Avast highlights the failing in consumer protection
Sometimes we can learn a lot from what experts in their field of operation publish. Ironically we saw this yesterday again when Avast, a large anti-virus vendor, quoted an article by John Wasik on Forbes:
All online scams have one thing in common: They want to tap your greed to get at personal information they can steal. These “phishing” ruses are happening 24/7.
A typical banking scam will ask for information so the scammer can access anything from your credit cards to your checking account. Never reply to these emails.
What we learn here is how anti-virus vendors are failing consumers, using non-authoritative sources to blindly drive campaigns. We can understand why Advance Fee Fraud (AFF) is at an all time high. We can understand why BEC has grown to one of the top business facing threats. But does opportunity arise from this ill thought out post?
Let us first understand what was said an why the assumptions made are patently wrong.
All online scams have one thing in common: They want to tap your greed to get at personal information they can steal.
There are many online scams. Which person using the internet to shop, hunt for a bargain, has not come up against a fake shop or business? This shop will offer various goods, typically high value goods, at a slightly lower price than average market value, or scarce items hard to come by. Verification, in a due diligence attempt by the consumer, may well fail since business impersonation is rife on the web. It’s not uncommon to find the brand name of a known company reused, their address reused, sometimes even their company and tax numbers. As any real security expert will know, the SSL certificate is commonly abused to establish trust. A perfect consumer trap. Where would the greed be in purchasing from a shop like this, perhaps even resulting in the consumer getting his credit card details stolen? Artists Against 419 has been dealing with this issue for the longest of time. The Japan Cybercrime Control Center (JC3) and the Anti-Phishing Working Group (APWG) most recently also released a report on a vicious form of this type of fraud. This report also states:
Given this situation, JC3 has been providing APWG with the URLs of “Fake Stores”, however, only some APWG member companies adopt the URLs to display an alert on users’ PCs, because the “Fake Stores” don’t meet the APWG’s core phishing website criteria.
Therefore, in the near future, it is expected that APWG should establish a new definition of “Fake Store” as a harmful threat for users. It is also expected that more APWG member companies leverage the URLs of “Fake Stores” that JC3 has been providing to APWG, in order to use in their alerting systems to protect users from the threat of “Fake Stores”.
Why was it necessary for this to become a crisis if we have known about this risk since at least 2003? Why has this not been protected against at any AV vendor’s package claiming to be protecting the consumer? As the report states: ‘because the “Fake Stores” don’t meet the APWG’s core phishing website criteria’.
Another salient point the report makes is domain abuse:
Infrastructures including IP address and domains used for “Fake Stores” are characterized by the following points.
- Common IP addresses and email accounts are used for many domains used for “Fake Stores”.
- While criminal groups seem to get hundreds of domains at the same day, these domains are used for a month or a couple of weeks at shortest.
Ironically domain abuse has been one of the most devastating threats to consumers and to date, largely ignored. Domain abuse is acknowledged in other areas, but not in consumer facing fraud. Most recently all domain registrations became subject to GDPR provisions, hiding domain registration details. Consumers have to rely on other parties (who are failing them) to do proper checks on at least some basic level in terms of domain registration details supplied. Such is mandated in policies and published. Yet we find it’s not being done! These are not isolated cases either.
Taking this one step further at showing why greed is not a factor: one of the most dangerous consumer facing threats is the common fake courier and variations thereof, also the fake escrow. These fake sites may either be bespoke fake companies or impersonating real companies. They are most definitely not phishing either. While phishing normally uses spoofing as a tool for stealing details such as bank credentials etc, not all malicious spoofing is necessarily phishing (simply put: all cats are animals, all animals are not cats). They are not necessarily out to steal your personal details, rather your money. The clues have been around for the longest of time, which some the experts chose to not understand in an unforgivable lack and betrayal of consumer trust. Let us consider a spoof of DPD Couriers. DPD Couriers has for the longest time used mechanisms such as UDPRs to mitigate spoofs of themselves. Yet their name is now once again abused in vehicle escrow fraud as extremely well documented by Scam Survivors after a consumer was targeted. This posting most certainly shows the usage of malicious non-phishing websites many security experts will not even recognize, that of a fake dentist (previously Wikipedia was spoofed for this purpose). Any consumer trying to research this will be faced with a domain registered with Namecheap’s WhoisGuard proxy protection. A verification of an official business as suggested by the Berlin Group (emphasis in red that of the author) does not always hold true:
“7. Commercial data which may be disclosed must not include personal data.
While recognizing that commercial entities have less or no protection under data protection law than individuals, we recommend that ICANN acknowledges that commercial data may also include personal data. In its WHOIS-policies, ICANN should take into account that contact data from small business, sole contractors, home businesses and start-ups may be personal data. Secondly, ICANN should develop a procedure to distinguish between public contact data from companies and personal data from individual employees working for companies. The IWGDPT notes that businesses engaged in electronic commerce are likely to be regulated by national or regional law, in which case it is often mandatory for them to publish contact data on their website. This is not a role for ICANN or the WHOIS.“
This discounts business owners not having to list certain details on all websites internationally, nor brand owners like banks and other companies not retaining the main brand affinity, rather using product domains as marketing. A real company may register a domain for each of their products, market the product from distinct websites. This creates the ideal environment for fraudsters to add another (fake) domain and website. Studies have been done by the likes of ICANN SSAC showing how malicious domains preferred proxy protection. This was ignored to the detriment of the consumer.
Yet the Berlin Working group advice was also held out as an unofficial measure for the GDPR implementation in the ICANN Whois discussions with the European Article 29 Working Group. The adoptions of this into ICANN policy was a failure at many levels undermining consumer rights and privacy in the AFF field. Not once does the Berlin Working Group acknowledge the massive DNS abuse of AFF. Not once does one of the corporations/protection rights groups say anything regarding DNS abuse in AFF targeting consumers, unless mentioning consumer protection and phishing in terms of their own interests. The GDPR meant to protect the privacy of ordinary consumers has now been turned against ordinary consumers in AFF and we’re seeing this more regularly. ICANN is not willing to take up the AFF challenge this far and recognize this type of DNS abuse. Certain registrars have most certainly been long term mitigators, likewise some registries. Other registrars and registries chose to pass this off as outside their mandate and rather focus on business at all costs, even if it is with malicious registrants. Bullet proof DNS provision is a reality in AFF.
This is the background as to why a consumer is left with the impression they are dealing with a legitimate courier providing an escrow service to purchase a vehicle. A check on official government websites will show DPD Courier exists. Depending how users access the website, they may even encounter the little green padlock in SSL abuse. Surely it must be legitimate? It even passes the anti-virus package browser check. Yet this is not, they are dealing with yet another escrow fraud domain shielded by registrar Namecheap (extremely well known for allowing these types of abuses). Most anti-virus packages will gladly pass the consumer to this website, be happy that there is no consumer threat at this URL.
This type of escrow fraud has nothing to do with greed either (unless at scammer, and registrar and registry level for some). Nor phishing, it’s not the goal of the fraudster, any abused consumer details is incidental. Buying and selling is a normal part of commerce on the web. As such we need to ask, is it fair to go into a victim blaming exercises here, more specifically by a company claiming to be “Protecting your digital life”? It most certainly is not.
Such an escrow/courier may not spoof a real company either. Where does this leave the “advance fee fraud phishing” confused experts? Let’s consider another vehicle escrow scam template extremely prevalent and using Namecheap registered domains with their free blanket WhoisGuard protection they offer, currently also called trdcorporationvehicles[.]com:
![trdcorporationvehicles[.]com](https://blog.aa419.org/wp-content/uploads/2018/08/20180808_152934_oowv0fro1-615x1024.jpg)
We need to ask what threat value a (non-spoofing) fake courier has in fraud? Does it rely on greed to succeed? Last year Delta Airlines launched a John Doe lawsuit against pet scammers impersonating them. It took the likes of the US BBB and Mr Steve Baker to expose how prevalent pet scams were. Even so, the security community selling consumer protection products is fast asleep. Verifiable evidence is available to those caring to look, to discover how the same parties spoofing Delta Airlines, are using other non-spoofing couriers as well, once again in a thumb print a mile wide. Is it any shock to discover these same parties also target consumers in drug scams? Before adopting the druggie victim blaming tangent, consider laws exist under which certain substances may be purchased for good reason. This is how cancer patients are regularly targeted, then end up facing extortion. There is a reason the FDA and the DEA published alerts on spoofing and extortion. The incumbent registrar Namecheap chose to distance themselves from this fraud as only being a registrar. Their reseller in India closes tickets without responding. We have even recorded spoofs of the DEA trivially used in extortion! Most anti-virus protection packages are happy to accept these as safe in a false negative. Is any party going to the trouble of obtaining a legal medial certificate to purchase marijuana for legitimate purposes, that of seeking relief from the symptoms of cancer, now greedy? How is this phishing? This is not! Yet uninformed opinions abound and ignorance is bliss.

Another usage of the fake courier is sending packages used in the infamous romance scam linked “gift scam”. Victims to fictitious partners on places like Facebook are groomed and led to believe they are in a relationship with a real person. All types of problems arise, many of these ruses are using fake websites on bespoke domains our traditional security vendors do not even recognize; an energy/construction/avionics company, a fake petroleum company with a bespoke login panel where accounts are pre-populated with fake contractors with a million or two outstanding to them, no phishing involved. Likewise fictitious banks that may or may not impersonate a real bank’s brand, some using stolen bank websites with logos and names changed. Others are bespoke. Accounts are once again pre-populated with fictitious names and amounts, typically millions. Even the US Army is similarly spoofed, registered and hosted in Russia at a bulletproof registrar. The victim is shown these fake websites when the fictitious scamming partner needs to borrow a few thousand dollars as not being able to transact himself for some reason, or showing the monies outstanding to him yet to be paid. The scam relies on the goodwill and illusion he has spun in the mock relationship; he uses these instruments of fraud to convince the victim it’s okay to borrow money as he is good for it. In the process promises are made of marriage and other like romantic proposals. The fraudster sends a parcel to the victim via the fake courier – except we find there is a problem; custom fees, penalties and a myriad of other types of fraud. Where is the phishing in this? There is none. Where is the greed in this? There is none. We only see misplaced trust and caring, the very elements that makes us human. Is this worthy of victim blaming and shaming?
Media reports have been largely sensationalist on the this phenomena. Reporters want victims to tell their version of a story, but only if it fits into their pre-written script as related to them by parties which are not subject experts. Who makes better victims? The elderly as the media would like us believe? Or people in their twenties as others would have it? While they quote romance scams and military scams being at an all time high, the detailed underlying mechanisms of the fraud are not mentioned, it’s just another story to sell. Only on deeper investigation by real serious experts do we find how this all links to BEC and other similar AFF.
Such was a report earlier this year by serious players in the field, Agari, who did not follow the popular mantra of knowing it all, repeating myths of ill understood advice, rather researching: Behind the “From” Lines: Email Fraud on a Global Scale.
This report clearly mentions the link between AFF and BEC numerous times and is well worth the read, example:
Examination of the attackers’ activity shows that BEC scammers are involved in a whole host of other scams. Historically, these organized crime groups have engaged in romance scams, but more recently BEC attacks have emerged as a more lucrative and successful approach.
Even as these criminals have taken on more sophisticated attacks, they have continued romance scams. We believe there are two reasons for this. First, they provide steady cash flow to fund the criminal enterprise while it goes after larger prey. Second, they allow the gang to generate a continuous supply of new money mules who they depend on to retrieve their funds.
After an Australian citizen ended up being victim to a romance scam and an unwitting drug courier, she is now facing the death penalty. While Artists Against 419 most definitely does not condone drug trafficking, our sympathy goes out to this victim. There is little understanding at senior (and supposedly knowledgeable) levels as to the full nature of romance scams, how everything around such a victim is twisted and perverted on the net:
Exposto had said she went to Shanghai to meet a U.S. serviceman with whom she had an online romance, and had been asked to carry a bag full of clothes. She said she was unaware that the bag also contained drugs.
Another serious piece of research linking these human rights abuses and organized criminality, is a paper published by Crowdstrike. It mentions:
Black Axe gangs are involved in a multitude of organized crime ventures such as running prostitution rings, human trafficking, narcotics trafficking, grand theft, money laundering, and email fraud/cybercrime. These activities primarily take place in Nigeria, and they also are conducted by Black Axe members (known as Axemen) in Europe and North America.
Exposto was not phished. She was turned into an unwitting drug mule. Most likely victim blaming will be in abundance by the ignorant, some even being IT security experts. We have no doubt she even had an anti-virus package on whatever medium she used to communicate. Can we then really blame the Millions of older Aussies missing out over ‘fear’ of the internet? Who are the players to blame for these failures? Law enforcement? No, they are the garbage can we throw the victims to after they become victims, it’s easier making it somebody else problem while holding yourself blameless. At best law enforcement mitigates where failures in earlier protections occurred. How is this consumer protection?
Is it coincidental that BEC is now targeting consumers? Not really, understanding that BEC originates with AFF and these bad actors are forever expanding their net, sometimes returning to the target group where they obtained their training wheels.
It’s also no surprise to see Malaysia mentioned in the arrest report. One facilitating party in AFF who we will mention by name, Henry O Njemanze, massively facilitated romance scams in Malaysia. Using about a 100 websites, this party and the syndicate targeted about 15,000 (fifteen thousand) people at about a 60% success rate, the victims predominantly being in the Far East, young single mothers. Their sin was not greed or being victims to phishing. They were merely trying to use the internet to learn more about different cultures and make friends. However they were set upon by fraudsters like a pack of hyenas with fake profiles, then targeted. Well defined fake courier websites were used in systematic DNS abuse that started at domain reseller level for bespoke courier-like domains, to be published using reseller hosting facilities. In an audit, Henry’s domain account was found to be hundred percent fraudulent domains, apart from his company’s own domains, OBJAC International and Data Host. The incumbent upstream registrar took a dim view of this abuse and immediately terminated his facilities after substantiating the facts. Henry tried making two more comebacks at this registrar, but unsuccessfully. Henry then ran to Namecheap where he found registrar sanctuary. He is still welcome at his traditional hosting provider in Europe.

Despite many efforts at outreach via numerous channels, the Malaysian authorities have remained silent on this issue. Yet the existence of the Faker Makers was first documented, proven and immortalized in materials used for law enforcement training as far back as 2007, an issue Artists Against 419 and other groups easily discovered in 2003 and why Artists Against 419 exists today. Empires have been built upon this trade in fraud facilitation and it continues. Why? The diagram used in our article on this role player in advance fee fraud is essentially the same one created for the original materials at the time in 2007. Most recently the Crowdstrike report reiterated the cybercrime syndicate structure in an independent study:
These zones typically have a commander or crime boss referred to as an “Oga”.
In terms of eCrime, the Oga directs the scams and provides direction to his team. These teams are composed of spammers, catchers, and freelancers. Spammers acquire email lists and operate advanced mail systems. The catchers monitor the responses to the spam campaigns and make first contact with victims (known as a “magas”) in order to advance the scam. Freelancers perform additional duties such as assisting with romance scams, acquiring and developing infrastructure, and creating fake documents.
This tallies with the syndicate structure we described as far back as 2007, except the Faker Maker becomes the contractor in their description, but Crowdstrike’s description is not inaccurate either. In the past year, parties in India have been uncovered facilitating the propagation of fraudulent AFF websites and registration/hosting activities, both in the 419 and Cameroonian fraud spheres. What was at first thought to be a party from West Africa abusing a fake identity in the more traditional role, was later identified. This proved AFF was evolving and growing. These facilitators are an insider threat in domain reseller channel and at hosting providers, undermining the net. They make out not too shabby clients, supplementing registrar profits and account for much domain churn. Likewise in the hosting channel. It’s not uncommon to find vast infrastructures of fraudulent websites migrate between hosting accounts. It is understood why these actors are offered protection in plausible deniability excuses from the relevant providers. Money talks.
Palo Alto Networks Unit 42 also incidentally points of this hosting and domain abuse issue in their SILVERTERRIER: THE RISE OF NIGERIAN BUSINESS EMAIL COMPROMISE report. While this report focuses in the incidence of malware in BEC threats, we have already seen other consumer facing threats making out part of this landscape and is also mentioned in this most worthy report. In their study they mention:
Among the list of actors are those who pursue cybercrime as a full-time activity; those who provide enabling activities, such as web hosting or domain resale; and those who own a mix of legitimate and fraudulent domains. With the latter, we assess that many such actors view cybercrime as a means to supplement their legitimate income, as they most often maintain employment with organizations in the technology, education, media or music industries.
These observations tallies with our own, although in a different sphere of 419 operation. Any serious cyber security expert wishing to fast track on AFF and malware needs to read this report as well. It bears testimony to the fallacy dumb Nigerian Princes and dumb victims, where a supposed expert has collected a few scam emails, then deciding victim blaming is appropriate.
Europe has become the target of a growing number of loan scammers from Benin, West Africa. Even now we are mitigating a known bad actor once again. Increasingly we find victims to romance scams, or scammed businesses, having their private details leaked on AFF websites. In a period when the GDPR has has the predictable unintended consequences of being abused in AFF, cyber-criminals are forming coalitions. Yet the EU Foreign Affairs Council rejected attempts from Interpol in a consolidated approach at cybecrime:
The UN’s Group of Governmental Experts (UN GGE) tried mightily to convince governments that cooperation was the key to successful cyber-defense. However, that effort was rejected by the EU Foreign Affairs Council, which took issue with how national sovereignty applies in cyberspace, how aggressive a country can be in its cyber-defense strategy, and whether or not international humanitarian law applies to cyber-operations.
At this stage we’ll just leave it at how many human rights there are and the rights of one party may not be to the detriment of other parties, a foundation principle of humans rights norms. This ill fated decision and lack of real consumer voices at a time when it was most needed, is a massive failure in terms of protecting human rights.
Meanwhile general consumers are facing threats emanating from Nigeria which is largely unchecked (as has been confirmed by three parties the past few months, the last time last week) where Artists Against 419 deals with authorities and like. Despite continuous promises to clean up the mess from Nigeria, such efforts rapidly disappear into oblivion. Punishment is for the perpetrators without friends in high places or who don’t bribe officers. It no surprise to read this in the previously quoted SILVERTERRIER report:
For example, these actors take little to no care to remain anonymous. The credentials they use to register their malware infrastructure are easily associated with their public social media accounts on Google®, Facebook®, MySpace®, Instagram®, and various dating and blogging sites. Despite the passage of laws prohibiting fraud, scams and other illicit activity, the culture in Nigeria remains permissive of cybercrime, and widespread enforcement of the laws has yet to be observed.
Yet the grandstanding abounds. Most recently researchers discounted the value of WHOIS details prior to trying to implement sanity into the GDPR-WHOIS discussions. Is it no coincidence that AFF and hard drugs keep on cropping up emanating from the same circles, or that victims are used as drug mules, just as we see in BEC and AFF mules. To these predators, the victim is no more than a commodity item to be used and abused and pimped out for personal profit. Who is protecting the consumer? Where are the human rights in this? Yet the experts in privacy chose to ignore this, further undermining basic human rights even as this was written. It’s grossly unfair to embark on victim shaming against this background, more so if perpetuated by a company claiming to protect the consumer.
What Advance Fee Fraud is not, phishing!
A tip straight from the trenches: any party mentioning Artists Against 419 fighting phishing, or confusing phishing and AFF, is no expert. Leave and do something more constructive. Your time can be better spent feeding ducks while sipping a beer or a cup of coffee. Phishing and advance fee fraud are two separate threats. We escalate phishing to other parties that are experts in their fields. While a member or two may be involved in some other activities in the phishing sphere, having mitigated and assisted in those fields, the focus of Artists Against 419 is Advance Fee Fraud, not phishing. Ironically we find numerous supposedly authoritative peer reviewed studies describing us fighting phishing. Once such was found using this misguided understanding of the threats to criticize why it’s dangerous doing what we do, fighting phishing the way we do. Peace sister …
Generally phishing is impersonating a party to obtain credentials or other details the victim has, to then abuse it further, typically impersonating them. The idea is stealing information for abuse under false pretenses. We might see this where malicious actors send victims an email, pretending to be from the victim’s bank. They may further lure the victim to a website where the victim finds a copy of his bank. The victims enters his details and his credentials are stolen. This is a massive problem for banks where these criminals empty the victims account, leading to much distrust. Huge campaigns and efforts take place on various levels to protect against this. We only need to think of the APWG, NetCraft, Phishcops etc.
But what if a bank is spoofed, where a bespoke crude accounting system is bolted on, loaded with accounts and fictitious amounts? This is called flashing in 419 spheres. No credentials are asked of the victim. Instead the victim is given the credentials, or that of a fictitious partner (as mentioned earlier). In essence this spoof is not a phish, although still a spoof. This bank may equally be a bank with content stolen from a real bank, but with name and logo changed. It may even be a totally bespoke bank. Likewise a bespoke synthetic fake bank template may suddenly be called Bank of America. While the name of a real bank is used and perhaps commercial rights are abused, this is secondary to the primary 419 goal where consumers are the primary target and not the brand abused. This has been described in an article called Phishing sites vs Fake 419 Banks we published in an educational attempt. Much research matter exists to back that up. It’s not uncommon though, to see exposed 419 domains that have outlived the usefulness, abused in BEC-like phishing attacks, but that is not their main purpose. Consider yourself using a key to open up a box – the key is merely a tool that can be used for the purpose, although it has a different primary purpose.
Typically phishing happens on a compromised website, unlike the AFF domains and websites we list. AFF happens where the malicious actor registers the domain, populates it with content, having full control of this domain at all levels and can trivially abuse it, making any host based mitigation moot. A typical cure for phishing would be contacting the website owner or hosting provider, a vulnerability is fixed and the threat is cured. Phishing domains are also sometimes registered domains. Likewise a compromised website may be used for AFF, although this is extremely rare. Artists Against 419 does not list breached hosting accounts which are abused for AFF, we rather follow phishing mitigation techniques. The only exception was one breached website where the owner did not have time to fix the issue as was continuously promised for more than two years. At this stage we decided the owner clearly did not care and was no longer a victim to this fraud, rather perpetuating AFF through inaction. The website was listed and the upstream registrar and hoster was contacted with a long and full report on the events. The domain was suspended. Each rule has exceptions and a full understanding and situational awareness is required to evaluate what is being seen. Much fallacy exists in the AFF field.
Just as with a fake bank, any sector of the commerce can be spoofed or imitated. Conventional cures exists for copyright and trademark breaches, yet these are incidental in AFF. The fictitious bank is as dangerous as any other AFF website. We have discussed fake couriers. What about a fake lawyer website? Who needs a (fake) lawyer to look at his best worst interests? Consider the fake lawyer website Al Fatah Law Firm mitigated at hosting level, while the abuse starts off at DNS level: https://db.aa419.org/fakebanksview.php?key=93735. Yet conventional wisdom blindly subscribed to, would have this to be content issues as dictated by experts that never made a study of AFF. Such wisdom saw this website rehosted 27 times. Surely a website active for 4 years must be legitimate? Knowledge based intervention saw this domain being correctly reported and suspended. This was never was a hosting issue to start of with.
Ironically, many AFF websites are accidentally listed as phishing – accidental consumer protection under the phishing banner. While it’s tempting to use an easy phishing excuse to mitigate certain threats, it undermines understanding of the real threat and other associated threats and risks associated with AFF.
Mitigating at hosting level for traditional AFF is akin to putting a bucket under a leaky roof. Rather fix the roof or be doomed to be forever emptying the bucket, while the surrounding roof trusses silently rot. The consumer’s roof trusses are silently rotting, along with his security. So do we blame the victim when conventional wisdom is not knowledge based and quite frankly lazy, an exercise in passing the buck? “Make it somebody else’s problem, not mine” is all too easy. Do we want to chase shiny things like profit, selling to consumers claiming to be protecting their privacy, but not really protecting them, or taking time to understand their distinct threat landscape? Is this aimed at certain anti-virus vendors? Or perhaps certain registrars? It’s all to easy hiring an actor and scriptwriter to publish articles on security and make a total mess, as we saw a while back at a certain registrar. Just act it out. It would have been comical if it was not such a serious issue.
Once again we will explain the threat landscape the common consumer faces.
Governments spend billions annually in cyber protection. They hire/poach the brightest minds. Law enforcement is there to protect breaches of the laws. They have the legal system on their side. Yet they fail from time to time and we read about those in sensationalist news articles. Yes, sometimes they are stupid in the things they do in hindsight. But then again bashing any party failing at cyber security has also become extremely popular in both the media and at the hands of other security actors.
Commerce has even a greater set of threats and protection. Equally large budgets running into billions of dollars are available to this sector, budgeted for and spent. Once again top security sector actors are employed. Brilliant legal minds are hired to protect them. The security sector is also at their beck and call for a slice of the action in a self fueling market. Yet they fail. Once again the media and the other security actors are around to laugh, use it as an excuse to peddle more of their wares and services.
Meanwhile back at the ranch, Average Joe or Plain Jane who is the average family member each of us has, simply wants to watch a movie on Youtube, or perhaps spend some time with a Facebook friend or even check up on their bank balance. His or her protection? An anti-virus package. In many parts of the world they can hardly afford the bandwidth associated with the regular updates. The results are quite predictable. What chance does the average consumer have of staying safe where government and corporate networks fail, potentially facing the same malicious actors and threats?
Well done to those kicking this party, the consumer, the least protected and the most vulnerable player on the net. Your right of existence disappears if he disappears. But let’s bully, blame and shame them. There – job done, now you feel clever and self important, you’ve shown up stupidity and greed.
To each and every one involved in this sick syndrome, let’s hope your physician does not adopt the same attitude in your time of need when you may inadvertently skip a traffic sign or somebody else does. Did you not see it coming? Is it your stupidity and need to be in a rush that will be used to write you off?
A sad fact from the trenches: Many victims to AFF are people in the health care profession, slightly disproportionately high enough as to be noticeable. Their real sin is that they could not believe that any party could be as malicious as the one they met, could be allowed to flourish on the net by those responsible for due care in business. In turn the very care givers, who may have wanted to assist a stranger, got defrauded. A such this example is extremely appropriate.
The reality check:
The common user may see commercial threats, targeting his bank account or like – phishing. Anti-virus packages may protect him from this threat. This is the threat where commerce and consumer have overlapping interests, creating much awareness and subsidizing a secondary industry in consumer protection and education.
The average consumer faces threats where parties spoof the likes of the government in tax scams. Government engages, alrts goes out via government agencies and anti-virus packages blacklist. People are arrested.
How many antivirus vendors will blacklist pmkpaperline[.]com selling paper? Or petspom[.]us? How many security experts even know they are part of the same set of scams? How many know or have heard of the Cameroonian threat and scams, or the difference between them and 419 scams? Anything from fictitious pets to combine harvesters are sold (even a refurbished manufacturing plant once), accompanied by massive SEO and social media abuse. Another specialty they have is their ability to spoof real company registrations in forged documents. As such the Berlin Group’s advice was ill timed. They also love imitating other successful online scams with twists.
Let’s just look at the scale of the operations of the owner of petspom[.]us:
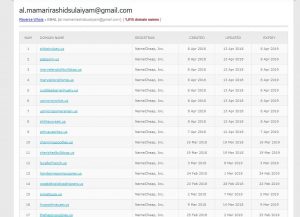
1015 domains!? With registration details like
Registrant Name: Morgan Lorga
Registrant Organization: Anonymouse Host
Registrant Street: Down street Rus
Registrant Street:
Registrant Street:
Registrant City: welmshi
Registrant State/Province: North West
Registrant Postal Code: 101000
Registrant Country: RU
Registrant Phone: +7.675552377
Registrant Phone Ext:
Registrant Fax:
Registrant Fax Ext:
Registrant Email: al.mamarirashidsulaiyam(at)gmail.com
Registrant Application Purpose: P1
Registrant Nexus Category: C11
Compliance experts Neustar do not care to listen and learn, yet they are experts running this registry for the NTIA. In a previous incident they took three months to investigate a similar party, ended up allowing it despite the non-compliant category and nexus as well as fake details. They were made aware of the above registrant, also that this issue was prevalent at this registrar. Why is the incumbent registrar given free reign to profit accepting any junk into the registry, undermining and defrauding US consumers? This is not a commercial threat and all is good, or is it? Will an anti-virus package says pass? Are consumers stupid and greedy if they wish to buy a dog?
Another irony is that so many fraudulent domains were allowed into the .US registry, that it has become impossible to monitor the status of all the threats in this registry. Artists Against 419 does a distributed weekly check on each domain abused in fraud during it’s entire life cycle until it finally expires, with a pause between each check, to avoid being seen as abusive in terms of resource hogging. Yet we regularly are seen by Neustar as abusive and denied access with too many lookups. Considering this registry is a thick registry, there is no way to see if the domain is in a clienthold, serverhold, redemption period or pendingdelete status, without obtaining all the data. We are most certainly not trying to steal data and Neustar has no other mechanisms available that allows for safe verifiable access (as was queried). A special process had to be created to recheck all the failures at Neustar. Surely any serious player in this field would accept there is such a thing as domain abuse, not self blind to a span of P1/C11 domain registrations (violating policy) from the Cameroon and Russia all abused in the well documented pet scams mentioned before that was demonstrated in the US BBB report. Whose security is Neustar protecting? Miscreants abroad with ever changing fake registrations details, or their fellow US citizens that are the target to these frauds? It’s not as if ICANN SSAC has not mentioned the problem in SSAC101 of overzealous limiting. So this is a known problem affecting security. While it has to be verified, it appears that too many checks on .US domains also see checks on .BIZ domains impacted. We are recording failures on the odd unpopular .BIZ domains after encountering .US lookup failures. We have requested that our access issue and the inordinate number of non-compliant .US domains be looked at by Neustar Legal. Downstream registrar Namecheap was not willing to do so. No response was ever received. This economic interest overrides consumer interest and rights.
What about evergreenfedbnk[.]us?

Who said “Hold on, but that is phishing”? Wrong – it’s not, it’s 419 fraud. However many anti-virus vendors will use incorrect classifications to protect consumers by accident, further led astray by expert classifications. Of note is the registration details?
Registrant Name: Rae D. Garcia
Registrant Organization: Elek-Tek
Registrant Street: 22 Trehafod Road
Registrant City: BUCKFASTLEIGH
Registrant State/Province: London
Registrant Postal Code: TQ11 1WU
Registrant Country: GB
Registrant Phone: +47.0785640
Registrant Phone Ext:
Registrant Fax: +1.5555555555
Registrant Fax Ext:
Registrant Email: s.mark8080@gmail.com
Registrant Application Purpose: P1
Registrant Nexus Category: C11
Luckily dhxcourier[.]us is safe for consumers says the experts … except it’s not. The .US registry allows us to see what passed for registration details at certain registrars. These experts are not keeping consumers safe. Domain edexexpresscourier[.]com may have a familiar name – perhaps missing an F – active and scamming since 2015 and host hopping. The logo may also ring a bell for some, even if not quite for others … yes, it’s an adapted USPS Logo:

Is this now suddenly a copyright issue and that alone, or part of a bigger threat? Likewise the domain name dhxcourier[.]us may sound somewhat familiar. Anybody noticing patterns? Will it be an invasion of privacy looking at (fake) registration details? If this does bother you (as the privacy experts are now telling consumers and not allowing themselves to protect themselves using WHOIS and actively not allowing it in many TLDs), it’s the same party all along. WHOIS failing, failing the consumer?
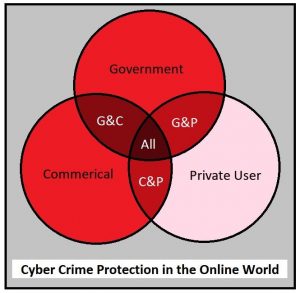
More importantly, which anti-virus package is protecting consumers from these? The NTIA appointed experts and some of their downstream registrars most certainly did not. We are now in a blind spot for most commercial protection packages. The consumer is on his own as there is no overlapping governmental or commercial threat interest. He cannot claim any protections in terms of domain policy.
We can illustrate the protection landscape as three overlapping circles, the darkness of the red indicating the threat protection. The private consumer’s protection is mostly by accident in threat identification, rather than by design, in the non-overlapping areas.
The irony is a lesser know products is. At the risk of sounding like marketing, which we aren’t, it’s worth mentioning the name of a long term acquaintance in the AFF war arena.
Users are free to install the Web Of Trust (MyWOT) browser plugin as 140,000,000 other users did, which will block such known websites.
MyWoT became friends in the 2010 Heihachi/Fake Shopkeeper gang wars which even saw the likes of SpamHaus attacked via DDoS. Just as Artists Against 419 was. This was never an issue to the domain experts which gave these criminals sanctuary. These were criminals that were tried and convicted, as such we can call them criminals. Yet never an eyelid was batted in the registrar community that gave to one of the biggest consumer facing frauds at the time the tools to commit their fraud. This only became an issue when the attacks shifted from consumer to PostBank. MyWoT led the initiative in flagging malicious domains during that time. A shout out to them.
It’s sad that JWSpamSpy is no longer available. Joe is one of the real experts in the AFF war, still posting at https://419scam.org/ and silently doing his thing.
How can any provider claim to be protecting consumers if they are protecting against phishing and malware, but not other threats? Any such provider has supplied the consumer with an umbrella where half the panels missing in the midst of an electrical thunder shower, giving them a false sense of security.
Considering all the research that has already been done in the field of AFF, there is no reason to adopt a blindness to this threat. Artificial Intelligence can be implemented. Other legal methods exist of threat identification and mitigation. We are not adverse to sharing our work, knowledge or advice if it will lead to consumer protection. We regularly partner not only with other consumer protection facing partners, but also other brand protection agencies. Does that sound wrong? Not really upon considering our select set of fraudsters we deal with, regularly impersonate brands to confuse and deceive consumers. We were the ones to alert a certain bank in France, just as they launched a UDRP for the second time in as many years to mitigate a party spoofing them, that he had just registered a third spoof. Once again traditional wisdom and policy had failed at many levels and the result was predictable based on open source intelligence gained. It’s not uncommon to see phishing excuses used by WIPO approved lawyers in pure AFF threats, thereby winning the right for their clients to take over a malicious domain; the right results for all the wrong reasons. It’s not uncommon to see phishing style take-downs on malicious domains, to only have them change to email-only threats (keep your enemy in sight). Similarly we see content hidden on sub-domains or on sub-directories where targets are given URLs. This is also an open invitation to any provable rights holder or their agents to obtain a report from us on anything we list, be it to mitigate or litigate: we have records of serial abuse and fraud attempts on many of these malicious actors, even if not always their (real) names. One party has over 1600 records in our database and going strong.
An example of the details for a report is shown below with details redacted for obvious purposes.

The report includes snapshots with metadata embedded showing the date and URL address when it was made, also shown at the top of each snap.
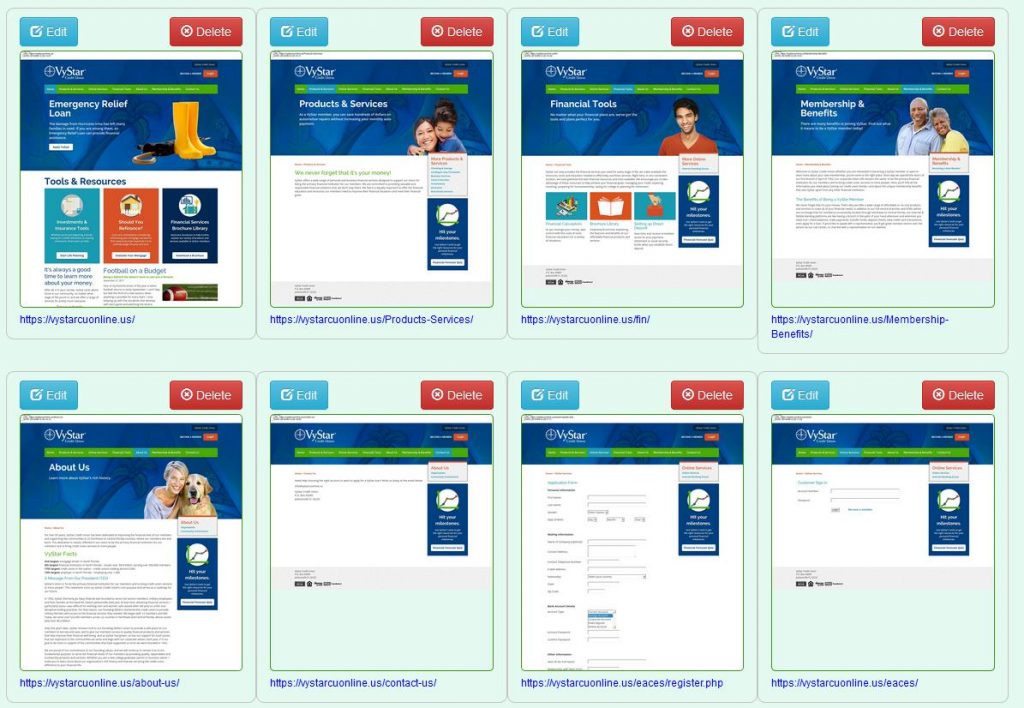
Detailed first snap:
Conclusion
The eagle eyed may have noticed we switch between AFF (Advance Fee Fraud) and 419. AFF is a vast set of consumer threats. We specifically focus on vehicle and mule scams emanating from Eastern Europe, 419 scams from West Africa and Cameroonian Scams. Each of these three sets makes up a further family of complex threats the average consumer is ill equipped to deal with and no proactive protection is available. While generic advice is given in the broadest sense of references in the media, the reports do not indicate the real danger flags. Commercial and like threats shown make up many of the warnings the consumer is hounded with, desensitizing them to lesser known yet equally serious threats rarely reported on in a knowledge driven way. The consumer needs and deserves our understanding and protection. We can show the expectation of basic checks done at registry level is not met despite promises and marketing, yet something a consumer expects is done in any sane world where a registry is mentioned. Disparate laws further undermines the consumer rights. While it may be problematic understanding the madness that is consumer supplied information, rather gear up develop systems that can be used to create an early alert system in a feedback loop that also protects consumers while also protecting self interests in a fair win-win situation. Do not make the consumer a mere product to be profited from. These are the real people. We are willing to assist in our relevant field of expertise. We are not even asking formal recognition. But let us rather work together to give the average consumer a better deal.
Subscription fee: An honest desire to protect consumers, people who may be your sister, brother, friend, daughter, granny … the small mom and pop shop … perhaps a bit too naive, trusting marketing experts and opinions, not IT security experts. People getting a raw deal. These are the people driving the real internet. We promised them a better deal in the 90’s, let’s deliver on it.
Thank you to the parties that already use our data!
Edit:
Since posting this, other parties have responded, sharing news articles. They are well worth reading, proving exactly the consumer dilemma and dangers mentioned above. Most do not mention the associated domains and websites used, although this is a well known fact.
https://www.mamamia.com.au/online-romance-scam-sharon-armstrong/
“All these people sit back in some form of judgement, instead of actually thinking, ‘My God, that could be my mother, it could be my sister, it could be my daughter, my uncle, my brother, my father, my grandfather, my best friend’,” she said.
“There are people out there whose sole intent in turning up to work every day is to extort someone in some way, be it emotionally, be it financially, be it by making them an unwitting drug mule. But [trolls] are not focusing on that; they’re blaming the ‘dumb, stupid’ victims.”
The FBI and Secret Service say they don’t have the resources to investigate all of the reports.
https://theconversation.com/why-we-need-to-do-more-for-the-victims-of-online-fraud-and-scams-59670
Or imagine if your partner was approached with an investment opportunity. They do their research, do “due diligence”, and it seems to check out. There are glossy brochures, a website of testimonials, and an array of staff to whom they speak on a regular basis.
So they invest thousands of dollars and are able to log in to an account to track the progress of their investment. But one day the website disappears – along with all of your combined savings.
https://www.journalducameroun.com/en/two-cameroonians-arrested-india-online-fraud/
The men are accused of making fake websites of various companies to cheat people through online shopping, providing customers with fake license and documents of the product.
Edit2:
Global drug trafficking operation run out of Villawood detention centre, phone taps reveal
Global drug trafficking operation run out of Villawood detention centre, phone taps reveal
This article does some real deep diving into the phenomenon of online fraud linked to romance scams with the victims being turned into money and drug mules. Currently no anti-virus will protect you from these scams.
See if you can spot the black money scam abused. That is the ‘SSD Solution’, ‘Red Mercury’, ‘Vectrol Paste’ etc, commonly seen in scam websites that does not exist, but a search engine will make you believe does.