Malicious Domains: Heroes and Facilitators
In a new pending report from the United States Better Business Bureau, they are looking at a new plague that’s hit the United States and the world. While we will not steal their thunder in this most excellent report and the revelations contained in it, it does illustrate certain underlying issues, malicious domains controlled from West Africa. Let’s get some facts straight:
A domain registered by a malicious party for malicious purposes, is malicious.
This is simple undeniable logic. Such a domain has no right of existence outside it’s malicious usage and this is why it’s called a malicious domain. If the malicious actor uses this domain to point to malicious content to defraud consumers, this is not merely a hosting issue. Should an abuse report be received by the hosting provider and he suspends the content, the malicious party can rapidly redirect the domain to a new hosting account. The malicious actor spends a considerable amount of time and energy in establishing this domain name. Hosting is secondary to this. The only real relief in 419 and related West African fraud is a domain suspension.
The problem: #1 – ICANN
However, this is not what ICANN and certain registrars would have us believe. It’s ICANN’s contention that the domain is harmless in this process. Is this true?
Let’s consider example domain unicef-online.com. This 419-scam domain was deliberately chosen for numerous reasons, but let’s first look at the obvious issues.
It’s being abused to spoof the legitimate United Nations Children’s Fund at https://www.unicef.org/ with content stolen from it. This content is then abused in 419 fraud. Understanding this is important. We have copyright and trademark issues and we have fraud. The deception stas at the choice of the domain name, unicef-online.com. The United Nations is an innocent party whose content has been stolen, then used by the malicious party to defraud casual innocent internet users. We have two sets of victims, both the United Nations and the consumer.
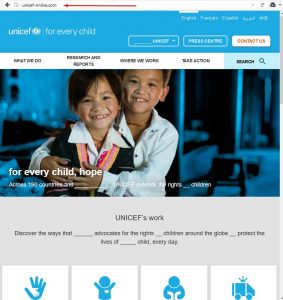
Looking at https://www.icann.org/compliance/complaint we find ICANN would either consider such issues content issues Spam, Phishing & Website Content, or IP Infringement & Cybersquatting. In the case of IP Infringement the best case scenario from an ICANN responsibility perspective would be to lodge a UDRP complaint. But that option is reserved for right holders only, the United Nations in such a case. If it were not the United Nations, it would cost the rightful brand owners a minimum of $2,500 to defend their rights. But in this case, certain names are protected internationally. This opens up a not so small can of worms for ICANN.
But what about the causal consumer that may be targeted with this issue? We find a typical tunnel vision replies from ICANN at https://www.icann.org/en/resources/compliance/complaints/web where 419-fraud is not even acknowledged, despite being a massive growing threat to business and consumers. In all cases the reply is generally the same:
Complaints about website content are outside of ICANN‘s scope and authority; for these types of complaints, please refer to one of the options listed below:
- You may want to contact a law enforcement agency in your jurisdiction
- You may want to file a complaint with a consumer protection entity such as the International Consumer Protection and Enforcement Network or the US Federal Trade Commission
- You may want to contact the website’s Internet Service Provider
- You may want to contact the registrar of the website’s domain name
It’s common cause that victims to cyber crime are turned away at many law enforcement offices. Victims are even scolded, demeaned and chased away. While some countries have taken a mature approach to this form of fraud, many countries have not and any such protection is virtually non-existent.
ICPEN, while a great initiative and most definietely not to distract from what they are doing, is not as international as is required to be an abuse operator for ICANN. We find a list of member countries here: https://www.icpen.org/who-we-are – but what about the countries not mentioned? Think of countries like India? Ukraine? South Africa? Russia? Malaysia? The FTC in turn is is great for citizens of the USA, but there it stops.
Up to this point, it’s clear ICANN is trying to make everybody except themselves an abuse operator for what they are supposed to be managing, domains. So that leave the consumer with the last option:
- You may want to contact the registrar of the website’s domain name
However, before looking at this option, we need to remember that the consumer has no official voice at the registrar where such a registrar’s domains is used to the detriment of the consumer. The contract between ICANN and the registrar, the ICANN RAA, transfers no third party rights. This makes many internet consumer a slave to the goodwill, or abuse, of a registrar sponsoring malicious domains.
However, as was recently said to ALAC at one ICANN meeting:

By disassociating domain names from any abusive usage, ICANN is violating consumers trust while simultaneously setting up their registrants for unaccountable $2500 UDRP bills.
The problem #2 – Registrars
Many registrars are great at looking at abuse issues given clear evidence; The Endurance Group, Tucows, GoDaddy, Internet.bs etc. These registrars do not wish to see their services abused to the detriment of the consumer and will suspend such malicious domains. They have no desire to accept stolen money, the consumer’s money, from fraudsters who’d wish to purchase their products. These are the silent heroes the causal internet user may not even be aware of.
Yet the efforts of these registrars are being undermined, to the financial detriment and market share of the heroes. To understand this statement, we need to consider that most registrants are not abusive, register a few legitimate domain. On the other hand, West African fraudsters can be considered extreme domain consumers. It’s not uncommon to see one individual linked to over 300 domains. In one instance such a fraudster registered over a 1,000 domains – and still at it!
Namecheap
Namecheap is a long time sponsor of malicious domains. Their response in abuse issues has been documented before on this blog. However, we will soon be seeing how Namecheap has been central to one issue the BBB will be publishing on. Not only has Namecheap been allowing generic top level domains to be abused, but also .US domains at the hand of West African scammers, to the extreme detriment of US consumers. All we will say at this stage is “Watch this space”.
There can be no argument that Namecheap is a consumer threat enabler, wittingly or simply due to carelessness.
Reg.ru
But let’s consider flyasianxpressdip.com registered via Reg.Ru and abused by West African fraudsters to defraud consumers in Eastern Europe in West African romance scams. The content used for the website has been stolen from the legitimate http://www.aerofrt.com/ and the company name changed, matching the domain name. This domain was registered using the registrars privacy protection service.

Domain name: FLYASIANXPRESSDIP.COM
Domain idn name: FLYASIANXPRESSDIP.COM
Status: clientTransferProhibited http://www.icann.org/epp#clientTransferProhibited
Registry Domain ID:
Registrar WHOIS Server: whois.reg.com
Registrar URL: https://www.reg.com/
Registrar URL: https://www.reg.ru/
Registrar URL: https://www.reg.ua/
Updated Date: 2016-10-19
Creation Date: 2016-10-19T20:06:57Z
…
Registrant Name: Protection of Private Person
Registrant Street: PO box 87, REG.RU Protection Service
Registrant City: Moscow
Registrant State/Province:
Registrant Postal Code: 123007
Registrant Country: RU
Registrant Phone: +7.4955801111
Registrant Phone Ext:
Registrant Fax: +7.4955801111
Registrant Fax Ext:
Registrant Email: FLYASIANXPRESSDIP.COM@regprivate.ru
This domain is being abused for the infamous gift scam, where the new partner sends a fictitious gift, but then customs find issues with this parcel and the victim has to pay fees and fines. A scam. But we have other serious issues here. Scammers do not care about consumer’s privacy, only stealing money from the victims via deception. This domain is massively leaking out victim consumer privacy.
Registrar Reg.ru was made aware of all the pertinent information. Reply?
Subject: Re: [Ticket#2017052110023261] Fraud Alert: flyasianxpressdip.com [77.222.62.59]
Date: Mon, 22 May 2017 10:50:55 +0300
From: Отдел рассмотрения жалоб <abuse@reg.ru>Dear Sir/Madam,
REG.RU company has no right to apply sanctions to the domain name on the basis of third parties claims. Domain registrant independently carries out domain management and is solely responsible for the content posted on its resource and all the activities associated with the domain name.
We can take measures to domain registrant only on the basis of an enforceable judicial decision or in case of violation of the Rules of registration by the registrant.Please refer to the article: https://www.reg.com/support/abuse/#expanders=c0
it lists all of our recommendations for solving this issue.REG.RU Company do not provide any services for domain. Please, apply to current service provider.
The irony here is that there are certain obligations a registrar or proxy provider has to provide proxy services. These cannot be found on the English or Russian websites at https://www.reg.com or https://www.reg.eu. As such we launched a compliance complaint to ICANN. ICANN’s response?
Please note, the registrar demonstrated that all posting requirements of the Specification on Privacy and Proxy Registrations of the 2013 Registrar Accreditation Agreement (RAA) are displayed on the registrar’s website, https://www.reg.ru/
Despite asking numerous people to check, no proxy provisions as per the ICANN RAA SPECIFICATION ON PRIVACY AND PROXY REGISTRATIONS can be found.
It get’s better, USMILITARYCOMMAND.COM – the supposed United States Army (Leave Department for the U.S. Army), linked to a well known West African serial domain abuser, is registered on Reg.ru. Once again the domain name matches the content.

So how does Reg.ru’s relief provided scale?
Where to apply (international domain zones .com/ .net/ .org/ .info etc.)?
APWG Anti Phishing Working Group
APWG is the coalition unifying the global response to cybercrime across industry, government and lawenforcement sectors. ICANN is a member of this organization and refers to it if necessary to file a complaint about phishing.
contacts: http://www.apwg.org/contactus/
website: http://www.antiphishing.org/ICPEN International Consumer Protection and Enforcement Network
ICPEN organization within the consumer protection agencies from more than 50 countries, the aim of which is to promote global cooperation among law enforcement agencies.
website: https://www.econsumer.gov
Artists Against 419 is a member of the APWG. The APWG was not set up to address 419 fraud. We already looked at relief via ICPEN and the shortcomings of this approach. So it’s clear we have no real relief for 419-fraud issues as per the option provided. But on the off-chance of those 419-spam issues might giving us a clue on how to resolve this:
SPAMHAUS
The area of competence of the organization includes counteraction to the use domain names for the purpose of phishing, unauthorized access to information systems of third parties, malware distribution and management of malware (botnets).
website: http://www.spamhaus.org
APWG Anti Phishing Working Group
APWG is the coalition unifying the global response to cybercrime across industry, government and lawenforcement sectors. ICANN is a member of this organization and refers to it if necessary to file a complaint about phishing.
website: http://www.antiphishing.org/
Spamhaus, despite doing a marvelous job doing what they’re doing, has no reporting mechanisms for the consumer.
Conclusion: Reg.ru is trying to making everybody else responsible for abuse of their services while offering no real workable solution. This becomes important where we see them as a domain supplier in the West African fraud chain.
Namesilo
Namesilo has also become one of the got-to places for West African fraudsters to register their domain names. Many are using Namesilo’s associated PrivacyGuardian.org proxy. In a recent analysis, it also clear that approximately 80% of these malicious domains are channeled via reseller QHoster.
How does Namesilo view their role in fighting abuse – or should that be not fighting abuse? Judge for yourself: https://www.namesilo.com/Support/Abuse-Reporting-Procedures:
Please note that we are not a shortcut around due process. We are not an arbiter of trademark, copyright, intellectual property, etc. disputes. There are established processes in place for dealing with many common disputes, but we are not to be used as a shortcut around those processes. We are also not a law enforcement investigative body. We are a domain registrar. We do not believe it is the role of domain registrars to determine what is legal and what is not. This is the purview of the legal process within the locales in which alleged offenses occur. Please do not contact us with the goal of circumventing the legal process. Remember that we are a domain registrar and not a government agency, a police force or a judge of legal matters. Please do not ask us to determine if content on a web site is legal or not. In the vast majority of such cases, that determination is not objective and there are nearly always areas of disagreement between parties. As a domain registrar, we are not to be used to render decisions on these matters unless directed to do so via a court or similar agency of adequate jurisdiction, or indisputable evidence that a violation of our terms has occurred.
We find banks, drug scams, fake couriers and similar malicious domains flourishing under Namesilo’s protection. It’s no surprise that we find this registrar also being named in reports from other parties fighting other forms of abuse. Yesterday again, Artists Against 419 had to intervene again to mitigate on a Royal Bank of Canada spoof, abusing domain irbcon.com:
Domain Name: irbcon.com
Registry Domain ID: 2100855297_DOMAIN_COM-VRSN
Registrar WHOIS Server: whois.namesilo.com
Registrar URL: https://www.namesilo.com/
Updated Date: 2017-07-20
Creation Date: 2017-02-27
….
Registrant Name: Domain Administrator
Registrant Organization: See PrivacyGuardian.org
Registrant Street: 1928 E. Highland Ave. Ste F104 PMB# 255
Registrant City: Phoenix
Registrant State/Province: AZ
Registrant Postal Code: 85016
Registrant Country: US
Registrant Phone: +1.3478717726
Registrant Phone Ext:
Registrant Fax:
Registrant Fax Ext:
Registrant Email: pw-0fb58888829407528992990403142be5@privacyguardian.org
Looking at this domain, we note PrivacyGuardian.org being used to hide the fraudster’s identity. As per the associated website at https://www.privacyguardian.org/:
If a domain utilizing our service has engaged in SPAM or some other illegal activity, please provide evidence of such behavior below. If you have a copyright/trademark dispute, you should direct your complaint to the respective web site host for the domain. We are solely a privacy service, and, as such we have no control over the storage or distribution of any allegedly infringing materials.
What a great game to play, but only the start of the games. You can report anything, they deny anything illegal, but will not judge on it – including the RBC spoof that was reported via their form at the above URL on 20 June 2017.
But the plausible deniability game does not end here. The game works like this.
- Domains are registered via resellers such as QHoster. Many have fake details. Reporting this QHoster results in a request to report it to Namesilo (despite ICANN RAA requirements supposedly enforced onto the channel as a whole).
- Namesilo in turn insists their abuse form is used. This form does not send any acknowledgement, leaving the reporter with no way of proving this form was used.
- Should any future issues/consequences arise due to Namesilo’s inactivity (some touching on ICANN mandated policy and obligations), they simply deny having received such a submission with no way to prove otherwise.
- It appears the PrivacyGuardian form operates in a similar fashion as no acknowledgements are received either.
Ironically in the malicious domains registered via this channel, most have accurate registration details, the telephone numbers are working, the names seems like real people. But upon closer inspection, the name does not belong to the address, nor does the phone number match. The registration detail are totally bogus. This pattern is seen in one syndicate operating under Namesilo.
In another fraud issue with domains sponsored by Namesilo, we see shockingly invalid registration details and hoster mitigation offering no consumer relief. This issue was reported to ICANN compliance in a complaint last year. ICANN in turn diverted this into a domain registration issue closing the relevant ticket. This fraud continues – massively.
Currently law enforcement is once again trying to pick up the pieces left behind in one such instance where we see people from the Middle East being grossly defrauded in Namesilo sponsored domains.
Ourdomains
Registrar Ourdomains in Hong Kong is a newer registrar and already seeing gross domain abuse used in West African fraud and especially a specific type of fraud; pet scams from the Cameroon. Along with Namecheap, this registrar is responsible for most of the obvoius pet scam domains targeting the USA and areas where pets are sought. Up until the end of last year, they were also offering domain proxy protection. They later denied this after an ICANN complaint, which ICANN accepted without checking further and closing the compliance ticket. West African fraudsters using KodDos/SwiftSlots/BeamServers as hosters, use this registrar regularly.
However, there are encouraging signs coming from this domain sponsor. They have been seen to be putting domains on hold. One scammer massively using them would be elibulldogs@gmail.com. But while some of this parties domains are being suspended, others are left intact. As such this registrar’s reaction is rather confusing. We can only hope.
Reality Check
West African fraudsters have refined their fraud to the levels unprecedented before. The days of the Nigerian Prince wishing to deal out millions is long gone. It’s been replaced by romance scams, investment fraud, commodity scams, extortion etc. Once the domain name is known to the anti-abuse community, it’s not uncommon to find these domains recycled and re-purposed and used for phishing and BEC where no hosted content is visible.
West African based fraud includes domain use where such use has no other purpose than fraud. West African fraud would not be as successful as it is were it not for a readily available supply of cheap domains at registrars not enforcing their stated policies, or willing to hold themselves blameless while profiting from such domain abuse.
With ICANN denying this reality and responsibility, ICANN and certain registrars are facilitating fraud, massively depriving innocent consumers of their livelihoods, if not lives indirectly.
References: Malicious domains