Tender Scams: A new twist in 2023
Extract of an update on the alert at https://blog.aa419.org/2019/11/04/the-south-african-tender-scam-za-tender-scam/.
2023 started off with a bang for South African based tender scams. Users were complaining, asking how an official .gov.za could be used on Twitter in response to a Department of Home Affairs alert at https://twitter.com/HomeAffairsSA/status/1624636511617445889.
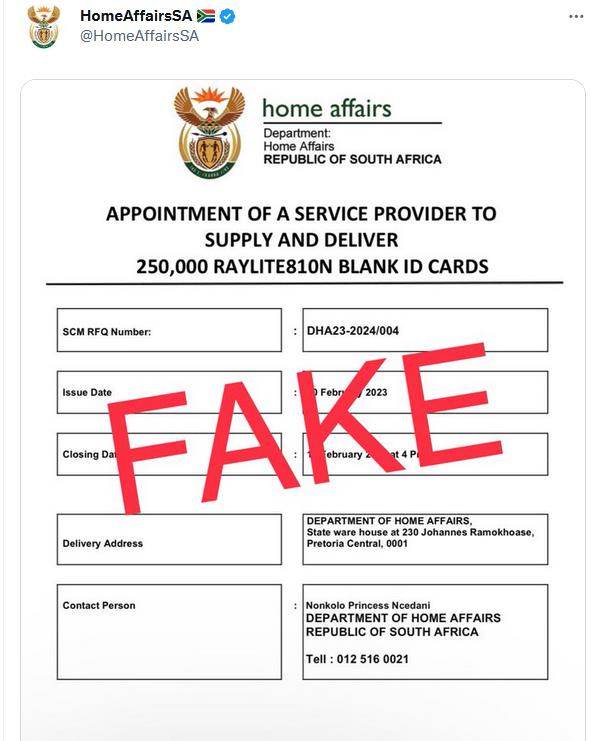
Any reasonable ITSec investigator would assume this to just be a spoof and users Davie and Akintola falling for the scam. Any reasonable ITSec investigator would be wrong.
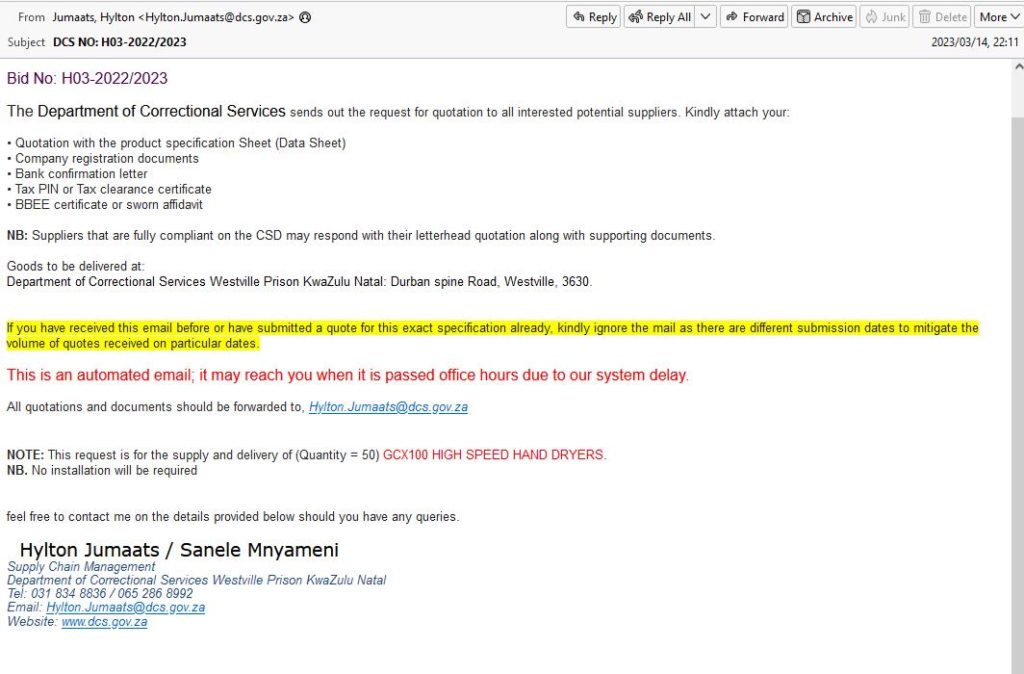
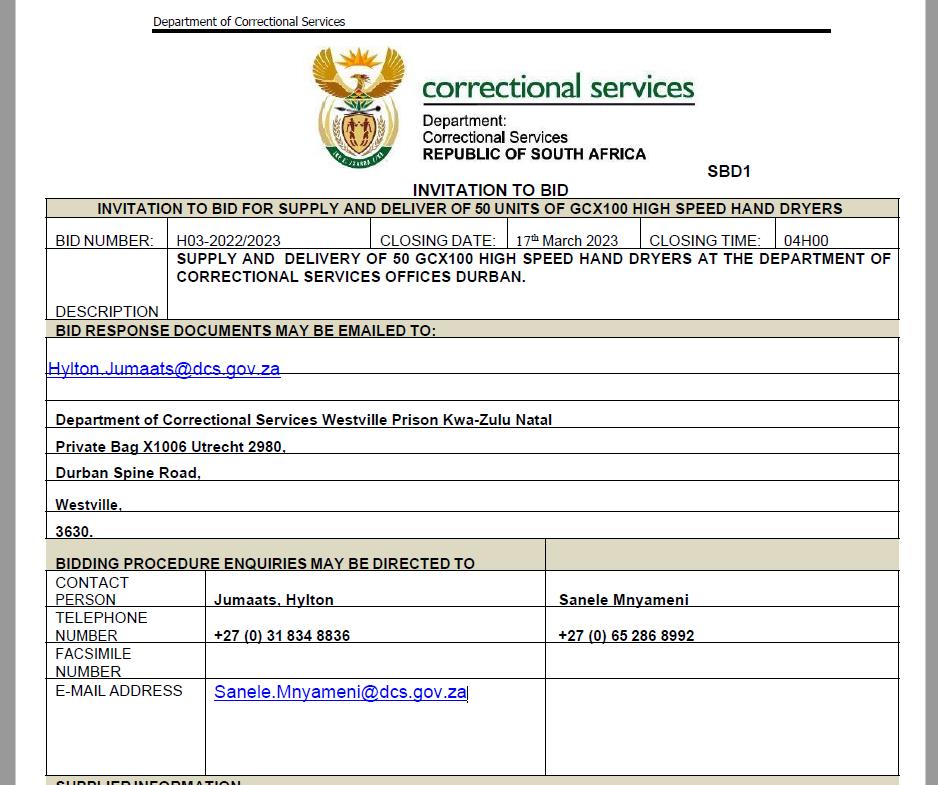
Artists Against 419 managed to obtain a raw email. More surprising is that we saw that not only was the Department of Homes Affairs dha.gov.za domain being abused, it also revealed a second government domain was also being abused, dcs.gov.za. Artists Against 419 alerted the authorities immediately.
On 18 March 2023 we received yet another raw tender scam email. Incredulous at what we were seeing, we reached out to a well known reputable party in cyber forensics who kindly offered up his time to confirm what we could not believe, fraudsters were sending out scam emails via the Department of Correctional Services domain. It was clear we were seeing a new evolution in the tender scam:
- Initially two fake websites were created, published on two separate domains,
- Later this evolved to one of the domains spoofing a government department with no content.
- The newest evolution was abusing a real ZA Government domain and sending out fraudulent RFQs this way.
All the work IT Security experts had put into SPF, DKIM and DMARC was now useless. Fraudsters had achieved the wet dream of any fraudster, the ability to defraud using an official government domain behind a reputable email security provider, guaranteeing the emails would be white listed, ensuring a more efficient and successful targeting of South Africans. More so, respondents are being asked for personal details, something considered PII, using resources of the South African government.
Received: from securemail-y55.synaq.com ([196.35.198.122])
Email header
by dedi436.nur4.host-h.net with esmtps (TLS1.3:ECDHE_RSA_AES_256_GCM_SHA384:256)
(Exim 4.92)
(envelope-from <(redacted)@dcs.gov.za>)
id 1pcB48-0006NT-96
for (redacted)@(redacted); Tue, 14 Mar 2023 22:16:23 +0200
Considering suspects had long since been identified, at least one actor extremely proficient in all things DNS and security related, another extremely proficient in procurement processes, yet nothing ever happened since 2015, we are not really shocked to see the latest evolution. It’s only a natural progression of what fraudsters will do when they operate in a fraud tolerant system where a government has no real cyber security posture.
The relevant authorities were alerted and details captured in our database entry https://db.aa419.org/fakebanksview.php?key=160573