The GDPR and blanket privacy: Hold on – who watches the guardians ICANN?
ICANN had two complaints they closed, escalated back to them last week. One was a Registrar Standards complaint, one was regarding a rogue reseller proxy at the registrar which is the subject of the first complaint. Why?
What happens where we have a registrar that serially accepts and has been accepting weak unverified registration details, for at least the past four years into the registries, in violation of the ICANN RAA and this leads to mass abuse?
What happens if this is pointed out to ICANN via existing mechanisms, then it’s made out by the registrar as content issues and blindly accepted by ICANN as such, despite the last* Registrar Standards complaint being an analysis of WHOIS details showing unverifiable non-existent telephone numbers, registrant details being nothing more than non existent made up registration details stuffing? Example: “Bar Clay” (for a Barclays spoof) and then used again and again? Ditto “Inno Cent”? Sure, when hell freezes over. Even if it convinces the registrar and ICANN, it doesn’t convince us. Why? This malicious actor is making a mockery of the domain registry system, yet ICANN accepted the registrar’s response that these are mere content issues.
/Update 2018/09/11: These Complaints can now be found on ICANN’s website at https://www.icann.org/complaints-report as Complaint Numbers 00006097 and 00006198.
It’s for this reason Artists Against 419 escalated the handling of it’s latest two complaint’s and closure within ICANN back to them, also making the ICANN President Mr Marby aware of this most serious issue.
* Last: This was the second complaint about the same issue and the same registrar in as many years. This violation was previously devolved to a mere WHOIS issue about a single domain, then resolved and closed by ICANN with the domain they devolved it to, still resolving with clearly fake registration details and spoofing the Reserve Bank of India. This was after a similar closure of a report regarding another Registrar with similar attitude, that saw the complaint devolved to an issue about an American bank spoof with fake registration details, that eventually became an escalation to the ICANN Ombudsman, to be never heard of again.
Who are the guardians of the RAA Whois Accuracy Program Specification and upholds Registrar Standards if ICANN does not accept this role for GTLDs where they oversee policy development and standards? It makes any such policies moot and nothing more than window dressing if such policy is not enforced.
What happens when we end up with abused proxies when the above mentioned registrar’s main reseller responsible for greater than 60% of domains targeting consumer in fraud, is running a proxy not in line with the RAA Specification on Privacy and Proxy Registrations? On said proxy we see banks and commerce being spoofed, phishing attacks, all carefully hiding the perpetrators? A proxy with no polices and a perfect shield to ensure accountability. In some cases we even end up with proxies behind proxies, where the downstream proxy and reseller registers domains for their clients based upon usage (the author had an interesting chat with the downstream proxy/reseller who thought he was one of the regulars. This reseller does jurisdiction/Registrar shopping. Registrars in Russia, China and the USA are fair and willing game).
ICANN’s view on closing the complaint was :
Upon request by ICANN, the registrar took corrective actions and is now in compliance with the relevant provisions of the Specification on Privacy and Proxy Registrations of the 2013 Registrar Accreditation Agreement (RAA).
Which was later changed to:
To clarify this matter, the registrar of record confirmed with ICANN that the domain names referenced in your complaint (domain names redacted), and those registered with similar information, are registered to a third party or reseller and not a proxy service. Under the 2013 Registrar Accreditation Agreement (RAA), resellers may be registrants for domain names.
This was the reply, despite said reseller have their own complete domain registration panel etc, separate from sponsoring Registrars system (we are unsure what back-end integration there may be), also the RAA saying under the proxy provisions:
1.4 “P/P Provider” or “Service Provider” is the provider of Privacy/Proxy Services, including Registrar and its Affiliates, as applicable.
2 Obligations of Registrar. For any Proxy Service or Privacy Service offered by the Registrar or its Affiliates, including any of Registrar’s or its Affiliates’ P/P services distributed through Resellers, and used in connection with Registered Names Sponsored by the Registrar, the Registrar and its Affiliates must require all P/P Providers to follow the requirements described in this Specification and to abide by the terms and procedures published pursuant to this Specification.
What is an affiliate?
Electronic commerce: Firm which sells other merchants’ products at its own website. Visitors to the firm’s website may order merchandise from there, but the sale is transacted actually at the principal’s site who passes on a commission to the website from where the order originated.
From: http://www.businessdictionary.com/definition/affiliate.html
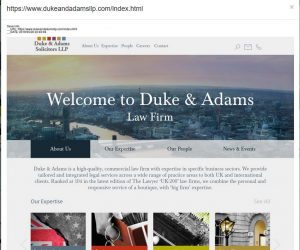
… unless we are to believe the reply to ICANN and it’s the reseller spoofing banks like The Bank of England, Cater Allen Private Bank, stealing content from lawyers like Edwin Coe LLP to create a fake lawyer (see below), or even spoofing NATO procurement (where we have an email with headers)? Which, if it were true, surely said reseller has no place in the domain channel and it could be suggested some time rather sepentin jail, not excused and silently absolved as affiliates of the accredited registrar? We see massive gaming of the DNS system at everybody else’s expense:
We are now seeing some strange language other than common logical English emanating as an excuse. The sponsoring Registrar was aware of this proxy as was demonstrated. There is a logical departure from reality here in ICANN’s reply regarding this proxy. It is for this reason this response was also escalated within ICANN along with the first.
Taking this a step further: what acknowledgement is there for a polluted reseller channel where the hoster and domain reseller via an affiliate program is the very one receiving abuse reports? There is plenty evidence of this.
To briefly illustrate the problem, we will oust a facilitator, VBHostNet. Naturally all evidence has been captured. If you can’t say it; “shush”. If you have evidence, you can shout it out. Domains below were mitigated rapidly at the respective registrars and are for illustration purposes. Initially the reseller/hoster was playing abuse games on AceNet, disabling spoofs and scams upon abuse report receipt, then to sneak them back hiding content:
Email address provider @rhyta.com is an open to anybody, disposable email address at FakemailGenerator , also serving email addresses ending in @armyspy.com, @cuvox.de, @dayrep.com, @einrot.com, @fleckens.hu, @gustr.com, @jourrapide.com, @superrito.com and @teleworm.us.
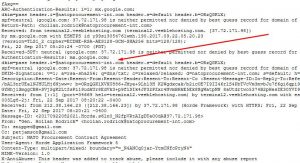
Ref: http://www.fakemailgenerator.com/Looking at the email address carlmarvin64@gmail.com used for registering the Danske Bank spoof, we find another identity with another address using the same email address:
We see the registrant name, address and telephone number changing for email carlmarvin64@gmail.com
(We show domains to illustrate a scam nest):
vbh.csv
VBHostNet Facilitated Advance Fee Fraud
Domain dbURL Site Name stancharteredb.com https://db.aa419.org/fakebanksview.php?key=128571 Standard Chartered onlinefinansb.com https://db.aa419.org/fakebanksview.php?key=104911 Finansbank nat-oilcompany.com https://db.aa419.org/fakebanksview.php?key=124902 National Oil baylinelaw.com https://db.aa419.org/fakebanksview.php?key=124901 Bayline Solicitors mynetcash.com https://db.aa419.org/fakebanksview.php?key=124897 MyNetCash shullyblogistics.com https://db.aa419.org/fakebanksview.php?key=124896 Shully B Logistics teaboconline.com https://db.aa419.org/fakebanksview.php?key=124892 The East Asia Bank of China esquirebonline.com https://db.aa419.org/fakebanksview.php?key=124887 Esquire Bank cargofr-china.com https://db.aa419.org/fakebanksview.php?key=124883 Cargo From China globalwiledsafe.com https://db.aa419.org/fakebanksview.php?key=124882 Globalwiled Safe Security & Shipping Company devonenergy-corporations.com https://db.aa419.org/fakebanksview.php?key=124880 Devon Energy integrityfinanceloans.com https://db.aa419.org/fakebanksview.php?key=124678 Integrity Finance and Loan dcecourierservices.org https://db.aa419.org/fakebanksview.php?key=123003 Direct Courier Express wheatlandb.com https://db.aa419.org/fakebanksview.php?key=122919 Wheatland Bank jpcorpllc.com https://db.aa419.org/fakebanksview.php?key=122918 JP Construction LLC cts-freight.com https://db.aa419.org/fakebanksview.php?key=122902 China TS Freight creditsmutuel.com https://db.aa419.org/fakebanksview.php?key=120531 Credit Mutuel chelsharbour.com https://db.aa419.org/fakebanksview.php?key=120530 The Chelsea Harbour Hotel unihospae.com https://db.aa419.org/fakebanksview.php?key=118877 Universal Hospitals saugerhosp.com https://db.aa419.org/fakebanksview.php?key=118876 Saudi German Hospitals Group saugerhos.com https://db.aa419.org/fakebanksview.php?key=118306 Saudi German Hospital Dubai capfcu.com https://db.aa419.org/fakebanksview.php?key=106135 Capitol Federal Credit Union vtbconline.com https://db.aa419.org/fakebanksview.php?key=128670 VTB Group intlmonetaryfund.com https://db.aa419.org/fakebanksview.php?key=125811 International Monetary Fund speed-cs.com https://db.aa419.org/fakebanksview.php?key=125533 Speed Couriers Service unicef-online.com https://db.aa419.org/fakebanksview.php?key=125507 The United Nations Children's Fund candidhelp.com https://db.aa419.org/fakebanksview.php?key=125506 Candid Help fadeeslogistics.com https://db.aa419.org/fakebanksview.php?key=125505 Fadees Logistics tuksbonline.com https://db.aa419.org/fakebanksview.php?key=125504 TurkishBank tuksb.com https://db.aa419.org/fakebanksview.php?key=125503 TurkishBank landforexfx.com https://db.aa419.org/fakebanksview.php?key=125502 Land Prime Ltd / LandFX Ltd jetteust.site https://db.aa419.org/fakebanksview.php?key=125499 http://jetteust.site danskebonline.com https://db.aa419.org/fakebanksview.php?key=125476 Danske Bank turkpb.com https://db.aa419.org/fakebanksview.php?key=125469 TurkishBank turkbkonline.com https://db.aa419.org/fakebanksview.php?key=125468 TurkishBank santatravelsae.com https://db.aa419.org/fakebanksview.php?key=125090 Santa Travels & Tours LLC capunityonline.com https://db.aa419.org/fakebanksview.php?key=124908 Capital Unity Bank mercurypays.com https://db.aa419.org/fakebanksview.php?key=124907 MercuryPays qphunds.com https://db.aa419.org/fakebanksview.php?key=124906 qPhunds elite-courieronline.com https://db.aa419.org/fakebanksview.php?key=124905 Elite Logistics elite-logisticsonline.com https://db.aa419.org/fakebanksview.php?key=124904 Elite Logistics
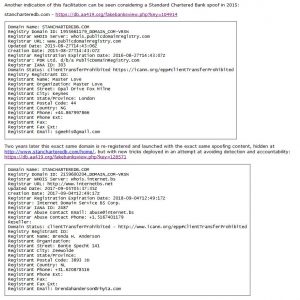
This is big business in certain parts of the world where the very party designing fraudulent websites, registering domains for criminal enterprise and publishing them for criminal syndicates, is also the party that has reseller privileges, apart from hosting reseller accounts etc. Sometimes this party operates purely email only domains portfolios. This type of pollution is well hidden and an insider threat to the ICANN system, but regularly encountered upon closer inspection. The one report ICANN has in their possession shows something similar, but a magnitude of size greater, also previously reported in a compliant. This has led to two years of profuse consumer harm while undermining the legal rights of banks, lawyers, governments etc.
What acknowledgement is there for the dangerous nature of consumer harm that can be done with domains? What about the consumer rights? That consumer may be a bank or an ordinary man/woman/even child in some remote jurisdiction where law enforcement is not that mature? It may be a government. If we go onto the net, we are consumers of the DNS system. Each and every user clicking on a link on the the web, or email, or even typing a website name into an address bar, is consuming DNS to resolve that website to an IP address. It’s that DNS that’s being poisoned with malicious entries. The consumer is not only a privileged group called registrants, a special club, as has been implied before at some ICANN events. Even if it were, the legal rights of “club registrant” is being undermined by malicious actors in the DNS system.
The GDPR was meant to protect the privacy of natural persons. What acknowledgement is there in spirit for the GDPR if “anything goes” into the registry via certain registrars who feel themselves absolved to not to uphold the RAA or any form of consumer protection? How much of this mess is currently being hidden by proxies and of late, the GDPR? Speaking wider than the above mentioned registrar, certain disposable email addresses have online pages actually publishing such email communications. We see credit card fraud charge-backs, spam complaints, phishing complaints and even CP feedback from certain registrars on these disposable emails as reasons for termination and suspension. Where is the consumer protection? Yet many of these domains survive if these small obstacles are bypassed. Disposable (fake) registration details and disposable emails go hand in hand with abuse. There is very little acknowledgement for the rights of ordinary consumers except to consider them a third party with no rights in any of these agreements. The registrar holds the registrant liable for any issues and the RAA and Registrar/Registrant agreement requires the registrant will not use the domain to directly or indirectly infringe third party rights. What if the malicious actor uses that domain to point to fraudulent content, perhaps even stolen content, as to defraud? Perhaps even causally spoofing? Or perhaps uses the domain to spoof in email only attacks, for example to impersonate the FBI etc?
3.7.7.9 The Registered Name Holder shall represent that, to the best of the Registered Name Holder’s knowledge and belief, neither the registration of the Registered Name nor the manner in which it is directly or indirectly used infringes the legal rights of any third party.
3.7.7.12 The Registered Name Holder shall indemnify and hold harmless the Registry Operator and its directors, officers, employees, and agents from and against any and all claims, damages, liabilities, costs, and expenses (including reasonable legal fees and expenses) arising out of or related to the Registered Name Holder’s domain name registration.
But what happens to 3.7.7.12 if that registrant is a bogus entity and the registrar knows it? Can the registrar still be held harmless on the basis of the RAA? Indeed, what about ICANN, if they know about such an issue and and do nothing about it?
What if the registrar or it’s affiliate provides proxy protection to a malicious client instead?
3.7.7.3 Any Registered Name Holder that intends to license use of a domain name to a third party is nonetheless the Registered Name Holder of record and is responsible for providing its own full contact information and for providing and updating accurate technical and administrative contact information adequate to facilitate timely resolution of any problems that arise in connection with the Registered Name. A Registered Name Holder licensing use of a Registered Name according to this provision shall accept liability for harm caused by wrongful use of the Registered Name, unless it discloses the current contact information provided by the licensee and the identity of the licensee within seven (7) days to a party providing the Registered Name Holder reasonable evidence of actionable harm.
Ironically this is being massively gamed. To date no registrar or the affiliate proxy provider has been held accountable, yet some operate proxies with reckless abandon, ignoring these provisions. Will that change when we illustrate a pattern of deliberate self blinding? At one registrar providing blanket protection, we get some insight into what qualifies as acceptable, much hidden behind proxies (although via indirect methods).
We do have a small acknowledgement for commercial rights in the RAA in terms of UDRP mechanisms (or URS – depending on the TLD). But if we see a bank like Société Générale lodge UDRP proceedings for a second time to protect their rights, and the same respondent that does not reply use the same weak unverified details to register a third spoof even while the second UDRP is taking place, does the $10 domain the malicious actor pays not trump the rights of the ~$2500 the bank pays, turning the party using ICANN’s own UDRP sanctioned system into a victim at the hands of non-caring reckless registrars? Where does the responsibility lay for this abuse – merely the registrant? Or can the registrar be held accountable? Indeed, what about ICANN, once they are aware of this and do not remedy the situation?
How will the ordinary consumer in country XYZ defend their rights if their authorities does not wish to engage? This is extremely topical: The UK has been more transparent than most countries in this regard. Only 1% of reports leads to an arrest. About 10% gets investigated. Official stats says only 10% of victims report (this figure is being revised, it’s way too high). So less than 0.1% of cyber crime victims ever get restitution of see justice. What happens to the other people, the other victims, and their rights? They are doomed to become statistics simply because a malicious actor payed a “I can’t care a hoot” Registrar using ICANN accreditation as marketing material for $10? Do the victims have rights? Human rights? Privacy is one right – but in a poisoned DNS system where not much can really be verified, risk increases. Business identity theft is rife: just because a website gives details of itself does not mean those details belongs to it. This is not something the Berlin Group anticipated. Even the authorities are being spoofed with impunity. How do you stop a consumer entering his details on a spoof domain or like, to end up on a sucker list forever more, unless he totally stops using the net and anything electronic? Even then it may not be enough. Once the damage is done, it’s extremely difficult undoing such damage – much like trying to un-spill water.
How do you stop a domain being used for abuse where there is no content and a proxy protection? This is as one senior IT security staff member in the EU found out recently after being defrauded with a Standard Chartered Bank spoof, loosing his livelihood. This was just after a certain large registrar blanked their registry details even before the GDPR mandated it, blindly applying blocks on large tracts of IP addresses, protecting club registrant at the cost of the rest of the world with no checks and balances in place. We also were subject to a block and were told via ICANN that Artists Against 419 was harvesting registrant details (hogwash – we never did), but it was blindly accepted. It seems this was a common excuse at the time. Apparently even ICANN abused the system as it was blocked at a stage. This was looked at by an ICANN SSAC member. This largest registrar was invited to do an audit on our systems. Yet it was easier casting aspersions on one of the most anti-abusive, altruistic and non-commercial causes which we uphold, protecting consumers. Artists Against 419 was one of those that saw retaliation, unbeknownst to Mr Brian Winterfeldt, but which he predicted. The ICANN RAA was flouted and we ended up with the tail wagging the dog. Does commercial interest trump consumer rights? Every bad decision on the net has victims, many ordinary consumers.
Certain registrars tend to make law enforcement and/or EC3 their garbage disposal abuse agents after abuse takes place with domains they sponsor. Or insist on a court order. Or insist the complainant has no rights to complain about a spoof. Yet the very consumer is the target when it comes to predatory domain abusers. Many a time spoofing is a crime of convenience in fraud. Ditto stealing content. Law enforcement are overwhelmed and simply cannot do all the mitigation, that is why they ask consumers to report fraud. They try and address the worst of the worst. But geographical boundaries dictate where a party may report it. We wish anybody in most of the Far East, South America or Africa trying to report serial fraud to their local authorities if they are not a victim. They have much less chance if that fraud is targeting the European Union. Europe only accept reports from their own citizens or law enforcement via certain channels. Suddenly we find a disjuncture between registrar theory of operation and reality. Is this deliberate? A simple reality check – and Google/Bing/Yandex/… search shows online fraud is at an all time high. Even from China we find this interesting article: http://www.xinhuanet.com/english/2018-08/04/c_137368096.htm
Technology giant Tencent Holdings detected 96.8 million malicious websites, tagged 29.7 million phone numbers used for fraud, and blocked 18.3 million fraudulent messages in the first six months of 2018, according to the report jointly released by Tencent Research Center and the Data Center of China Internet.
The most common fraudulent messages included those on illegal loans, virus software, malicious websites, fake job positions offering high salaries, and online shopping.
While the breakdown of the numbers will cause a few smiles or giggles in certain jurisdictions, the bottom line is Tencent says there are 56.9% pornographic websites and 34.4% gambling websites in those 96.8 million malicious websites. That leaves 8.7% malicious websites, assuming the gambling websites are real (Tencent points out the upsurge in these with the 2018 FIFA world cup in Russia and we know from history many would be fraudulent and on bespoke domains). 8.7% x 96.8 million is approximately 842,000 malicious websites. Even if we discount political websites and like, as they are most probably included, we also need to accept they probably also overlooked unrecognized threats, so we still have an astronomical number of malicious websites living right next to you and me on the net. Many of these will be using domains registered with fake registration details and each of us are the target. The simple reality is nobody really knows the extent of the global malicious domain problem. Only of late have commercial sector cyber security actors started looking at traditional 419-type fraud. They recognized the “contractor“, a party well described in Artists Against 419 training materials as far back as 2007 as the “faker maker“. The world has moved on. Even now that picture has changed and malicious domain provisioning is taking root in a new way for advance fee fraud syndicates. The parties selling SEO, retweets and followers on Twitter, Facebook etc are now also selling domains, hosting and content to the cybercrime syndicates.
But that aside, is law enforcement consumer protection? No, it’s mitigation of damage after the fact, when the consumer already became a statistic and the harm is already done.
So how does the ICANN environment measure up to consumer privacy protection the GDPR is meant to create while citing human rights? Is ICANN and all registrars really living up to the spirit of the GDPR, or is it simply an opportunity to sweep a big can of worms under the rug, undermining the GDPR, creating a situation where the GDPR becomes a tool to undermine not only privacy but also other human rights? We need to remember that, regardless of which version of human rights you subscribe to, there is a balance between rights and one party’s rights (or abuse thereof) should not be condoned if it undermines the rights of others. Balance of rights is key.
Are the bottoms up processes commonly held out to be followed merely a placebo, while registrars are free to sponsor criminality on the net using domains with fake registration details or proxy protection for $10 a shot as many times as they can do it, simply because they are “not an arbiter of the legality of content hosted on web sites”? Any sane, mature person will know heroin, cocaine etc drugs are illegal in the USA. Or at least you should if you are a business in the USA. Apparently that excludes certain registrars. Did the abuse process not start before the content is active online, spoofing the United Nations/Reserve Bank of India or pretending to be Joe Blogg Drugs targeting consumers internationally? Did the abuse not start during the domain registration process when the registrant deliberately supplied inaccurate registration details? This was most certainly recognized in 2003 in an ICANN advisory. But it seems the system has now dumbed down 15 years later – or is it self blinding for the sake of profit?
Does the GDPR not place an expectation on ICANN and registrars to verify registration details? Does the GDPR not even go as far as allowing the sharing of data for anti-fraud purposes? Is there not an expectation within the GDPR which is overlooked and not taking place in ICANN circles, to take due care and try and keep fraud out of the system? Surely by the 10th time a registrant crops up spoofing “A B C” with a new domain and every changing details, or using a domain to defraud consumers, private people or commercial, we have a pattern? Likewise if a party serially registers fictitious drug selling domains fro later websites?
If somebody with serial abuse history claims to be selling Nembutal in the USA, surely there should be a red flag?
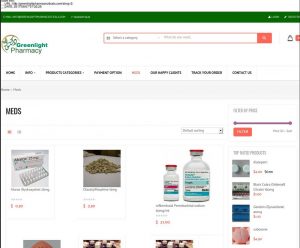
This is in reference to a particularly nasty type of fraud leading to extortion which the DEA and FDA warns about. We even have a spoof of the DEA recorded in our database showing the victims being extorted! This type of fraud specifically targets cancer sufferers and like, first with other fake medication offers while also stealing their credit card details. When the victims give up all hope, the Nembutal drug scam targets them again (remember – sucker lists). Let’s look at Greenlight Pharmacy:
Ironically this domain was put onto hold, but is now resolving again. How innocent! A redeemed fraudster now offering health advice? Did said registrar now not use content issues to decide on DNS abuse?
Meanwhile elsewhere in the real world, the domain’s email is being used to sell cocaine, LSD, opium … so is this a content issue? Or an excuse?
Remember, while this party has access to the domain’s DNS, he can set the SPF/DKIM to whatever he likes. We now have a dangerous domain able to send verified email from anywhere and receive it whereever the fraudster desires. Our fraudster has now undermined SPF and DKIM mechanisms. Does it help that we say that, despite this party’s proxy protection, we know full well who he is? Hello “Apteka HealthCare”. Does it help to say that this registrar welcome this fraudster with open arms, even offering him sanctuary and defending him when honorable Registrar Joker booted him for similar drug scams and abuse of their proxy services? Does it help saying he is also a John Doe party in the Delta Airways vs John Does case: http://www.spokesman.com/stories/2017/oct/29/delta-probe-uncovers-criminal-scheme-to-scam-pet-o/? The close link between pervasive pet scams and drugs scams are well established. Who would have ever expected the Asian Arowana sales were extortion – they are CITES protected species. Our fictitious DEA/FDA agents are also fictitious US Fish and Wildlife officials out to get the gullible who believed the fraudster advertising on the net and buying from him, with fake promises of permits for non-existent Arowana, then using non-existent couriers (leaking privacy like a sieve) to complete the consumer trap as “These fish may not be imported for commercial or personal pet purposes.” Pay up!
Likewise fedrbnyc.com which is spoofing the New York Federal Bank and had content hidden at http://fedrbnyc.com/online/ and the domain was suspended. The content was removed and the domain un-suspended. Once again we see what the registrar claims vs what they do, does not tally. Was the content removed, or merely moved? Well, the New York Fed is now being spoofed from http://us.fedrbnyc.com/ – is that us. a clue to DNS abuse or not? While a simple example, there is a myriad number of ways that a malicious registrant can mitigate host based take downs. The Bank of America incidentally mitigated a spoof of themselves at hosting level ala anti-phishing style for a domain registered at this registrar. Result? The domain was promptly transferred to a professional email hosting provider. The content was gone, the fraud continued. The domain was not phishing, it was being used for advance fee fraud (419-fraud). Email abuse in the DNS system is pervasive, why not in advance fee fraud? Is this so difficult to understand or unexpected?
At another registrar we saw a fake lawyer website, with content stolen from the real lawyer, mitigated and jumping between hosting providers no less than 27 times before the registrar finally intervened and placed the domain on hold. As any realistic hosting provider will tell anybody caring to listen, mitigating at hosting level while the malicious registrant still has access to the domain’s DNS is an exercise in futility. And what if the hoster is one of those protected sanctuaries for criminality, incidentally also the downstream domain reseller?
Back to the registrar of the topic: Ironically one of the issues mentioned in the report was said registrar not responding to complaints. KnuJon encountered a similar issue and reported on it publicly last year, http://www.circleid.com/posts/20170215_narcotics_traffic_is_not_part_of_a_healthy_domain_system/, describing how:
the site became “hidden” from certain IP addresses. As of today domain is still selling Fentanyl.
We see a report of similar tardiness to address illegality and abuse in a CSIP / LegitScript report in June 2018, The State of Opioid Sales on the Dark Web (comment in bold that of the author for the sake of clarity after redaction):
website amazingpharmaceuticals.com lists opioids for sale, including fentanyl, morphine, and codeine. We were unable to verify whether products are actually
shipped …… but the company (the registrar) has been slow to respond, sometimes taking months to process complaints that often result in no action.
While KnuJon and LegitScript are trying to address an illegal drug sales problem, Artists Against 419 is trying to address an Advance Fee Fraud issue. Apparently both are equally at home at said registrar. Ironically amazingpharmaceuticals.com is in the fraud category, also targeting the desperate with Nembutal and not surprisingly most probably linked to the previously mentioned Greenlight Pharmacy above. Recorded 2017/06/18:
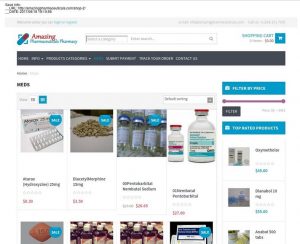
This is what happens when self blinding to obvious issues for the sake of ease and profit occurs, criminals find a foothold from where to launch attacks against the most vulnerable of the vulnerable. What has become of the hope and promise of the Internet?
Advance fee fraud is DNS abuse when the fraudster has a bespoke domain for all the stated reasons and with zero legitimate purpose. Anything further abuse related that follows, is a product of this abuse of the DNS system. While it’s trivially easy abusing a registrar, it becomes unforgivable when a registrar self blinds to the obvious and becomes a knowing facilitator, even if indirectly. Likewise any system that allows it.
Most registrants are honest upstanding people/companies. But then again they will only ever own one or a few domains. A few more brand protection agencies or domain speculators will have vast portfolios. Yet advance fee fraudsters also massively register domains, abusing privacy mechanisms or fake registration details, for one single purpose – to defraud. One party is sitting at far over 1,600 domains. When registrars get wise and boot him, he simply uses another one. Rinse and repeat the domain abuse. Let consider fursythe02@yahoo.co.uk … the privacy purists – please relax, it’s a synthetic identity showing why we need WHOIS access to protect consumers:
https://www.whoxy.com/email/753754
Ouch!!! An old acquaintance in compliance at Tucows; will remember him as Bola Olorunlogbon – yes, he’s still at it abusing the DNS system more than 10 years later! Thanks for the many times you mitigated him!
Aliases fursythe01@gmail.com, matlock.stephen@yahoo.com, stevenjpratt01@yahoo.com, hacking_unlimit3d@yahoo.com, lester.m1010@yahoo.com … the list goes on an on!
Another malicious party targeted ~15,000 victims with just under a 100 domains, leading to loss of victim privacy and defrauding >60% of these victims, many left destitute; mostly single young mothers and even children. Law enforcement never engaged despite outreach via the appropriate channels. He retried abusing said registrar two more times and got booted both times (all honor to the registrar and relevant registry – thanks to friend). He was welcomed at a certain large US registrar offering blanket proxy protection with an extremely bad reputation in IT Security circles. He promptly spoofed numerous legitimate couriers to perpetuate his gift scam again (how did we know how many victims were targeted? read on). Some registrars self-blind to the obvious. The bullet proof registrar has become a reality in the USA.
This article explains the gift scam: https://www.iol.co.za/news/courier-scam-woman-on-the-verge-of-suicide-7750603. While this is not part of the previous scam nest, South Africa is known to be the location of a reseller massively targeting consumers and business in orchestrated fraud, using the registrar at hand. This reseller also targets business in a variation of a procurement scam called a tender scam, spoofing government and having a devastating effect on small business, destroying many. Who would have ever thought the humble courier is probably one of the biggest consumer threats today? There is a reason why DPD Couriers has had to defend their good name with with UDRPs (not cheap). While some registrars who are quick on the draw when they see a bank spoof (ooh, a phish …), many hardly care about fake couriers. These trivially leak private consumer information (yes, that’s how we knew how many target victims there were earlier). Some offer credit card facilities to pay, claiming the card was rejected, using this as a reason to demand a Western Union or other unaccountable payment method. Is it not money laundering this leads to? Regardless of paying or not after this, or smelling a rat, victims have their credit cards abused if they tried using them. Let’s Encrypt certificates are trivially abused to complete the illusion. The courier is probably the most abused scam type. The Eicra Courier Template is probably the most abused and virtually a guaranteed danger sign. The owners of the Eicra template decided not to defend their design and is probably now useless. This does not mean harm did not follow. Many consumers probably silently regret ever seeing it. Despite this continuous abuse, there is little recognition and acknowledgement for the danger of fake couriers.
Mainstream IT security are extremely busy mitigating commercial and governmental threats. There is little recognition for pure consumer facing threats and as such little understanding of the latent threats. It was against this background that BEC evolved from consumer to commercial threat. Even now the puppy scam actors targeting the USA is a massive problem in Far East and lurking in shadows in Europe. The same fictitious couriers used to transport fictitious pets in the USA are being used to transport a few tons of fictitious lobster tail/scrap/paper in the Far East, also Europe of late. Incidentally also the drugs mentioned above. Since a few syndicate members find themselves in Europe, this is no surprise. Yet these are not our Nigerian Princes that have evolved, we need to look a bit South East to where we have unrest, the Cameroon. These parties have syndicated in a threat that’s equal to, if not greater than, their Nigerian counterparts. Even now we are seeing European companies spoofed, vehicle scams that are near indistinguishable from the traditional vehicle scams, fake European commodity scams with stolen European business registrations displayed as their own. Earlier this year a certain Spanish company bought seafood that never arrived. The commodity scam has taken hold in Europe and destroys businesses, the small mom and pop shops are extremely vulnerable. Of late the same drugs scams targeting the USA have been seen targeting Europe and Canada. We only need to read Steve Baker’s Better Business Bureau report on pet scams and arrests in the USA to get a peek of this hidden threat. Fake passports? Forged Euros? IETLS/TOEFL certificates? Visas? No problem. These parties massively abuse domains as the report shows. More so, social media and online classifieds are also abused. Once the fraud is established, online content is secondary. A working email that can’t be mitigated is vital – welcome email-only domain abuse.
What is ironical is how this group uses the one tolerant US registrar for their pet scams and vehicle scams, the other tolerant US registrar referred to in this report for their hard core drug scams and like. Couriers are distributed across the two. It’s no coincidence these correspond to the first and second highest fraud sponsoring registrars for long lived advance fee fraud domains recorded in 2017. ICANN is sitting on a time bomb.
No matter which way we spin these issues, this is systematic DNS abuse as these type of domains have no legitimate purpose in a legitimate DNS system. They only have one sole purpose, defrauding unwary consumers. Typically this fraud is illegal internationally, from (enter your favorite jurisdiction), to (enter your most hated jurisdiction). This begs the question: why this is tolerated? This fraud is also accompanied by all types of other human rights abuses. Law enforcement will not always engage for various reasons such as financial loss size, law enforcement goals, jurisdictional issues, local unrest (Cameroon?), under-reporting in law enforcement statistics, even political reasons etc. Many victims are left destitute and cannot afford a lawyer abroad. But then again, to what effect? To uncover garbage registration details the registrar will never be held accountable for while the miscreants abusing the DNS system get a fee pass?
Right now the GDPR has ironically also become a shield for bad actors abusing the DNS system claiming to be based in Europe. Some registrars do not tolerate these games and immediately stop such abuse. Well done to you, you know who you are. Likewise some savvy Registries have followed this route – kudos to you!
But then again other registrars are quite content accepting stolen money for more domains, quite willing to allow abuse of their proxies or even the GDPR for registrants rapidly changing names, continents and even gender multiple times per month. These registrars are sponsoring a part of hidden time bomb in ICANN; what will the European regulators do when they learn that their citizens are being defrauded and having their private details trivially leaked and distributed, while certain registrars self-blinded to this? What will they do when they see the details ICANN chose to ignore that is in conflict with publicly stated polices, the RAA verification claims even used in the public ICANN discussions on the GDPR? The current spirit of the GDPR does not live in the current policy enforcement at many registrars. Even some European registrars. A quick $10 is enough to sacrifice consumer rights. Yet consumers cannot enforce agreements between ICANN and registrars, but ultimately we can cry, and cry “foul” very loudly, when ICANN does not hold it’s accredited registrars accountable as per stated policies and consumer harm follows. That harm is affecting government, commerce and us mere mortals alike. Right now ICANN is sitting with a report showing how the Reserve Bank of India was spoofed countless times with impunity, using fake registration details for the past four years at least, while the one accredited registrar self blinded, something complained about twice. Other banks like RBS, Citi etc are spoofed. Perhaps Société Générale would not have wasted the time and money for another fruitless UDRP if somebody listened. Perhaps US lawyers, banks and companies would not have had their websites trivially stolen and republished behind bogus hiding pages to be sent to target victims, perhaps innocent US lawyers would not have had their faces plastered on these instruments of fraud propagated with abusive DNS records not worth a spit, perhaps there would have been a lot less victims in remote jurisdictions who thought they were dealing with a real company when applying for a job, or defrauded companies participating in a tender process. Indeed, in the one complaint we described how we literally saw an attack develop just after the domain was registered, changing from a spoof of a Canadian bank to phishing. This is the breeding ground for BEC. “Mike” was no surprise to us. Our data was used and mined in the lead up to the “Mike” investigations by savvy law enforcement.
While we reported the one registrar to ICANN again, also reporting the affiliated downstream reseller proxy at the same registrar, others exist. In the malicious domain data-set example used, the malicious actor registers his domains at two registrars. Did we also not report this second registrar’s lacking standards? Yes we did. Was this complaint not also similarly closed in 2016, with an American bank still being spoofed with equally fake registration details as now again? Why is the registrar now allowing malicious registrants to lie consistently about their identity when caught out spoofing banks with fake registration details? The owner of this registrar was quick to point out this is what ICANN told him to do. What can we say?
We chose the registrar in last weeks escalation, as they had the second highest incidence of advance fee fraud they decided to self blind to. One registrar chose to turn the .US registry into a trash can for scammers with the Registry idly standing by, allowing US consumers to be targeted in relatively low value fraud. They had a higher total fraud incidence. Yet the registrar described at the start allows the most dangerous domains into the DNS system. A fraud targeting a cancer victim in a drug scam followed by extortion, and finally leaving him destitute with his last cash stolen in a suicide drug scam, is and will always be the worst of the worst in human rights violations and despicable type of fraud. These victims will not come forward and silently slip into the night, giving up the fight. As such we attacked the most dangerous problem. But then the problem became even bigger when ICANN chose to overlook the obvious along with their own policies. Likewise other similar issues were swept under the carpet in the past. This madness has to stop.
To each and everyone discussing and deciding what to do with the event of the GDPR in the ICANN policy space:
Do not let theory of operation in your small sphere of the world dictate that you make bad decisions that will have massive ramifications in a distant part of the world, where human rights protection is not a priority, or be abused as an excuse to allow consumer harming practices. Unfortunately there is no security in the DNS without a way for independent parties to measure the effectiveness of a policy enforcement. There are poisoned apples in the DNS system and many upstream sponsors simply pass issues downstream if not ignoring them. Without accountability, everything becomes moot in Lala Land discussions with no real meaning.
This is also why we consider it vital for a full study be made of Advance Fee Fraud abuse in the DNS system by perhaps experts like ICANN SSAC. There is most certainly more than enough material available in DNS records. Government expert input should also be sought. Media reports are typically dramatic, never analyzing the problem from a DNS perspective. There is a consumer expectation that a bespoke domain name is a sign of trust; surely somebody checked. ICANN does require registrars do checks? Or not? The truth is many DNS custodian Registrars do not care – please pay $10 – perhaps as low as 79c discounted. Domain control is key at the SSL providers to obtaining SSL certificates and the green padlock lost all meaning, only perhaps meaning you may be defrauded securely. Let’s Encrypt considers Google Safe Browsing and Microsoft to be an indicator of a domains suitability for a SSL certificate to avoid phishing attacks and malware domains. Yet this mechanism does not acknowledge domain based advance fee fraud. Perhaps if a bank is spoofed, it will incorrectly get flagged as phishing (AFF is not phishing). If the fraudster has a bespoke bank or other fraudulent domain and website – the criminal is good to defraud securely, it’s not phishing as no brand is being impersonated. Anti-virus vendors have adopted this same distinct blindness for the mess that is advance fee fraud in the DNS system, this while advance fee fraud has steadily grown to a multi-billion dollar industry. This madness of annually increasing victim fraud statistics has to stop. Currently ICANN has a role to play if they accept realities – they need look no further than two reports and complaints which were escalated back to them, also making Mr Marby aware of the obvious problem. Don’t simply reject those as a matter of policy with weak excuses, read them – they have many clues and the exercise that was done is repeatable. Pass them on to the real experts if in doubt, not the nay-sayer excuse makers. There is a reason why the authorities took a good look at those details, took additional legal steps, but had to stand down – victim jurisdiction. It also shows why law enforcement makes for weak custodians of ICANN policies.
However that can be changed if the parties trivially having their content stolen choose to pursue the matter. Currently as many parties have a dog in this fight as the victims, at one with the common consumer, without them even knowing it. Government, commercial and casual user rights meet massively in this issue. It affects and undermines a healthy trusted internet for each and every person that has touched or will touch a keyboard or use some internet device to communicate. It affects everybody.