The South African Tender Scam (ZA Tender Scam)
The South African tender scam has been targeting businesses in Southern Africa for a while. While it’s a procurement scam targeting businesses, which in itself isn’t unique, the execution of it is and is identifying. It has already led to devastating financial losses, forcing many smaller business to close their doors in South Africa, resulting in job losses. This is at a time when the South African economy can ill afford it. Typically new naive, or unaware business owners, easily fall prey to this scam.
History
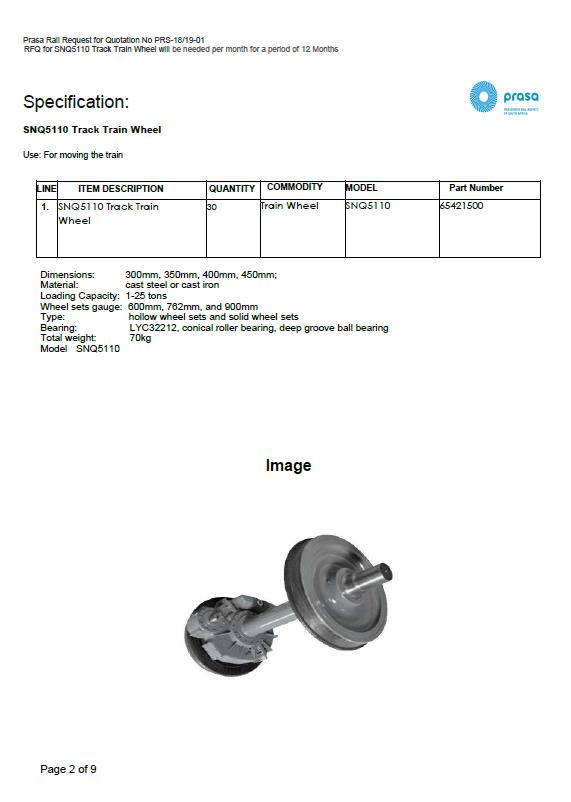
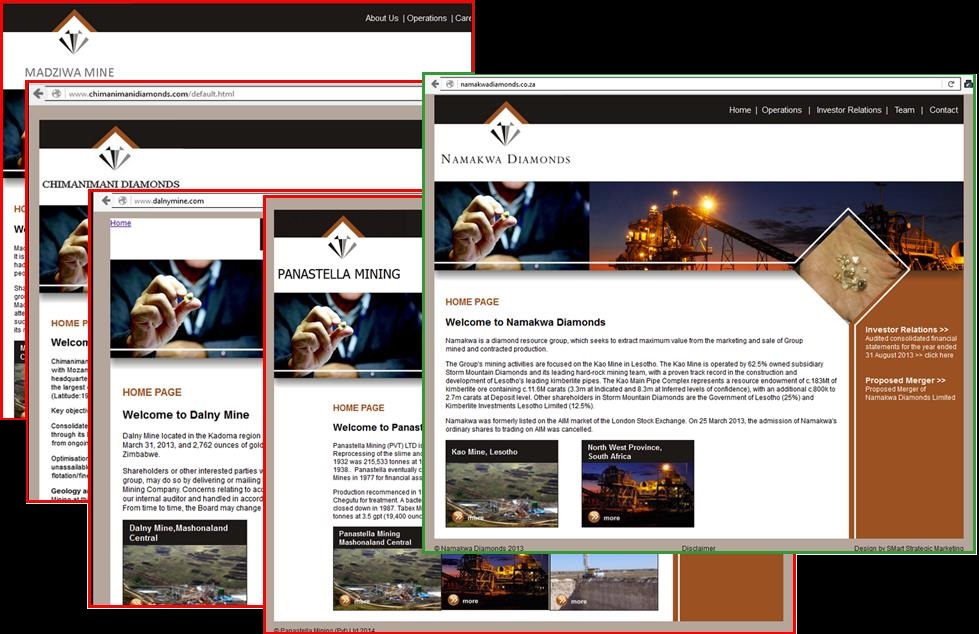
This scam was originally called the Mining Supplies Scam. In this scam, a mine in Zimbabwe would contact South African businesses seeking a certain high value item typically used in the mining industry. Drill bits were extremely popular. The requirements were for exactly the stated item, no substitution would be acceptable. A check on the mine would show it to exist, although details were vague. In reality many of the real mines with the name being spoofed had been closed down, or bought out by other mining groups. Cloning and spoofing real mining websites was common. This made verification extremely difficult.
The business owner, eager to accept the business, would see if the sought item could be sourced. Sure enough, searching on the internet reveals one business actually selling these items. A query to the potential supplier would result in a reply that the item is available in the desired quantities. Price negotiations would normally succeed. Unbeknownst to the business owner, this wasn’t a real business, rather part of the scam being perpetrated by the fraudsters responsible for the fake mine query.
This part of the scam which continues today still, will take a stock item generally available. This item will be given a unique stock or part number. Images of the real item may be edited to hide it’s true origins. This is then the item that’s being requested. Various web techniques are used to make sure this item can be found in a search engine, uniquely at the fake business. These include placing ads in online classifieds.

The business owner would respond to the mine that they could supply the desired item in the required quantities and their quote would be accepted. The mine would be quite happy to arrange for inspection of the goods, collect and pay immediately. So far so good. But this had to happen in a certain time period as the order was extremely urgent and a vehicle would be in the vicinity on a certain date to transport the items back to Zimbabwe.
The business owner would try and purchase the items from the supplier. The first glitch would be that the business owner doesn’t have an account at the fake supplier. The lead time from placing an order to delivery was also carefully crafted to just fit in with the expected date of inspection and collection by the fake mine. This put the business owner under extreme pressure with hardly any time to think logically. He would scurry around arranging the necessary funding, many times in the form of loans, to pay for the required items.
While communications were quick before delivery, the ordered items would never arrive and communications from the business owner would be ignored from this point on. The fake mine would equally go quiet. The business owner would be left out of pocket, many times financially compromised to the point of being forced to close his business, resulting in job losses. Attempts to trace the stolen money via the financial system would show it had been rapidly transferred out of reach in the delay between payment and the expected arrival date.
Evolution to the South African Tender Scam
The previous fraud execution required two sets of websites, a fake mine and a fake supplier. At some stage the tactics changed and it became popular to set up a spoof domain of a government department or a large corporation. No website was required for this spoof, only a working email address. The fraudsters would use this email address to send out fake RFQs, including a PDF document with the required items. Another questionnaire would accompany this where the tenderer had to supply all his business details and the business owners their personal details. This would lead to corporate and identity theft.
In a later refinement, the fraudsters would register two similar spoofing domains, one sending the fake RFQs, another for receiving the responses. The reason was that the sender domains are easily reported, causing disruptions between the fraudsters and their targets. Only upon closer inspection are the two domains revealed. Mitigating the second domain is much more tedious and the techniques exacting to obtain the required evidence for mitigation suitable for service providers.
The requested items would once again be available at exactly one supplier. In many cases a real business is spoofed by the fake supplier, sometimes the real business’s whole website is stolen. At other times the website is a mish-mash of content stolen from all over.
The rest of the scam ends up as before as in the Mining Supplies Scam.
A UDRP tells a tale of DNS abuse
In one case a fraudster not only stole the website of a company in the United States, Cornell Pump Company, he also registered a domain name to spoof them. Two crucial changes were made to the stolen content:
- The address was changed to a South African address
- An extra fictitious pump was added, a 8NNHM-SM Cortex-Prime
Cornell Pump Company became aware of this, and full credit to them, they decided to take action by launching a UDRP to take control of the domain cornellpumpsupply.com impersonating them.
The record of the successful challenge can be obtained here: http://www.wipo.int/amc/en/domains/search/text.jsp?case=D2017-1963
Some of the points in this process are pertinent to this post and highlighted here.
The Respondent is Emmanuel Dube, Conell of Johannesburg, South Africa.
…
The Respondent did not submit any response.
…
Additionally, the Respondent states that in the contact information for the registration of the Disputed Domain Name, the name of the registrant organization is “Conell” and indicates the registrant email is “conellpumps@….com” and submits that “Conell” appears identical to “Cornell” as the omission of the letter “r” by the Respondent is barely discernible. The Complainant submits that this is an obvious and intentional act by the Respondent to create the false impression that the Complainant is the owner of the Disputed Domain Name or that it is affiliated with the Complainant.
…
The Complainant states that, in conducting a reverse lookup of the physical addresses of the company locations listed by the Respondent, it was discovered that the addresses given are false, and no such “Cornell Pump Supply” offices exist at these locations and annexed evidence to support this.
It’s not uncommon for fraudsters of all types to abuse domains. They will use bogus names and address details to register these domain. The email addresses are typically hard to trace and the telephone numbers are disposable. In this case President Street in Johannesburg was used. This is quite commonly found in malicious domain registrations, along with other surrounding streets, where the domains are used for anything ranging from pet scams and commodity scams to tender scams. In these cases the respondent will never dare challenge a UDRP because he knows the domain name is being used for fraud.
The Complainant also states that it arranged for an investigator from its local counsel’s office in South Africa posing as a prospective customer to visit the address of the office allegedly located in Ndabeni, Cape Town, South Africa. Upon arrival, the investigator discovered there is no physical structure of any type located at the alleged location. It is a false address. The investigator visited all of the surrounding businesses, none of which were aware of the existence of a “Cornell Pump Supply”. The investigator also called the telephone number listed on the website. A woman answered the phone, and the investigator posing as a prospective customer requested directions to the store. The woman who answered was very vague and evasive, and repeatedly inquired as to the identity and company name of the caller. The woman then hung up. When the investigator called again, the woman hung up again, and did not answer any further calls.
Accordingly, the Complainant states, it is obvious that the Respondent has no intention of using the Disputed Domain Name in connection with bona fide sales of legitimate goods, but rather in a fraudulent and deceptive manner …
Cornell Pump Company needs to be commended for the effort they put in into trying to get to the bottom of this abuse. Unfortunately they were no more successful than many business owners and even law enforcement after the fraud is committed.
In a similar incident, a real business owner alerted us to people coming to collect boots for a “Defence Force tender” they had won and where they had paid the supplier, only to find the business doesn’t exist. At least one business was closed down in this case. Even the New Zealand ccTLD had been abused to create a fake manufacturer, using stolen content from a real manufacturer in Greece. Further the registrant email claimed different addresses and names in South Africa and New Zealand simulataneously.
Additionally, the Complainant submits, the Respondent slavishly copied the entire contents of the Complainant’s website, including use of the Complainant’s registered trademarks, copyrighted text and images, product brochures displaying the Complainant’s pumps incorporating the Complainant’s patented technology, and other proprietary information and material.
It states that the only information changed by the Respondent was with respect to sales contact information.
The was one more small change. Unfortunately the party looking did not have the relevant insight in what to look for, to spot the small addition; the extra 8NNHM-SM Cortex-Prime entry, our fake item.
Once the scammer lost access to this domain, he learnt from his mistakes and established his own fake brand – Gemstone Pumps. His initial malicious domain was gemstonepumps.com. This time our scammer changed his address to Cape Town for his domain registration, but still used the same stolen content from Cornell Pump Company, only changing the logo and address again.
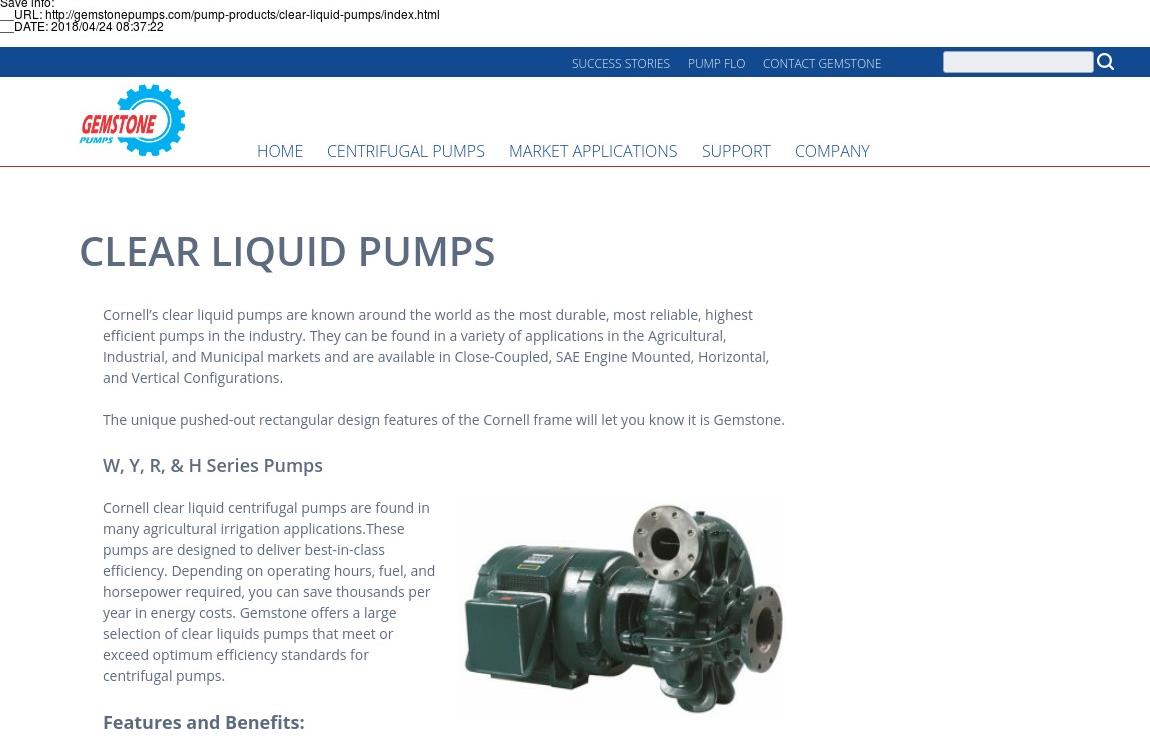
Since then, Gemstone Pumps has had many evolutions, using the stolen content while slowly adapting it on domain after domain from it’s Cornell spoof days:
- cornellpumpsupply.com – https://db.aa419.org/fakebanksview.php?key=130961
- gemstonepumps.com – https://db.aa419.org/fakebanksview.php?key=130960
- gemstonpumps.com – https://db.aa419.org/fakebanksview.php?key=133018
- gemstonpump.com – https://db.aa419.org/fakebanksview.php?key=137221
- gemstonepumps.com – https://db.aa419.org/fakebanksview.php?key=137280
Today gemstonepumps.com looks different to the stolen original content from Cornell. But knowing what you’re looking at, plus knowing a bit of it’s history, helps.
Remember 8NNHM-SM Cortex-Prime? Today a complete range of fake pumps exists with bespoke part numbers, but still the images and other specs stolen from Cornell!
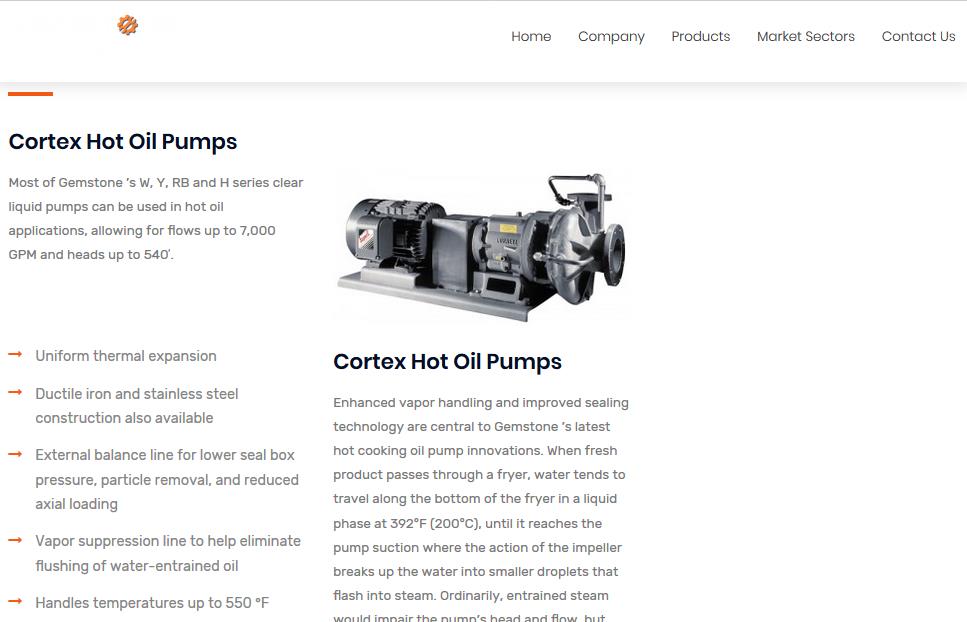
A quick check shows the real item to be the Cornell’s W, Y, RB and H series clear liquid pumps and not Coretex which is fictitious: https://cornellpump.com/pump-products/hot-oil-pumps/.
Hello South Africa’s Neighbours
Nobody is spared in this fraud. Most recently the Lesotho Electricity Company has been spoofed with domain lec-co.net, which is targeting businesses, asking for quotes on Flexicon 9800 Heavy Duty Pumps. This fictitious item is available at one company only, Grafton Engineering Pty Ltd on domain grafton.co.za. The real Lesotho Electricity Company can be found at https://www.lec.co.ls/
https://db.aa419.org/fakebanksview.php?key=140545
https://db.aa419.org/fakebanksview.php?key=140547
Behind this exposure is a story of businessmen banding together to save another business in Lesotho who thought they had lucked out with a large order. Only by consolidating the efforts of distinct industry experts, were they able to convince the would be victim he is being set up to lose his business. Sanity prevailed.
The Zambezi River Authority has not been spared either. It was slightly more complex discerning here who was real, who was not. A business owner might have been deceived into believing the imposter is the real one.
A business received an RFQ from supplychain@bghes.org requesting pricing on:
NPH-5200BH Vortex Lift Chain
NPH-4300RX Vortex Lift Chain
NPH-7160XV Vortex Lift Chain
Vortex Flow Meter FDR 13844MM Series
These items can only be found at vortexhydro.co.za. But there’s a catch. These items, while shown as technical drawings on the associated website, are actually edited images from Ingersoll Rand: https://www.ingersollrandproducts.com/. But it gets worse. The website appears extremely professional, but no match can be found online for the source. Yet if we understand all the red flags, we know something is wrong. It’s only after using numerous non-standard search techniques that we uncover the source of the stolen website to be http://vortex-hydro.com/, but it’s not resolving and the website is in-operational. We can however see it on the Internet Archive at https://web.archive.org/web/20190312003024/http://vortex-hydro.com/. Some content was added that was stolen from http://www.tewapower.co.za/ to “localize” it. This is much as we saw in the previous cases.
We mentioned the confusion as to which might be the real Zambezi River Authority. Domain name bghes.org was registered on 2017-09-02, domain zambezira.org was registered on 2018-03-14. This would indicate bghes.org to be the correct one. Wrong! Understanding all the red flags, we are prompted to dig deeper. The orginal domain for The Zambezi River Authority was zaraho.org.zm registered 2013-03-14. While the domain name still exists, it now directly redirects to zambezira.org.
<!DOCTYPE HTML PUBLIC "-//IETF//DTD HTML 2.0//EN"> <html><head> <title>301 Moved Permanently</title> </head><body> <h1>Moved Permanently</h1> <p>The document has moved <a href="http://zambezira.org/">here</a>.</p> </body></html>
Our clue is the email address info<@>zaraho.org.zm at http://www.zambezira.org/contact-us. This also illustrates why brand affinity is important, even in the domain name space.
https://db.aa419.org/fakebanksview.php?key=140512
https://db.aa419.org/fakebanksview.php?key=140513
New Evolution – The Tender Scam visits Europe
Artists Against 419 was surprised to learn from a business in the United Kingdom that had been defrauded in a tender scam.
I would like to advise that the Gemstonpump website is still active and we have been scammed by them this week.
Checks on the fake supplier revealed it to be the same actor that had been targeting South African business – the previously mentioned Gemstone Pumps! This was a major red flag.
More was to come. On 4 Jun 2019 an Italian pump manufacturer, Pumps, took to Twitter to warn the public that their website had been stolen and was being used to defraud other businesses. At https://twitter.com/GemmeCotti/status/1135930534423666688 we see:
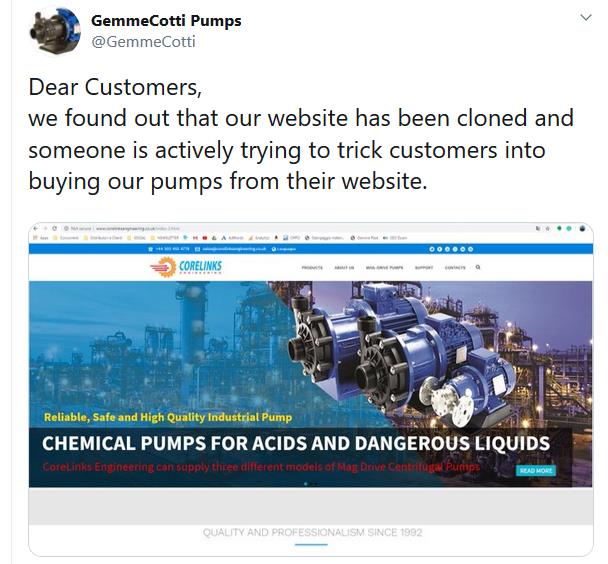
Dear Customers, we found out that our website has been cloned and someone is actively trying to trick customers into buying our pumps from their website.
This fake company, Corelinks Engineering, is listed in a website that warns against 419-scam websites because they have already defrauded another pump manufacturer.
They produce offers when they are contacted, they ask for payment in advance but then, of course, they don’t deliver the products.
This scam has been reported to British Police and we are taking all the necessary measures in Italy ourselves. Please watch out for this and if you hear of someone dealing with this company spread the word.
It’s no suprise to know that corelinksengineering.co.uk has a predecessor, corelinkspump.com. Nor should it be to discover that it can be proven that the same party that is behnd this fraud, is the same party as behind the Gemstone/Cornell incidents.
Nothing empowers criminals like success. Having successfully spoofed South African government departments and defrauding South African businesses with impunity, stolen content and even allowed back at the same registrars who had been alerted to them, these actors took to targeting businesses in the European Union in 2019.
A new twist in 2023
2023 started off with a bang for South African based tender scams. Users were complaining, asking how an official .gov.za could be used on Twitter in response to a Department of Home Affairs alert at https://twitter.com/HomeAffairsSA/status/1624636511617445889.
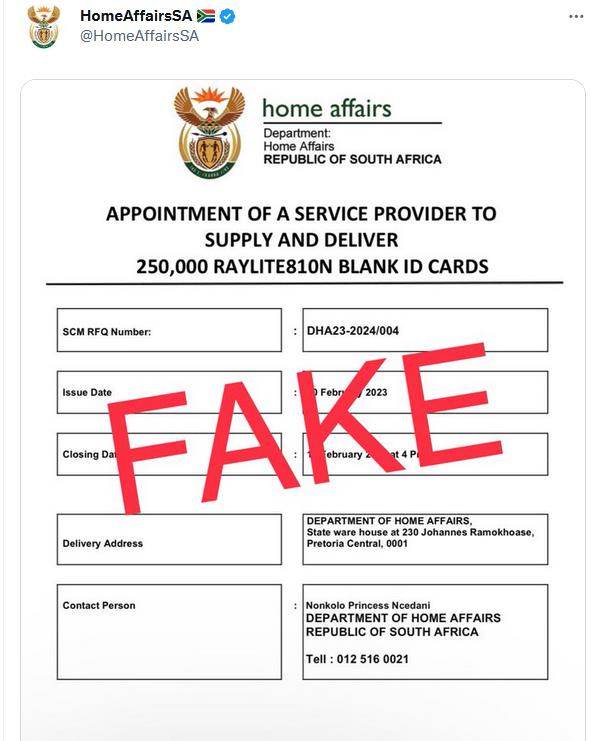
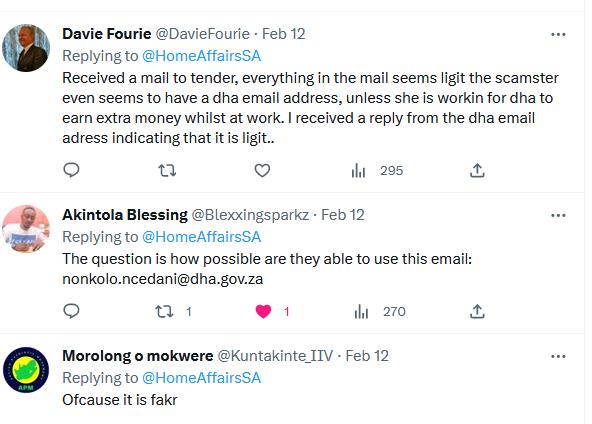
Any reasonable ITSec investigator would assume this to just be a spoof and users Davie and Akintola falling for the scam. Any reasonable ITSec investigator would be wrong.
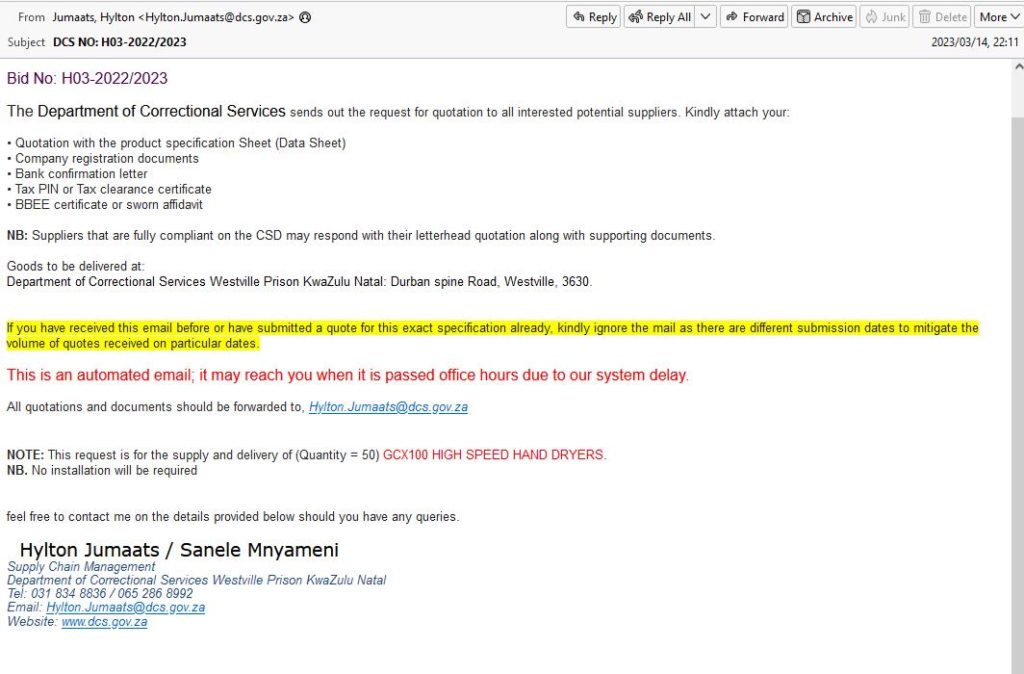
Artists Against 419 managed to obtain a raw email. More surprising is that we saw that not only was the Department of Homes Affairs dha.gov.za domain being abused, it also revealed a second government domain was also being abused, dcs.gov.za. Artists Against 419 alerted the authorities immediately.
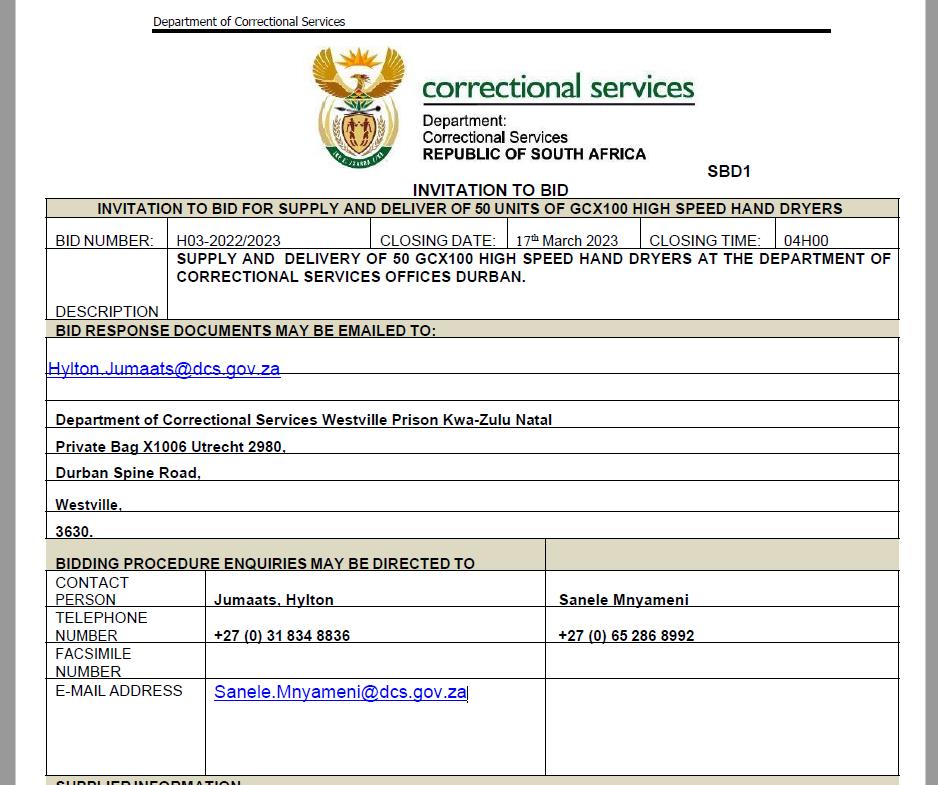
On 18 March 2023 we received yet another raw tender scam email. Incredulous at what we were seeing, we reached out to a well known reputable party in cyber forensics who kindly offered up his time to confirm what we could not believe, fraudsters were sending out scam emails via the Department of Correctional Services domain. It was clear we were seeing a new evolution in the tender scam:
- Initially two fake websites were created, published on two separate domains,
- Later this evolved to one of the domains spoofing a government department with no content.
- The newest evolution was abusing a real ZA Government domain and sending out fraudulent RFQs this way.
All the work IT Security experts had put into SPF, DKIM and DMARC was now useless. Fraudsters had achieved the wet dream of any fraudster, the ability to defraud using an official government domain behind a reputable email security provider, guaranteeing the emails would be white listed, ensuring a more efficient and successful targeting of South Africans. More so, respondents are being asked for personal details, something considered PII, using resources of the South African government.
Received: from securemail-y55.synaq.com ([196.35.198.122])
Email header
by dedi436.nur4.host-h.net with esmtps (TLS1.3:ECDHE_RSA_AES_256_GCM_SHA384:256)
(Exim 4.92)
(envelope-from <(redacted)@dcs.gov.za>)
id 1pcB48-0006NT-96
for (redacted)@(redacted); Tue, 14 Mar 2023 22:16:23 +0200
Considering suspects had long since been identified, at least one actor extremely proficient in all things DNS and security related, another extremely proficient in procurement processes, yet nothing ever happened since 2015, we are not really shocked to see the latest evolution. It’s only a natural progression of what fraudsters will do when they operate in a fraud tolerant system where a government has no real cyber security posture.
The relevant authorities were alerted and details captured in our database entry https://db.aa419.org/fakebanksview.php?key=160573
Conclusion
The South African Tender Scam has grown to spoof businesses and governments with impunity. It’s reach is now also international. While this isn’t a new type of fraud, being well known in the South African business space, it has expanded outside the borders of South Africa. Already these fraudsters have caused losses abroad and we can be certain, having tasted success, they will continue this onslaught against small businesses expanding worldwide.