Looking back at 2017
2017 was a disastrous year for the consumer in the cyber fraud arena and we saw a lot happening.
It’s all to easy looking at numbers such as our 2017 statistics, not realizing what they represent. This period was a virtual war where consumers lost their livelihoods after being defrauded, the numbers represent futures lost, the undermining of one of the marvels of the 21st century, the internet. Behind each increase in count, we find misery multiplied. These are directly linked to media reports of an all time high in BEC, fraud and losses to the amount of billions of dollars. Most of those crimes goes unpunished, once the money is gone, it’s gone forever. Many such victims are elderly and has no way of ever recovering.
Before delving into some of the issues and cases, let’s first look at those numbers.
The following represents the top abused registrars we recorded. It’s a sad fact that abuse is part of the internet and proactively stopping such abuse is near impossible. These numbers should not be seen as painting a complete picture or any condemnation of a registrar, rather the initial starting point the abusers used in attempting fraud; the blank canvas on which we paint the complete picture. It’s how long this fraud is allowed to flourish that counts.
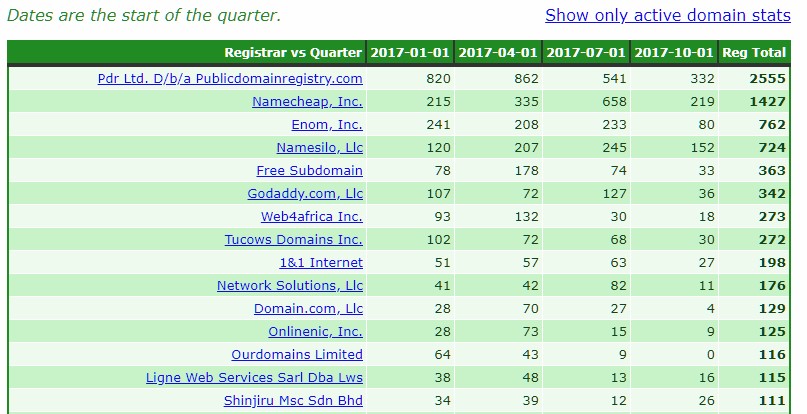
If we look at the domains that were active at the end of 2017, still defrauding consumers, we now have the picture on the previous canvas:
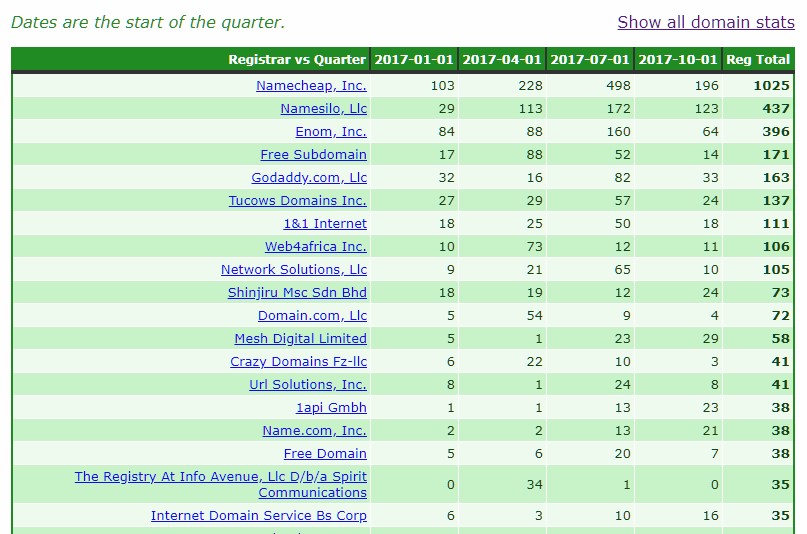
Suddenly we have visibility on the registrar heroes and the problem children. PDR Ltd, disappeared totally, Namecheap, Inc is right at the top. Bear in mind these totals only reflects an accumulation of domains registered in 2017. There are domains since 2016, 2015 and even 2014 still defrauding on Namecheap. Think in terms of active fraud days, the time the consumer trap is set to defraud.
* Pdr Ltd. D/b/a Publicdomainregistry.com: They drop right off the list. In fact they ended up with a total of zero known abusive domains all around. PDR has long since shown they do not tolerate abuse and specifically not advance fee fraud. While their market may be problematic as it includes vast regions of Africa, they themselves do not carry this problem on to the consumer. The typical lifetime of an abusive domain is less than a day once identified. This in turn results in domain churn, where the fraudster may attempt to register the same domain many times, using variations. However, once identified, the result is a big no! This registrar wins the Socially Responsible Company of the Year Award in our books!
But not all registrars are born equal.
* Namecheap, Inc.: This registrar has done more than any other registrar to empower advance fee fraudsters in 2017, refusing to understand that advance fee fraud is a domain based fraud despite irrefutable proof provided to them. Due to issues with their associated WhoisGuard proxy protection, as can be seen on WebHosting Talk here and here, they changed to a model of default free proxy protection for all registrants where possible upon registration. This created the perfect environment for parties intent on defrauding consumers, virtual anonymity. This is significant as Namecheap had previously little real willingness or ability to investigate patently fake registration details, something that continued into 2017 in the .US namespace. Apparently fraud was not the only abuse seen where Whoisguard proxy services were used, this most certainly reflected our own experience and resulted in a generic block on certain nTLDs. Numerous of the malicious domains registered via Namecheap where also had to be mitigated at registry level. This is telling. Even now Neustar, the registry operator for the .US ccTLD on behalf of the US NTIA, has been left a massive can of worms by Namecheap’s fraud tolerance (more shortly).
* Namesilo, LLC: Namesilo accumulated many long lived bad apples from West Africa. These included some very nasty scams that targets the most vulnerable of consumers in a time they can afford it least. Namesilo made sure they remained unapproachable to serious abuse issues. Namesilo insists all abuse complaints are lodged via their webform. However their web form sends no acknowledgement, leaving the reporter with no evidence of submitting a report. To make matters worse, they insist they never received such a report if an issue is escalated. Perfect plausibility (and bad practice harming the consumer). However an analysis of the badness shows more than 60% of the badness originates via their one reseller, QHoster. This figure may well be much higher as some TLDs appear to not be showing the reseller tag. Where WHOIS data was available and not hidden behind the Namesilo associated PrivacyGuardian.org proxy services (with the same deficient report web form reporting), the quality of data was atrocious and not in line with the policies set in the ICANN RAA and clearly not verified. Ironically this has was the subject of a 2016 ICANN compliance complaint lodged in 2016 and closed as resolved. Many of the 2017 issues was a mere continuation of fraud and fake WHOIS mentioned in the 2016 ICANN Compliance complaint, much even attributable to the same syndicate massively spoofing Citibank, the Reserve Bank of India, US attorneys and companies etc.
* Enom, Inc: Much of the badness recorded sponsored via Enom was actually based upon domains registered prior to 2017, attributable to Namecheap. Since being bought out by Tucows, there has been some background issues that makes real domain based fraud attribution difficult (see links below). As such we leave attribution as sponsoring registrar. But even where we discount those, response from Enom has evoked mixed feeling on the mixed responses. Enom has been quick to stop abuse in some instances, but as has been discovered in a recent incident, they are willing to surgically attempt to separate domain registration issues and the fraud committed with such a domain. However time will tell how their abuse response crystallizes out.
References:
https://domainnamewire.com/2017/09/01/namecheap-sues-enom-tucows-demands-transfer-4-million-domains/
https://domainnamewire.com/2017/09/25/tucows-responds-namecheaps-lawsuit-transfers/
https://domainnamewire.com/2017/10/24/namecheap-drops-lawsuit-tucows/
https://status.namecheap.com/archives/35574
* Shinjiru Msc Sdn Bhd: This small registrar, trading as Ilovewww.com, has become the go-to guys for fraudsters from all areas of West Africa; Benin, Nigeria and the Cameroon. They allow blatantly incomplete low quality registration details into the registries. We see massive syndicate activity on their services (and hosting). One such group ties in with the syndicate mention in the Namesilo discussion. It was also reported to ICANN Compliance in a complaint in 2016, with the same effect. This complaint was eventually escalated to the ICANN Ombudsman with little effect. One major issue seen in 2017 defrauding consumers from their services, was in effect a continuation of issues raised in 2016. Trying to surgically isolate fake WHOIS details and abuse is a distinct denial of realities we see in fraud and abuse in general. This resulted in parties such as the Benin Loan Scammers targeting Europe, now migrating to them. Their typical response when reporting fake registration details, is “We will investigate this case and take necessary action is the domain info is confirmed invalid.” (such evidence was provided). The last query about them doing nothing despite this promise resulted in:
“If you have concerns about the content of a website, you should address your complaint to the site’s author, or the applicable Internet Service Provider depending on the circumstances. If you believe that the content is of an illegal nature, you should contact an appropriate law enforcement agency (which will vary depending on jurisdiction) or consult an attorney for legal advice.”.
The site’s author is the problem! How many ways can you pass the buck? What happened to ICANN RAA contractual promises to promptly investigate WHOIS issues? Especially when presented with evidence where the same party changes names, New York is in South Africa, we see telephone numbers impossible to verify since they are invalid – all at odds with the ICANN RAA 2013 specifications!
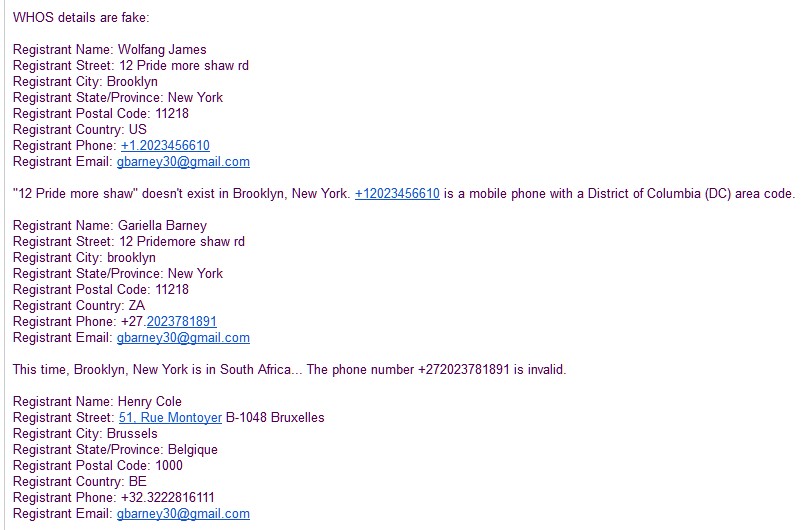
That’s how ridiculous Shinjiru’s response get to this obvious issue. Yet these domains like these are targeting Europe, the USA, India and the Far East, the whole world. No wonder we see the badness migrate to Shinjiru aka IloveWWW.com! Fraud and stolen money migrates to where it get’s Ilovewww’ed.
PS: A big shout out to all you New Yorkers, how is the weather in South Africa this time of the year?!
The other registrars are doing well more or less, but some are opening the door to mass abuse.
Special mentions:
* Godaddy.com, LLC: Godaddy is the world’s largest registrar. So in reality they are doing pretty well in keeping the total percentage of fraudulent domains sponsored via them relatively low. However their mitigation time is extremely varying. This may be due to underlying issues and or complexity. Some of the channels could be improved, but in general, Godaddy gets the tick in the box for attempting to mitigate abuse on their services.
On a negative note, Godaddy has started making it extremely difficult to investigate any abuse of domains sponsored via them. They started applying blanket blocks across large ranges of IP addresses. This has been the issue of complaints from various anti-abuse group, also to ICANN. 2017 ended off with some rather caustic comments in some anti-abuse sectors aimed at both Godaddy and ICANN. While we can accept, would in fact commend, any attempt at rate limiting scraping of WHOIS databases, this is not how Godaddy’s blocking is working. There is a difference between rate limiting and blocking. At this stage the Godaddy deemed cure is worse than the cancer. This is facilitating abuse by hampering an extremely small group of dedicated finite number of abuse mitigators, resulting in an unsafer internet. Policies are set for a reason! Nobody should ever have to say this to a parent, but at this stage we can’t get past it: Godaddy, you have an ugly child!
Dreamhost, Llc: A non-mention of DreamHost would be an insult to a lot of hard work done by them. Dreamhost had a massive problem with fraudulent domains in the 2015 time frame. They silently started taking a no-prisoners approach to abuse of their services. While they are not totally free from these parties, they have most certainly proven that fraud migrates away from where it’s not tolerated. Well done to the Dreamhost abuse team!
Ligne Web Services Sarl Dba Lws: A special shout out goes to LWS. We saw their services invaded by the Benin Loan Scammers. Where they were alerted to this abuse, their reaction was prompt. The message was clear: Not on our watch! Bien joué!
We could go on with public thank you’s. There was massive support to stop abuse.
Looking at the TLDs, we get a clearer picture of what is happening in the abuse vs anti-abuse world.
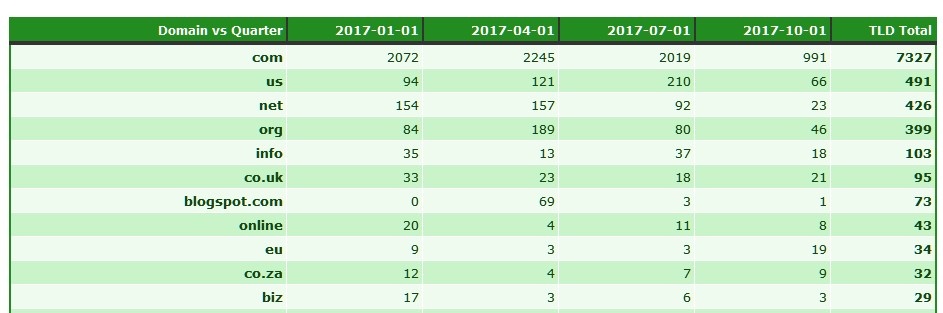
As expected, the .COM TLD is still massively abused. However the uninformed would be surprised to see the second most abused TLD, was the .US! Why was this?
Look no further than Namecheap:
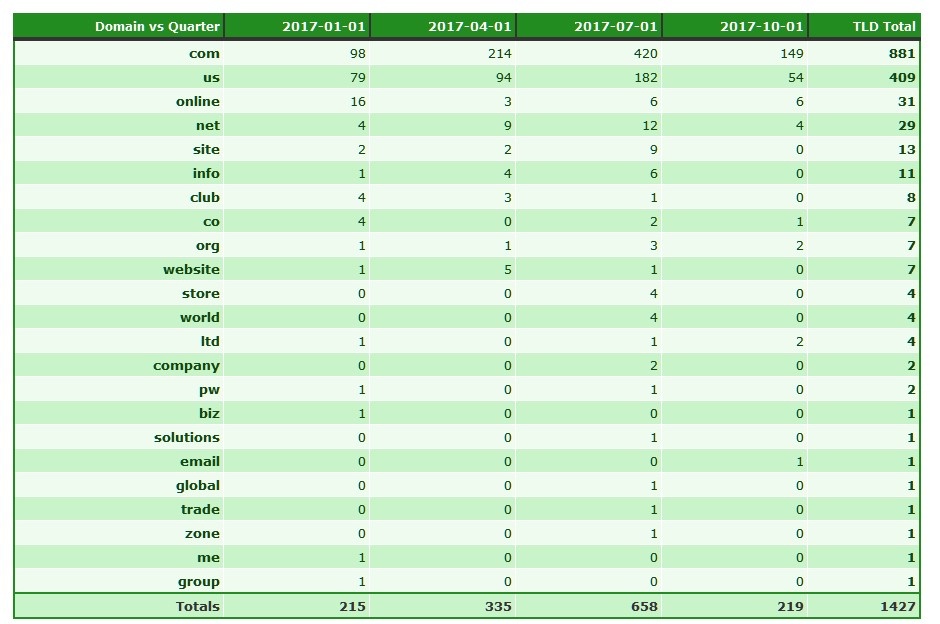
Here we see the TLDs abused where Namecheap was the sponsoring registrar; the .US anomaly is attributable their client base. We see of the 491 recorded .US domains, 409 were sponsored via Namecheap, that is over 83% of the recorded fraudulent websites in the .US TLD we recorded. More disconcerting is the number of these domains still active in one way or another:
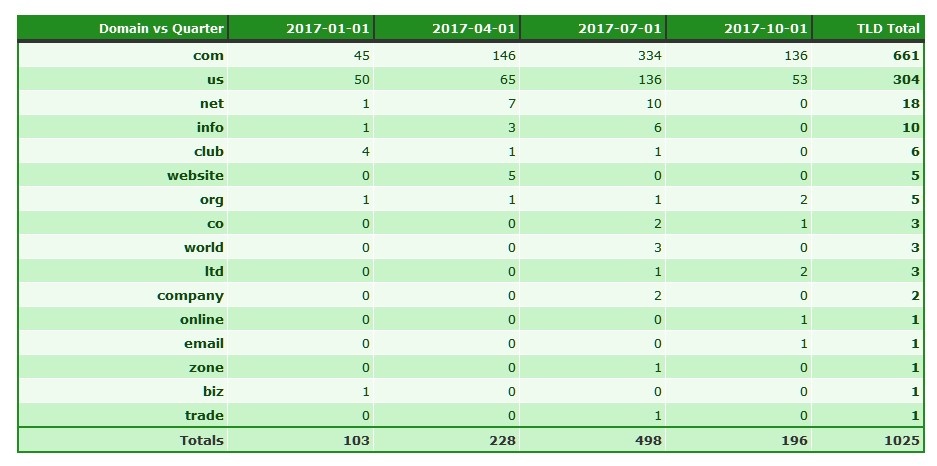
The understand the .US abuse, we have to start off with the US Better Business Bureau investigation into pet scams: https://www.bbb.org/puppyscam/. This report details how scammers target consumers all around the world. When Steve Baker initiated his investigation, he reached out to various parties, looking for clues. Artists Against 419 warned him he was opening the lid on a massive can of worms, Cameroonian scams and all it leads to; Pet scams, drug scams, courier scams, fake passport/visa/license/IETLS/TOEFL scams, black money scams, extortion etc. He probably thought we were daft. We pointed out one such party that was of interest to him, a certain prolific scammer using the email address registrant melaneeter@gmail.com.
Consider domain freelancerdocumentproducers.com at Registrar 1 & 1:
Domain Name: freelancerdocumentproducers.com
Registry Domain ID: 2051417416_DOMAIN_COM-VRSN
Registrar WHOIS Server: whois.1and1.com
Registrar URL: http://1and1.com
Updated Date: 2017-09-21T04:55:25.000Z
Creation Date: 2016-08-11T17:13:08.000Z
Registrar Registration Expiration Date: 2018-08-11T17:13:08.000Z
Registrar: 1&1 Internet SE
Registrar IANA ID: 83
Registrar Abuse Contact Email: abuse@1and1.com
Registrar Abuse Contact Phone: +1.8774612631
Reseller:
Domain Status: ok https://www.icann.org/epp#ok
Domain Status: autoRenewPeriod https://www.icann.org/epp#autoRenewPeriod
Registry Registrant ID:
Registrant Name: Ngwa Cole Shu
Registrant Organization: freelancer document producers
Registrant Street: Com avenue
Registrant Street:
Registrant City: Bamenda
Registrant State/Province:
Registrant Postal Code: 00237
Registrant Country: CM
Registrant Phone: +237.670510430
Registrant Phone Ext:
Registrant Fax:
Registrant Fax Ext:
Registrant Email: melaneeter@gmail.com
Versus the registration for antoniopitbullpuppies.us and cuteteacupyorkies.us at Namecheap:
Domain Name: cuteteacupyorkies.us Registry Domain ID: D58176252-US Registrar WHOIS Server: whois.namecheap.com Registrar URL: http://www.namecheap.com Updated Date: 2017-02-04T00:09:20Z Creation Date: 2017-01-27T11:40:22Z Registry Expiry Date: 2018-01-26T23:59:59Z ... Registry Registrant ID: C58176248-US Registrant Name: Bren Walters Registrant Organization: Cute Yorkies Registrant Street: 300 West Fitzhugh, |
Domain Name: antoniopitbullpuppies.us
Registry Domain ID: D59027444-US
Registrar WHOIS Server: whois.namecheap.com
Registrar URL: http://www.namecheap.com
Updated Date: 2017-03-24T13:59:22Z
Creation Date: 2017-03-24T02:47:41Z
Registry Expiry Date: 2018-03-23T23:59:59Z
...
Registry Registrant ID: C59027442-US
Registrant Name: soney sky
Registrant Organization: Global Escrow
Registrant Street: 20241 madison av
...
Registrant City: new york
Registrant State/Province: NY
Registrant Postal Code: 10001
Registrant Country: US
Registrant Phone: +1.9703358289
...
Registrant Email: melaneeter@gmail.com
Registrant Application Purpose: P1
Registrant Nexus Category: C11
|
Reports to Namecheap regarding fraud and fake WHOIS on 61 domains (Namecheap Ticket ID: VAS-767-35329), resulted in:
Please respond to this email with evidence of the specific contact information you have found to be invalid on the Whois records for the reported domain names. Examples would be a bounced email or postal mail returned due to an invalid address. If you have a bounced email, please copy and paste it to your reply. In the case of returned postal mail, please scan it converting into a PDF file and send to us via email.
While the domain names do have Namecheap.com as the registrar, we cannot oversee the data being transmitted through their websites. We do not own the domain names mentioned in your complaint, we are simply the company the domain names were registered with.
The issue would need to be addressed through the hosting provider to see if their terms of service are violated. We have no way to solve such issues as we do not control the hosting company in this instance.
In this case the hoster is bullet proof cyber crime laden web hoster Swiftslots. Once again we see the abuse and WHOIS issues separation. Never mind that this is merely two sides of the same coin. Never mind that a quick check on the national USPS or even Google maps (if you want pretty pictures) shows that no 20241 Madison Ave exists, the number is way too high. Never mind that this party has other domains with these fake registrations. Never mind that is was reported to you, you chose to ignore everything. Nobody is as blind as he that does not wish to see, a.k.a. self blinding. Whatever happened to due care? Sadly many of these domains are still active and defrauding, ever since this reply .
Meanwhile, as the US BBB investigation progressed, we saw some interesting arrests in the USA that is also shared in the BBB report:
In May 2017 three Cameroonian students at Slippery Rock University in Pennsylvania were criminally charged with operating a pet fraud. Boxer puppies were advertised on Craigslist around the country, and news reports indicate that the Defendants collected tens of thousands of dollars from victims. Two people are in
custody, and a third has not yet been apprehended.A man from Cameroon was arrested and charged in December 2016 in Charlotte, North Carolina. He is alleged to have picked up more than half a million dollars, keeping part of it and sending the rest to Cameroon.
In May 2016 a woman from Cameroon was arrested in Lehi, Utah. She was picking up money from pet fraud victims at a Western Union branch, and reportedly had 15 different fraudulent driver’s licenses.
In addition, two Cameroonians were recently indicted in the District of Kansas and charged with wire fraud and taking part in an international conspiracy which included pet fraud. Their role was picking up money sent by fraud victims at Western Union and MoneyGram outlets. Rodriech Nyugab Nkarawki is alleged to have used six different aliases in his efforts, and Gladys Nkome had 23. Some of their advertising is alleged to have taken place on You Tube. In addition to obtaining money for Yorkies and bulldogs, the two are alleged to have also offered to sell illegal identification documents such as passports, and also medications, prescription drugs, automobiles and chemicals.
It is .US domains being abused for these types of fraud, which accounts for the .US ccTLD anomaly. In summary, Cameroonian scammers are abusing the .US ccTLD to target Americans in fraud, while an American Registrar manned mostly by staff in the Ukraine (it’s no secret), self blind to these issues. And where we move outside the .US ccTLD, we find these fake details hidden by Namecheap’s subsidiary registered in Panama (a trick learnt from their Heihachi reseller a few years ago) to provide a proxy protection, also for such obvious fraud. We also see their reaction and blatant non-adherence of their stated policies in another incident, also verified after an interview with the victim and mentioned in the US BBB pet scam report.
But it gets worse. We ended off the year with a complaint that was rather disturbing, reported on our forums: http://forum.aa419.org/viewtopic.php?f=50&t=88199
In a nutshell, a cancer patient was targeted in a marijuana scam. The victim had gone through the needed steps to obtain a medical card, the needed permission to legally buy marijuana for medical purposes. This incident was also reported to the US BBB, IC3 and the victims local law authorities. Domain anncannamed.com was registered via Namecheap with proxy provider being WhoisGuard. The associated fraudulent website claims to be located at Clawson, Michigan, 48017, USA. As was pointed out to Namecheap Legal and Abuse in their ticket ##XJD-406-10000, the brands of FedEx and UPS are being abused as so called sleuth shippers for marijuana. Further, also as pointed out to Namecheap, selling Marijuana is totally illegal in Michigan. Ditto Australia where this fraudster claimed to be shipping marijuana to. Some of the other issues also uncovered a part of this scam nest is at the thread posted on the Artists Against 419 forums.
The same scam also defrauded at least two other victims. However this fraud took on a new dimension, extortion! After the victim purchased marijuana loosing his money, a spoofing FedEx using email address fedex@fedex-express.us sent him a fake waybill. Shortly after this the shipment was put on hold. The authorities were now all over this for contravention of drug laws. Pay up! This is exactly what the US Drug Enforcement Agency is warning about here: https://www.deadiversion.usdoj.gov/pubs/pressreleases/extortion_scam.htm
Digging into the circumstances surrounding this incident and other associated domain has now led to a massive nest of over 100 defrauding domains, ranging from pet scams to drugs scams. The impact is international. No guessing needed as to who the sponsoring registrar is: Namecheap. Also no surprise that on some, they refused to take action previously, forcing this to a hosting mitigation scenario. Unfortunately, with reseller pollution, this resulted in this syndicate’s domain shattering across numerous hosting providers to be stronger than even, retaining their investment made in massive SEO spamming of fake non-existent products, undermining any mitigation attempt. Mitigating domain propagated fraud like advance fee fraud at hosting level is the worst advice any responsible registrar can ever give.
In summary, Namecheap is allowing a new Heihachi, but this time unleashed on American consumer and business, indeed also the world, but magnitudes or orders more difficult to mitigate.
We also have a syndicate serially sourcing domains from Namesilo and Namecheap. This was mentioned before in the respective discussion on these registrars. Using analytical methods, it’s possible to prove massive fraud. Banks are being spoofed, US attorneys are being spoofed, The Reserve Bank of India is being spoofed, WhatsApp was spoofed … the list is incredible. This syndicates illustrates why the UDRP procedure in the face of fraud is not the appropriate tool. It turns the complainant into a piggy bank with no hope that this will yield any relief when the sponsoring registrar allows blatantly fictitious data into the registries via their services fo rmalicious registries. This syndicate has seen at least one UDRP from Statoil, one UDRP from Actelion Pharmaceuticals, Ltd Corporation Switzerland. Societe Generale lodged two UDRPs against this syndicate, one for ssgciib.com and one for cibsocietegenerale.com. No sooner did they win the last, than the same malicious registrant promptly registered a new Societe Generale spoof domain at Namesilo. This essentially makes a mockery of due process. So far we have 21 recorded spoofs of Citibank, 111 spoofs of the Reserve Bank of India, 17 spoofs of the Royal Bank of Scotland etc. So Societe Generale should not feel bad upon reading this. They are as much a victim of fraud tolerant registrars as the consumers these fraudsters target, while these registrars claim to be “Only a Registrar”, whatever that means, since we have an extremely clear wording regarding in a contract singed with ICANN, called the Registrar Accreditation Agreement of 2013. But these registrars are willing to leave abuse unhindered while it does not hurt them.
The dark side here also highlighted some beacons of hope. Registry PIR took action and put numerous .org domains on serverHold. Radix also took action where fraud was in their registries. This accounts for many non-active domains in the fraud tolerant registrars’ count. Well done to you!
Certain registrars and registries stepped up to the plate in 2017. You know who you are. It would be impossible to thank you all individually. But thank you!
For those “We are only a registrar” types self blinding: Registrars not mentioned like 1API in Ticket#2017111642013602, when faced with undeniable self incriminating evidence from the registrant and grossly fake whois details, while the domains are being abused in fraud.
With another certain old registrar in the EU where we eventually agreed on what a registrar is as per ICANN definitions, not what was initially said and done is in a well known vehicle escrow fraud targeting Canada, where fake WHOIS details was proven, including an email from the legitimate owner of the street address (even though easily publicly verifiable from public sources), where the registrar having certain victim details and bank account details used for money laundering as evidence – then sent this to their ‘client‘ with fake registration details in Eastern Europe (the same party who incidentally also massively uses Namecheap).
Reg.ru, you not only have a nasty West African nest defrauding the Western world, you also have them defrauding your own people. We’re not sure which policies you adhere to since they are most definitely not ICANN policies, much as you claim so. We are still trying to discover your ICANN mandated proxy policies, since you stated as much to ICANN. Numerous Russian speaking people have also checked, they seem AWOL?
You guys are going to be a problem for the EU as much as for the world with the coming GDPR, where you gladly accept any registration as long as the money is good, yet not wiling to take due care and are willing to game published policies, causing massive consumer harm. Policies were made for a reason. Is this is why some of you are so vehement in you support for blanket domain privacy, where your procedures are not open to public scrutiny? If you really cared about consumers, as the GDPR is intended, your stance would have been drastically different.
To the casual consumer reading this: There be dragons out there, on the net, tread carefully. All is not what it seems. Eye candy and tokenism abounds when it comes to policies mandated but not followed.
To any rights holder mentioned here being spoofed: Our evidence is yours to defend your rights.
To any law enforcement agency seeking evidence of what is being said here: just ask.
To the anti-abuse community: Thank you for your support and information. Each verified report in our database makes the world slightly safer.
Once again to all the abuse representatives that took there duties seriously in 2017: thank you!
Wishing all you folks a very prosperous 2018!