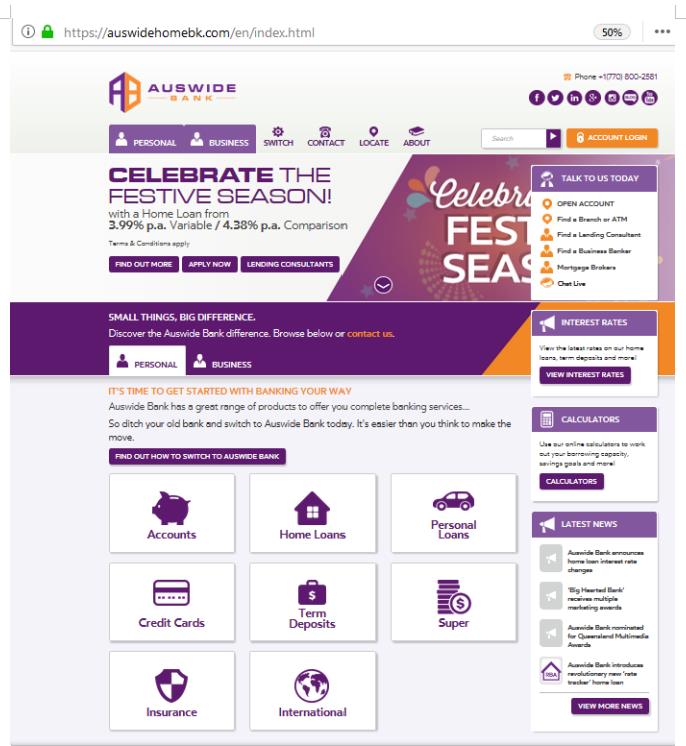
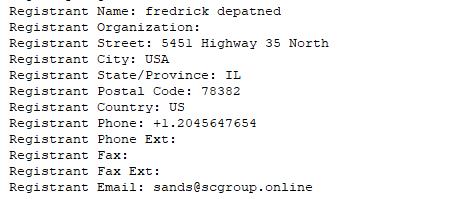
As it happened, in this case the registrant details wasn’t hidden:
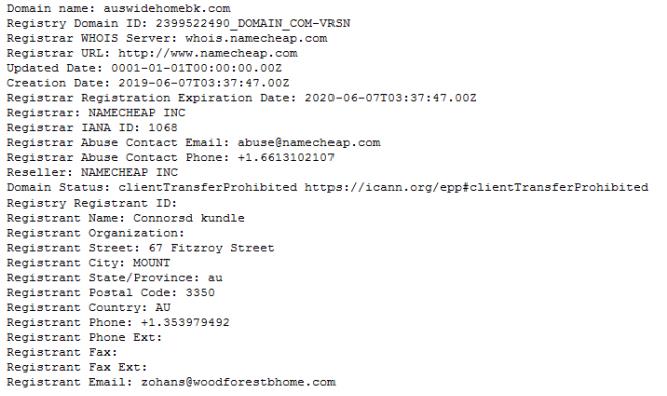
There’s a second bank registered with another email address on to the same woodforestbhome.com domain name:
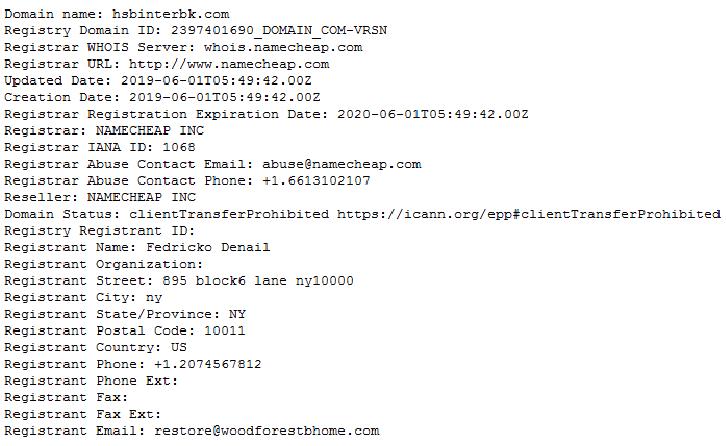
Once again the index page would appear to be a parking page:

Once again the actual content is hidden in a sub-directory as before:
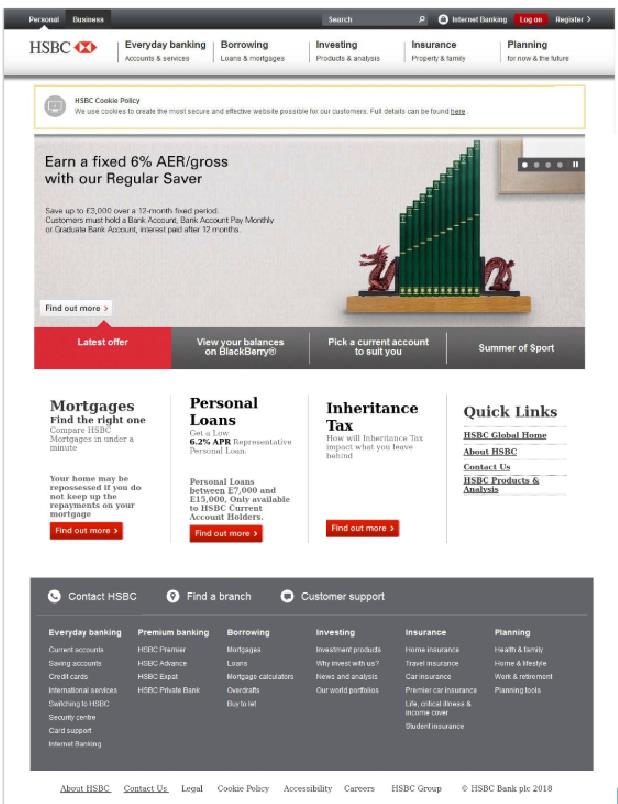
Apparently these “banks” were registered by another bank, woodforestbhome.com, with a maintenance page on it’s website:
Yet, hidden in a sub-directory, we find another 419 spoof of a bank:
So who does woodforestbhome.com belong to?
So this domain is registered with another email address claiming to belong to yet another bank. We continue like this, uncovering fraudulent bank spoofs registered with the address of yet other bank spoofs. The domino effect?
Scam syndicates connected
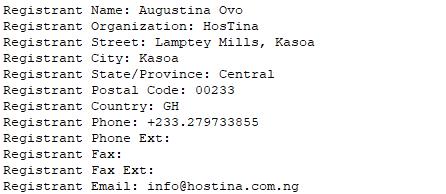
The first identified group of fraudulent websites are operated from Ghana. The domain name lgbkonline.com, impersonating Leads Guaranty Bank, is registered in Ghana by a Nigerian hoster.
A second one is centered around the email address mikepaulo1100@yahoo.com. During previous abuse way back in 2014 he claimed to be:
Currently this party claims to be:
| rbsintoniine.com | Royal Bank of Scotland | mikepaulo1100@yahoo.com |
| rbcroyalbn.com | Royal Bank of Canada | mikepaulo1100@yahoo.com |
| firstbknigeriaplc-online-access.com | Central Bank of Nigeria | mikepaulo1100@yahoo.com |
| eciticbnkgzcn.com | Citi Bank China | mikepaulo1100@yahoo.com |
| ecitcbnkcn.com | Citi Bank China | mikepaulo1100@yahoo.com |
| commerceswissb.com | Commerzbank Switzerland | mikepaulo1100@yahoo.com |
| ibkonlinesecure.com | Wells Fargo | mikepaulo1100@yahoo.com |
| dongguanonlineb.com | Dongguan Bank China | mikepaulo1100@yahoo.com |
| zocsparcel.com (expired) | ZOCS Worldwide | mikepaulo1100@yahoo.com |
| gscour.com | GSC – Global SC | mikepaulo1100@yahoo.com |
| eagleexpresscargoseurityservices.com | Eagle Express Cargo & Security Services | mikepaulo1100@yahoo.com |
| chasebakonline.com | Chase Bank Online | mikepaulo1100@yahoo.com |
| web-cmbonline.com (expired) | China Merchants Bank | mikepaulo1100@yahoo.com |
| asgetisl.com (expired) | Asia Springlite Group Elite Travels | mikepaulo1100@yahoo.com |
| enecitcnbnk.com (expired) | China Citic Bank | mikepaulo1100@yahoo.com |
| en-citicngz.com (expired) | China Citic Bank | mikepaulo1100@yahoo.com |
| e-citicncbk.com (expired) | China Citic Bank | mikepaulo1100@yahoo.com |
| cnb-ecitbkofcn.com (expired) | China Citic Bank | mikepaulo1100@yahoo.com |
With fgbonline.net spoofing First Gulf Bank, we find another syndicate from Ghana crossing paths:
| wfbonline.net | Wells Fargo Bank | meeetjem@gmail.com |
| laurencelawfirm.com | Laurence Law Firm | meeetjem@gmail.com |
| holytrinityorphanage.com | Holy Trinity Orphanage Ghana | meeetjem@gmail.com |
| grb-ae.com | Global Remittance Bank | meeetjem@gmail.com |
| g4snet.com | G4S International Logistics | meeetjem@gmail.com |
| fbonet.net | First Bank of Ohio | meeetjem@gmail.com |
| diamondslogistics.com | Diamonds Logistics Ltd | meeetjem@gmail.com |
| cargosco.com | Cargo Shipping Company | meeetjem@gmail.com |
| bridgebg.com | Bridge Bank Group Ivory Coast (BBG CI) | meeetjem@gmail.com |
| agricbnet.com | Agricultural Development Bank of Ghana (ADB) | meeetjem@gmail.com |
| fgbonline.net | First Gulf Bank | meeetjem@gmail.com |
| unclc.com (expired) | Universal Courier and Logistics Company | meeetjem@gmail.com |
Who remembers ‘Have a Coke and a scam‘? The same scammer now has comericab.com, impersonating Comerica Bank which leads to a South African “branch“ of his identity. When the registrant email address fjrasile@yahoo.com was first reported back in 2013, he was:
A year later until last time when we checked, while being busy with Coca-Cola lotteries scams, he was:
But where did Frank and his Coke scams originate from? Nine days before first observing Frank, we had a previous Coca Cola spoof:
To understand why these syndicates have become so powerful, we only have to look at domain glfswww.com. Despite many reports with evidence of blatantly deliberate inaccurate registration details, this domain abused for a fake courier was devolved to host mitigation time and again, “it was not DNS abuse” as per the wise anti-abuse sages.
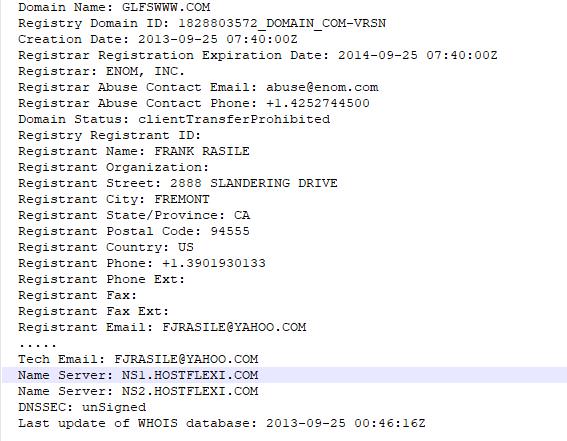
This resulted in the inevitable host hopping and victims:
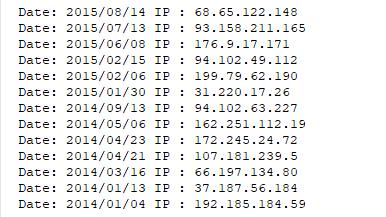
So far there are 31 fraudulent domain names that he registered and we managed to identify.
| invsetec.co.za | Investec | fjrasile@yahoo.com |
| comericab.com | Comerica Bank | fjrasile@yahoo.com |
| yorkshiresb.com (expired) | Yorkshire Bank | fjrasile@yahoo.com |
| thomasphilipsuk.com (expired) | Thomas Philip | fjrasile@yahoo.com |
| cokeawards.net (expired) | Coca-Cola | fjrasile@yahoo.com |
| standardb.net (expired) | Standard Bank | fjrasile@yahoo.com |
| mycokeawards.net (expired) | Coca-Cola | fjrasile@yahoo.com |
| cokereward.net (expired) | Coca-Cola | fjrasile@yahoo.com |
| cokegifts.com (expired) | Coca-Cola | fjrasile@yahoo.com |
| gfswww.net (expired) | Global Financial Solution | fjrasile@yahoo.com |
| ppelischekltd.com (expired) | Patrick Pelischek Industrail & Machinery Supplier | fjrasile@yahoo.com |
| thomasphilipuk.com (expired) | Thomas Philip Advocates & Solicitors | fjrasile@yahoo.com |
| peterhomeofantiques.com (expired) | Peter Home of Antiques | fjrasile@yahoo.com |
| ccolarsa.net (expired) | Coca-Cola | fjrasile@yahoo.com |
| yorkshireb.com (expired) | Yorkshire Bank | fjrasile@yahoo.com |
| coke-reward.net (expired) | Coca-Cola | fjrasile@yahoo.com |
| gfsrsa.com (expired) | Global Financial Solution | fjrasile@yahoo.com |
| gfswww.com (expired) | Global Financial Solution Ltd | fjrasile@yahoo.com |
| mycokereward.org (expired) | Coca-Cola | fjrasile@yahoo.com |
| cocacolareward.net (expired) | Coca-Cola Promo | fjrasile@yahoo.com |
| mycokereward.net (expired) | Coca-Cola Promo | fjrasile@yahoo.com |
| cokerewards.net (expired) | Coca-Cola South Africa | fjrasile@yahoo.com |
| cawardrsa.net (expired) | Coca-Cola South Africa | fjrasile@yahoo.com |
| cokeaward.org (expired) | Coca-Cola | fjrasile@yahoo.com |
| glfswww.com (expired) | GLFS Group | fjrasile@yahoo.com |
| ccrsa.net (expired) | Coca-Cola | fjrasile@yahoo.com |
| gfsww.com (expired) | Global Financial Solution | fjrasile@yahoo.com |
| ccawardza.net (expired) | Coca-Cola | fjrasile@yahoo.com |
| samsungawards.net (expired) | Samsung | fjrasile@yahoo.com |
| standard-b.com (expired) | Standard Bank | fjrasile@yahoo.com |
| cokecolasa.net (expired) | Coca-Cola Promo | makera@inbox.com |
We’ll skip historic fights with registrars about this blatant abuse of domains which led to aliases f.rasile@yahoo.com and latorcorpdesign@gmail.com, proven to be the same party as fjrasile@yahoo.com, that led us to now.
Linked to the above mess, we find another Nigerian actor operating a bank and a courier scam from the domain name logiscargodhl.com. It’s pretending to be both Logis Cargo Ltd. as well as Finance Bank. Two years ago he was actively doing romance scams using stolen pictures of a Focus Hawaii Agency model.
With europexpres.com, pretending to be Europ-Express France, we stumble upon a Benin loan scam syndicate:
https://db.aa419.org/fakebankslist.php?cmd=ADV&x_Project=beninloan
With bw-logisticsinc.com pretending to be a courier named BorderWay Express Logistics, we enter the Cameroonian Fraud arena – epo.johnson@yahoo.com:
| pracianaturals.com | Pracia Naturals | epo.johnson@yahoo.com |
| kushbase420.com | Kush Base 420 | epo.johnson@yahoo.com |
| horizonelogistics.com | Horizon Logistics / Trans Logistics | epo.johnson@yahoo.com |
| deltamotorsptyltd.com | Delta Motor Pty Ltd / Rotakuwa General Trading Ltd | epo.johnson@yahoo.com |
| blgspolka.com | BL Group Spolka | epo.johnson@yahoo.com |
| bw-logisticsinc.com | BorderWay Express Logistics | epo.johnson@yahoo.com |
Domain expresslinedelivery.com used to host a matching fraudulent delivery company, leads to yet another Cameroonian fraud syndicate:
| visionepxdelivery.com | Vision Express Delivery | lorahandersson84@gmail.com |
| uses-ps.com | USES Postal Service / USES-PS Logistic Services | lorahandersson84@gmail.com |
| thaigloballogisticscompany.com | Thai Global Logistics Company LTD | lorahandersson84@gmail.com |
| royalbluepitbull.com | Royal Blue Pitbull | lorahandersson84@gmail.com |
| megatravelagencyltd.com | Mega Travel Agency | lorahandersson84@gmail.com |
| expresslinedelivery.com | Express Line Delivery | lorahandersson84@gmail.com |
The registrant details of spoofs of Santander, CapitalOne and RainForest banks, leads us to the fake pharma supplier arena, with the orginal pharma domain being registered using a proxy provider:
| satanderlb.com | Santander Bank | nextlevel@richardpharm.com |
| capitonehomeb.com | Capital One Bank | next@richardpharm.com |
| rainforestcapitalb.com | Rainforest Capital Bank | nextlevel@richardpharm.com |
| richardpharm.com | Richard Pharamceuticals Ltd (PDL) | richardpharm.com@superprivacys ervice.com |
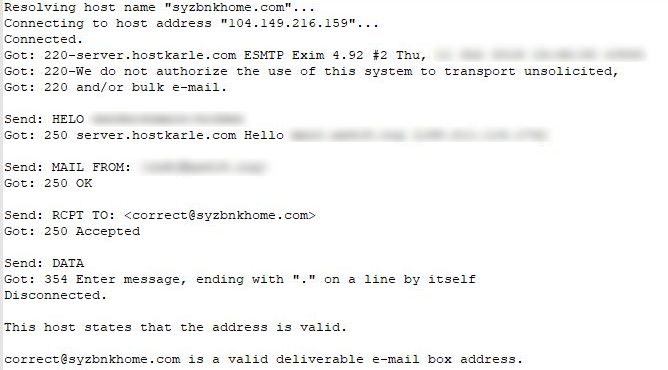
A spoof of the SYZ Bank is showing a host suspension page, yet it’s email was similarly used for registrant email addresses, initially starting with a proxy protected domain. In this example we also show how different registrars are used:
| firstexashome.online | First Texas Bank | correct@syzbnkhome.com | Namecheap, Inc. |
| cltihomebk.com | Citi Bank | correct@syzbnkhome.com | Namecheap, Inc. |
| syzbnkhome.com | SYZ Bank | contact@whoissecure.net | Ownregistrar, Inc. |
Despite the supposed host suspension, the email address is still active at the same host:
Domain scblhome.com used for spoofs such as Standard Chartered Bank, Bank of America (boalhomeb.scblhome.com) and the Federal Reserve (fedresvbnk.scblhome.com), was abused in a similar way, also registered via proxy protection:
| udssexpresslogistic.com | UDSS Express Logistics Limited | deals@scblhome.com |
| polarfreightglobals.com | Polar Freight Global Services | deals@scblhome.com |
| suntrsthomebk.com | SunTrust Bank | deals@scblhome.com |
| uobhomeb.com | United Overseas Bank Malaysia (UOB) | deals@scblhome.com |
| frosthomebk.com | Frost Home Delivery Services Limited | dyna1@scblhome.com |
| standchdbnk.com | Standard Chartered | earlyhr@scblhome.com |
| citlgroupb.com | Citi Bank | deals@scblhome.com |
| suntrstbhome.com | SunTrust Bank | earlyhr@scblhome.com |
| cityhomeb.com | Citi Bank | dyna1@scblhome.com |
Domain scblhome.com is now parked – long live scblhome.online. Rinse and repeat:
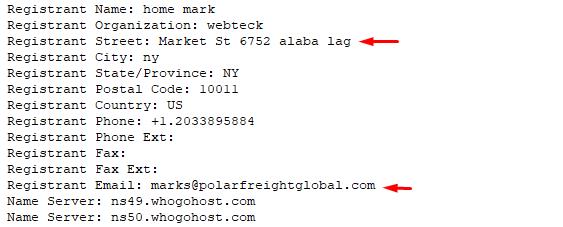
The index page is the one seen before.
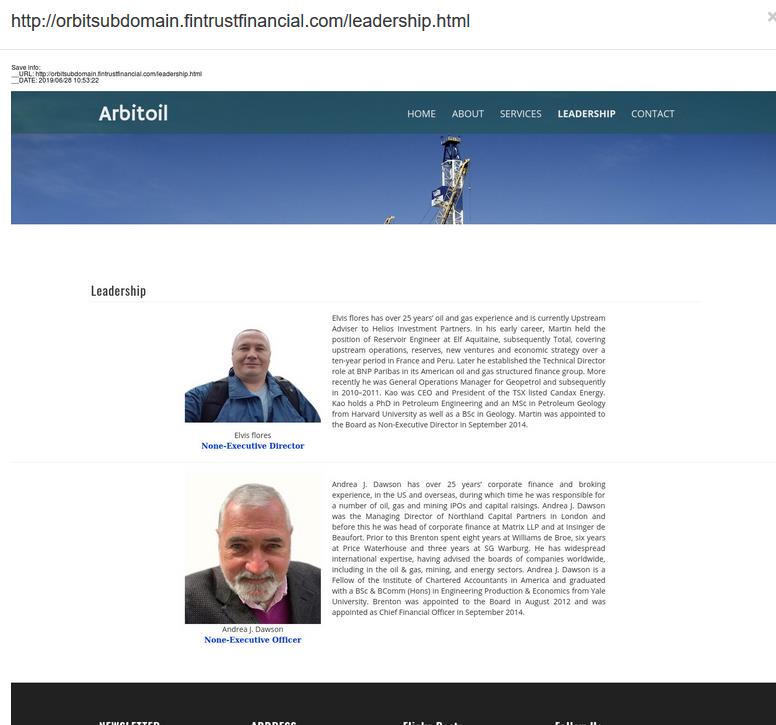
A fake bank is also an oil company simultaneously, with a divorced CEO, searching for love online and depriving his victims from all the money he can get. Domain fintrustfinancial.com is FinTrustFinancial Bank on it’s main website, but then also Arbitoil Engineering as per the domain’s one sub-domain.
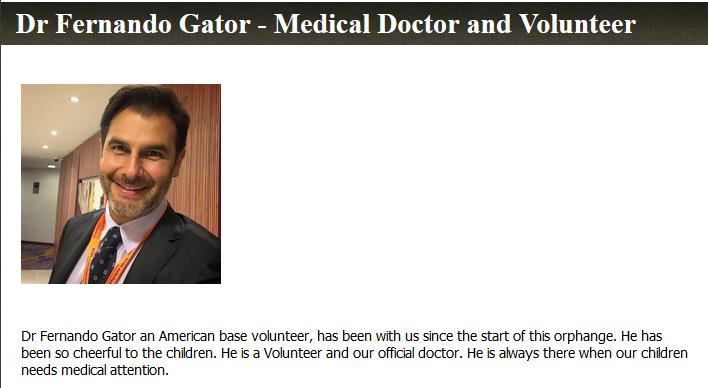
A fake orphanage holytrinityorphanage.com in Ghana is also used in romance scams. Their only American volunteer uses stolen pictures of a known doctor, a photo reported many times over the years by victims defrauded by these scammers.
A set associated couriers follows the same recipe. Virginia Farmer Matt Lohr, named NRCS Chief in 2018, will be surprised to learn that he was promoted to a diplomat, also has a new name. At least this is what an image of his says on a lot of the fake couriers, associated with these fraudulent websites. Meet “Senior Diplomat John Mathieu”!
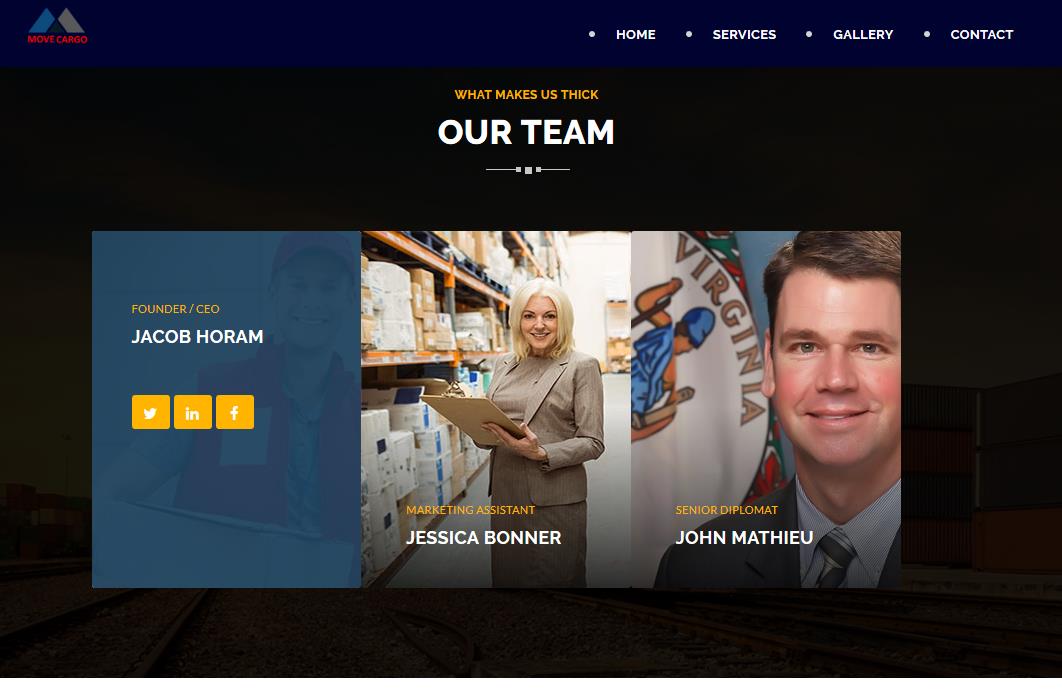
Analyzing the associated fake couriers, we find the same design elements used repeatedly. The association is clear. For example, we see addresses such as “6 River Hill Duharm“, sometimes in the UK, sometimes in Turkey, sometimes in the USA.
Let‘s look at those fake sites from another perspective. There are four domains impersonating Barclays Bank, 14 impersonating HSBC, 5 impersonating the Dubai Islamic Bank, 7 impersonating Citi Bank and 24 pretending to be FirstFlight Courier.
The examples can go on forever. Behind all the statistics and posturing surrounding the procedures at ICANN, we also find the reality of Advance Fee Fraud. Bad actors are working together for the common goal, on one side, to defraud consumers and small businesses. All the pomp and procedure at ICANN has long since become disjointed from realities the fraudsters understand and exploit. In the middle are the consumers, the victims defrauded every day. This fraud uses the DNS system caring little about definitions. The policy regulators of the Internet are debating theoretical concepts while fraudsters are busy abusing the system and destroying lives.