AA419 DDoS: India’s Crisis with Cyber Security
The DDoS against AA419 is still ongoing. One issue that became clear early on in the DDoS, was that numerous botnets were attacking the AA419 web server.
Also extremely noticeable was that the bulk of the attack traffic was coming from India. As such we contacted CERT in India.
CERT India’s response was extremely quick, thanks to the marvels of electronic communication. They read our email within minutes of it being sent. We knew this based upon a read notify I had put on the email. Sadly that is where it stopped. From the 28th of March 2011 to date they have not even had the common courtesy to reply.
This left us with a difficult decision:
Do we take a blanket approach to minimize the damage to the rest of the world and simply block Indian ISPs?
Do we take a blanket approach to minimize the damage to the rest of the world and simply block Indian ISPs?
While that would make a lot of sense, we also need to consider that India is one of the the most highly targeted countries in West African fraud. Artists Against 419 needs to make the Indian public aware of scam sites that may potentially be targeting them. As such our website will be reachable, despite CERT India’s silence.
If it sounds like we are unfairly singling out a country, judge for yourself.
Bot overview
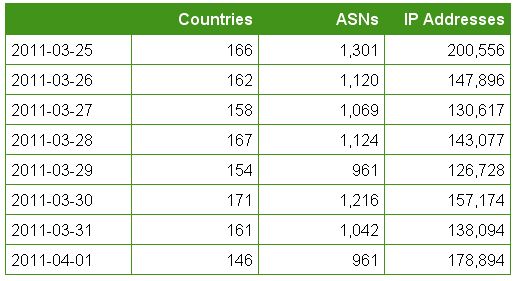
Initially when we went live on the new server, we had a lot of work to do to mitigate the attack. One noticeable aspect is their is no correlation between the number of attackers versus countries they are coming from.
Despite the 1st of April having the lowest originating countries for the attacking bots, it shows the second highest number of attackers for the day.
Bots by Region
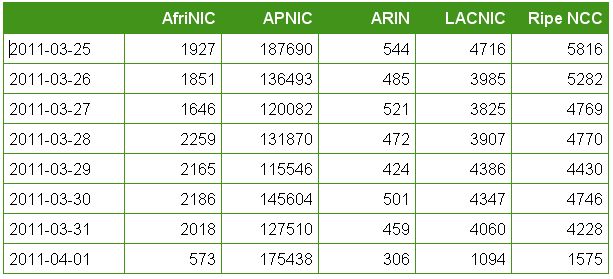
Looking at the attacking systems, one experiences an optical illusion looking at the APNIC column. The column is not narrower than the rest.
We clearly see the majority of the systems attacking us are coming from the APNIC region. Let us drill down into the APNIC region.
Bots by Country
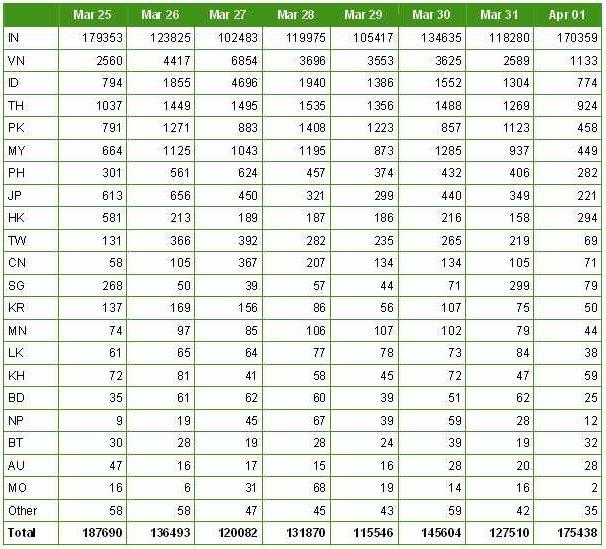
This is quite shocking. We immediately see we have a serious issue with attacking systems coming from India. The number of bots from India are two orders of magnitude larger than any from any other country in this region. In fact on average 90% of all attacking IP addresses are coming from India.
A Reality Check
Apart from the attempt to disrupt the activities of AA419, we should remember that the systems being used for this botnet:
- are also attacking other servers, trying to disrupt them (it has been verified)
- are not really under the owner’s control, but comprised and under the malicious control of some other unknown third party
- poses a security risk to India and the rest of the world. We do not know what data on these systems has been compromised. Remember, these same systems may also be used to access bank accounts, government infrastructure, manage outsourced tasks or potentially access other sensitive infrastructure. Any system accessed from them is also potentially at risk.
All we can say to CERT India is that you are failing dismally in your mission:
Mission
To enhance the security of India’s Communications and Information Infrastructure through proactive action and effective collaboration.
Here is the evidence you read the message that was sent to you with details:
This is a message receipt notification. The message sent on Mon Mar 28 2011 13:41:07 GMT+0530 (India Standard Time) to incident@cert-in.org.in with subject "Anybody from CERT India" has been displayed on the recipient's computer.
AA419 will have to seek to address the issue via other methods.